Amid the flood of alerts and data, SOC teams often discover that speed without the right metrics is just chaos at scale. In this blog, we’ll explore how to measure what truly drives efficiency, reduces risk, and empowers the transition toward an AI SOC, recognizing that while the destination is an autonomous SOC, most organizations are still on the journey to get started with AI in the SOC.
For SOC leaders, CISOs, and AI SOC analysts, the right metrics are the difference between detecting threats in time and missing critical signals.
Why SOC metrics and KPIs matter
Metrics and KPIs are the foundation for:
- Operational visibility: Understanding workload, detection quality, and response times.
- Strategic alignment: Connecting SOC effectiveness to business and risk management goals.
- Continuous improvement: Identifying bottlenecks, inefficiencies, and automation opportunities.
As SOCs evolve toward AI-driven workflows and complete automation, having the right measurements is crucial for guiding investment and benchmarking AI SOC tools and team performance.
Core SOC metrics every team should track
1. Mean Time to Detect (MTTD)
- What it measures: How long it takes from the onset of an incident until it’s detected.
- Why it matters: A shorter MTTD reduces attacker dwell time and potential damage.
- AI SOC connection: AI SOC analysts increasingly rely on anomaly detection and behavioral models to cut detection time drastically.
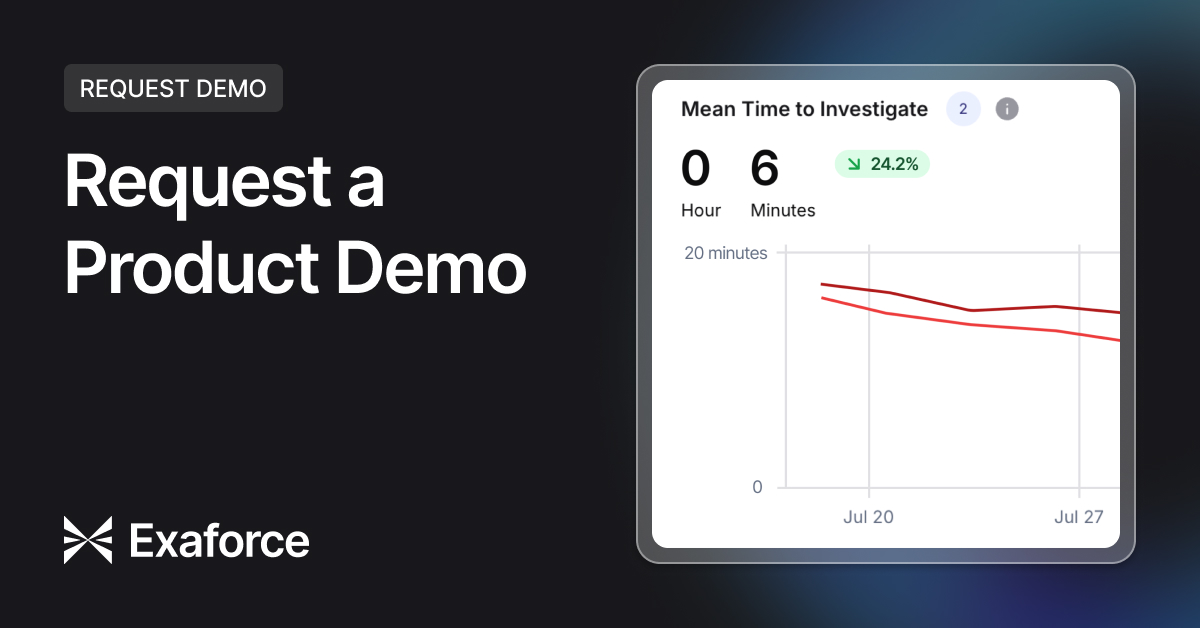
2. Mean Time to Investigate (MTTI)
- What it measures: Time taken to validate an alert and determine if it’s a true incident.
- Why it matters: Analysts often spend a large portion of their time gathering context. Streamlining investigation shortens the path to action.
- AI SOC connection: With automated SOC workflows, AI agents triage alerts and enrich context instantly.
3. Mean Time to Contain (MTTC)
- What it measures: Time required to contain or stop the spread of an incident after confirmation.
- Why it matters: Fast containment limits lateral movement and impact.
- AI SOC connection: AI SOC platforms automate isolation of hosts, user lockouts, or policy enforcement, reducing MTTC.
4. Mean Time to Resolve (MTTR)
- What it measures: Time it takes to fully remediate an incident.
- Why it matters: Longer resolution means prolonged exposure.
- AI SOC connection: AI SOC analysts equipped with automation can accelerate root cause analysis and recovery steps.
5. Alert Volume
- What it measures: The number of alerts generated by SOC tools within a given timeframe.
- Why it matters: High alert volume without prioritization overwhelms analysts and creates alert fatigue.
- AI SOC connection: AI SOCs automatically triage alerts, reducing false positives and correlating across domains, while collapsing redundant signals into single, high-fidelity findings.
6. False Positive Rate
- What it measures: The percentage of alerts that turn out not to be true incidents.
- Why it matters: Most alerts from legacy systems are false positives, wasting analyst time.
- AI SOC connection: Automated SOCs leverage additional context beyond the alert, continuously retrain triaging models, and leverage business context rules to minimize false positives.
7. Anomalous Safe Rate (ASR)
- What it measures: The percentage of anomalous events flagged by detection models that are later deemed benign (“safe”).
- Why it matters: A high ASR indicates detection engines are too sensitive, producing noise that drains analyst time and erodes trust in automation.
- AI SOC connection: AI SOC platforms optimize ASR by continuously learning from analyst feedback and historical safe anomalies, striking the right balance between sensitivity and precision.
The shift toward an autonomous SOC
Traditional SOCs rely heavily on manual triage and investigation. But as organizations embrace AI SOC solutions, the metrics evolve:
- Speed metrics (MTTD, MTTC) give way to automation-first KPIs like the percentage of incidents autonomously resolved.
- Workload distribution metrics shift toward measuring how much time AI SOC analysts spend on strategic analysis vs. repetitive tasks.
Building metrics into your SOC strategy
Step 1: Define success
Decide whether your SOC’s mission prioritizes speed, coverage, cost reduction, or resilience. Metrics should align with business goals.
Step 2: Standardize measurement
Ensure consistency in how MTTD, MTTR, and false positives are calculated across tools and teams.
Step 3: Benchmark and improve
Build a baseline of current metrics and track those metrics as AI SOC analysts gain efficiency.
Measuring for the future
The SOC metrics and KPIs that matter are shifting. MTTD, MTTR, and false positive rates still define the baseline, but AI-driven metrics are becoming essential.
For SOC leaders, adopting an AI SOC mindset and moving toward an autonomous SOC is about measuring what matters most. Start tracking the right KPIs today, and empower your AI SOC analysts to focus on higher-value security outcomes.
Want to see how your SOC can move from reactive firefighting to proactive, AI-powered operations? Sign up for a demo today.