Selecting the right AI-powered Security Operations Center (SOC) solution is no longer just about comparing feature lists. It’s about determining whether a platform (and the team behind it) can truly elevate your organization’s security capabilities, streamline analyst workflows, and adapt alongside an ever-evolving threat landscape. The following question set is designed as a comprehensive evaluation guide, helping you probe the technical depth, operational maturity, and business alignment of any AI SOC initiative you’re considering.
Every vendor is presenting their own “ultimate guide” to evaluating AI SOC solutions. We recognize this can make it difficult to cut through the noise. That’s why we’ve worked hard to make this guide as unbiased and universally useful as possible, grounded in real operational needs, no matter which platform you’re considering.
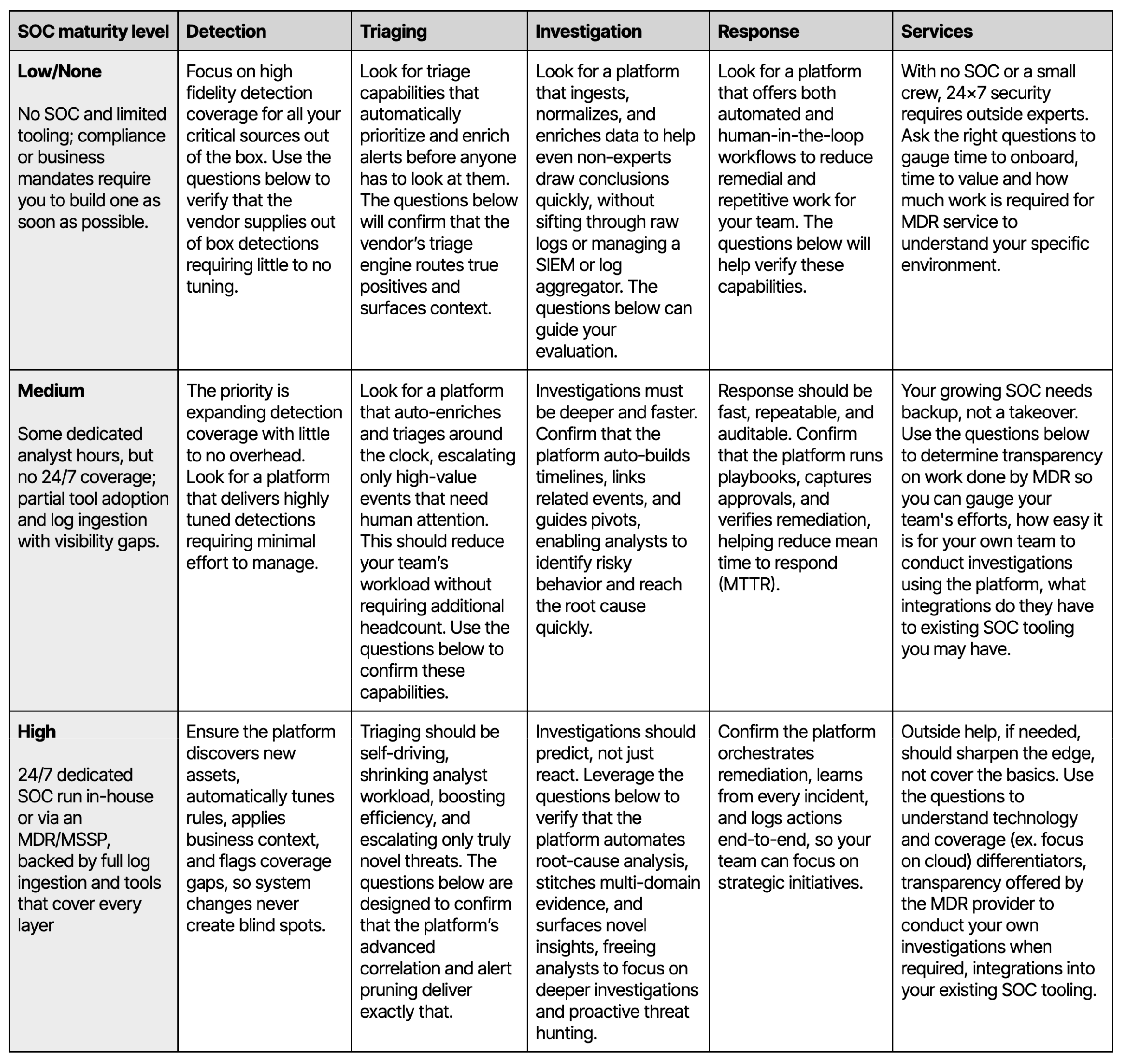
Use the questions in this guide to reveal how different solutions deliver on detection accuracy, automation, and managed-service quality. Whether you’re building a SOC from scratch, tuning a mature program, or vetting an MDR partner, this framework exposes strengths and gaps that matter to your risk profile. Let your current maturity level set the bar: the table below maps that maturity to the way you should use the questions for each section for every phase of the SOC lifecycle.
Detection
- Can the AI SOC tool generate its own, accurate detections that stand alone or augment ingested SIEM findings?
- Does the platform allow you to create custom detections?
- Does the system triage its detections with context specific to your environment to increase the fidelity of detections?
- Can the system create detections from the investigations you are performing?
- Can the system extract Indicators of Compromise (IOCs) and create detections from reading about known exploits?
- Does the platform require extensive customization and tuning, or can it automatically learn and adapt to my organization’s unique environment, behavior patterns, and business context?
- Does the platform provide end-to-end coverage across Tier 1 to Tier 3 analyst workflows to minimize handoff issues and preserve investigation context throughout the incident lifecycle?
Triaging
- How does the platform incorporate business-specific context (e.g., asset criticality, user behavior, environment) to assign severity, prioritize alerts, and reduce false positives?
- How does the platform automate triage, alert routing, and response based on severity and context?
- Can the system include user feedback, if applicable, when triaging an issue?
- Does the system learn from past triaged alerts to improve future outcomes? If so, what information does it factor into for past analysis?
- Can I clearly see the rationale behind AI-driven decisions and access a full audit trail of actions, such as marking a finding as a false positive, for accountability and review?
- Does the platform map its detections to the MITRE ATT&CK framework, and how is this presented to accelerate understanding and response?
- Does the platform support conversational interaction during and after triage, allowing analysts to ask follow-up questions and retrieve insights in natural language?
- Can the system correlate multiple alerts across other data sources as part of the triage process to determine a wider-scale impact?
- What is the Mean Time to Investigate (MTT) for the agent. Consider MTTI as the time interval between alert ingestion and a recommendation/disposition from the system on the alert.
Investigation
- Does the system perform out-of-the-box parsing, normalization, deduplication, and enrichment of data, making it easier for analysts to understand, navigate, and investigate alerts effectively?
- Does the platform provide meaningful context and explanations that go beyond what a typical analyst would already know, such as connected identities, chronologically close events across systems, threat intelligence enrichment on IPs, effectively educating users about alerts, tools, and behaviors involved?
- Does the platform apply advanced analysis techniques such as baselining, identity resolution, and risk scoring to help prioritize alerts and surface meaningful patterns across users, assets, and behaviors?
- To what extent can analysts complete investigations within the platform, and how often do they need to pivot to external tools or data sources?
- Does the platform provide clear, contextual summaries of alerts and events, including rationale, risk level, and enriched indicators, to aid investigations and educate analysts beyond standard details?
- Does the platform allow for seamless investigative pivots from an initial finding, enabling deeper exploration through follow-up questions and queries?
- Does the platform support flexible investigative workflows, including hypothesis-driven threat hunting and insider threat analysis?
- Does the platform support real-time collaboration between analysts and AI agents, including shared workspaces, notes, and timelines to document investigations and findings?
Response
- Can the platform trigger automated, no-code response workflows, like resetting MFA or disabling sessions, based on alert severity and business context?
- Does the system require building static playbooks, or can you describe to the system, in a prompt, what actions need to be performed under what circumstances?
- Does the solution support human-in-the-loop decision-making, with flexible business rules that determine when to involve users, managers, or analysts in response?
- Can the platform prioritize and execute response actions based on contextual risk scores, taking into account user identity, asset exposure, and behavioral anomalies?
- Does the platform provide a real-time, multi-user Command Center to coordinate response efforts across SOC, IT, and other teams, with full timeline, notes, and next steps?
- Does the system integrate with existing SOAR technology to leverage existing response workflows?
Services (if choosing an MDR service)
- How does your provider integrate with your data sources? Is it API based integration?
- Does your MDR require you to have a SIEM for log aggregation and auditability?
- What is the time to value? From onboarding to when you start noticing the MDR provider understands your environment and provides high fidelity escalations.
- Do I have 24/7 access to the underlying platform for visibility, investigation, and collaboration, even outside of MDR interactions?
- What integrations does the MDR provider have with existing SOC tooling: SIEM, SOAR?
- Does the provider offer true 24/7 managed detection and response (MDR) services, including continuous monitoring, triage, and escalation?
- Does the team include security experts with deep experience across IaaS, SaaS, and modern infrastructure environments?
- What is the expected responsiveness of the MDR or support team for questions, escalations, or incident handling, and is this backed by SLAs?
- Are regular check-ins or service reviews part of the engagement to ensure alignment, improvement, and evolving threat coverage?
Architecture and Deployment
- Is the solution offered as a SaaS deployment model to simplify operations and ensure predictable costs?
- Does the platform support single tenancy, the ability to deploy in your cloud, and data sovereignty to ensure data isolation, meet compliance requirements, and maintain control over where data is stored and processed?
- Does the platform support multi-level organizational hierarchies and granular role-based access control (RBAC) to effectively manage MSP environments and complex enterprise structures with multiple business units?
- Does the platform meet your required compliance standards, such as SOC 2, ISO 27001, GDPR, or HIPAA, and can it provide documentation or certifications to verify compliance?
- If I share data with the platform, is that data used to train underlying models, and what safeguards are in place to prevent unintended exposure or misuse?
- What mechanisms and safeguards are in place to ensure the platform consistently delivers deterministic and accurate results?
- How effectively does the platform present key operational metrics, such as MTTI, MTTR, and MTTC, in a clear and actionable way for tracking SOC performance?
- What is the typical time from onboarding to when the platform begins generating reliable, actionable alerts, including any necessary learning or tuning period?
Onboarding and setup
- Does the platform offer API based integrations into your data sources?
- Can the platform ingest and process data at the volume and velocity required to match the scale of your environment, especially your IaaS and SaaS logs, without performance degradation?
- Does the platform offer native integrations with key security and IT systems, beyond just SIEMs, including identity providers, IaaS, SaaS, endpoint, email, SASE, and threat intelligence feeds, to provide unified visibility and context?
- How long does it take the system to establish baselines on known good behavior in the environment?
- What kind of support services are offered, and do they include experienced personnel and clearly defined SLAs to ensure timely and effective assistance?
- How involved and collaborative is the team during onboarding? Do they actively guide setup, data source integration, and platform tuning?
Finding the right AI platform for your SOC
Choosing an AI-driven SOC platform is a strategic decision that will shape your security operations. Armed with the questions in this guide, you can cut through buzzwords, validate real-world capabilities, and hold platforms accountable for measurable outcomes, whether it’s reduced MTTR, lower false-positive rates, or demonstrable cost savings. As you compare responses, look for consistency between the platform’s stated features, the support team’s processes, and evidence from proofs of concept.
Ultimately, the right partner will meet your technical requirements today while demonstrating a clear roadmap for tomorrow’s threats and architectures. Prioritize solutions that combine strong native detection with transparent AI reasoning, seamless analyst workflows, and, if you need it, collaborative MDR expertise. When those elements align with your business goals and risk profile, you’ll have the confidence that your SOC is ready not just to keep pace with attackers, but to stay a step ahead.






