Turn EDR noise into actionable intelligence
Challenges with endpoint detection
Alert overload
EDR solutions flood analysts with false positives from routine activities such as legitimate software installation, scripts and normal use of Windows utilities, burying real threats under thousands of benign alerts daily.
High false positives rates
Without understanding system behavior and cross-environment correlation, many alerts turn out to be benign, wasting precious cycles.
Context gaps beyond endpoint
Endpoint alerts alone can’t reveal how endpoint activity ties back to cloud, identity or SaaS exploits.
Slow, complex investigations
Manually stitching together endpoint logs, identity trails, and cloud events necessary to tell a full story, eats up analyst time.
How Exaforce empowers your SOC for endpoint security
Always-active AI defense that digs past subject lines, following links, attachments, and identity traces, to pinpoint and neutralize email-borne threats before they gaiUnified management for your SOC team or our service that connects endpoint findings with identity, IaaS, and SaaS context, delivering precise threat triage, enriched alerts, and rapid investigations.
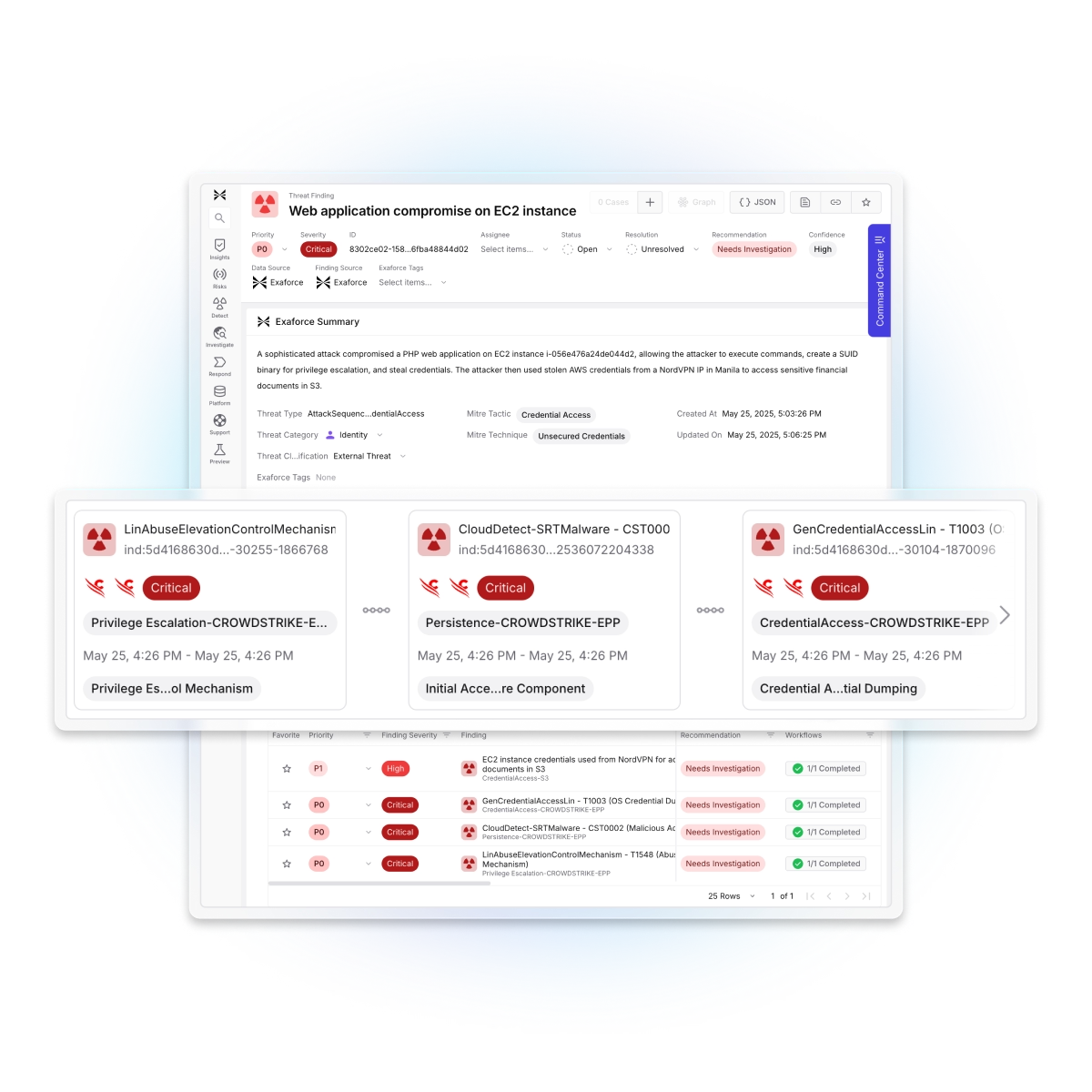
Exaforce connects and contextualizes endpoint detections, accelerating the whole SOC lifecycle.

Eliminate false positives
AI-powered triage instantly validates EDR alerts against actual system behavior and business context, filtering out routine IT operations to surface only genuine threats that require action.

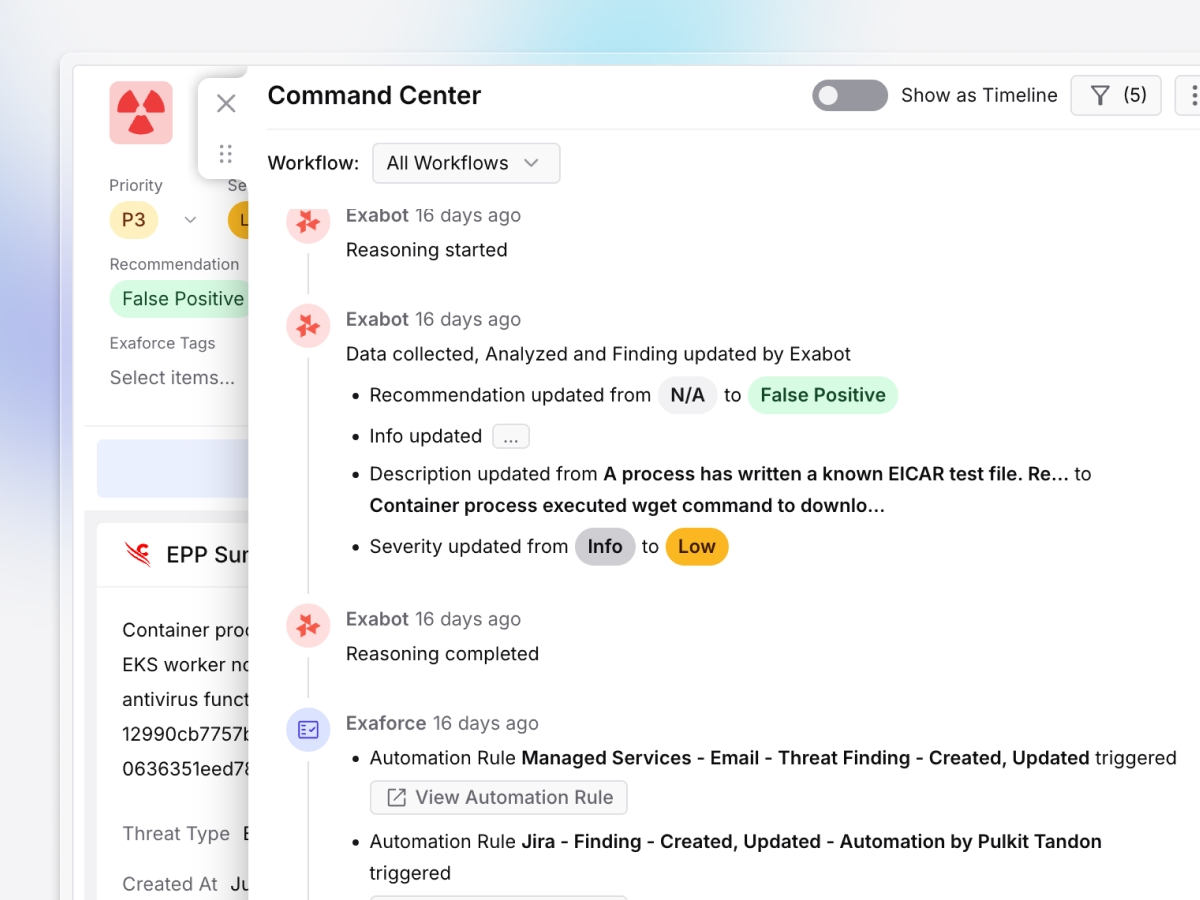
Enriched alerts with actionable context
Each alert is infused with correlated data from endpoint logs, threat intelligence data and correlated evidence, transforming raw EDR events into actionable incidents with clear response steps.

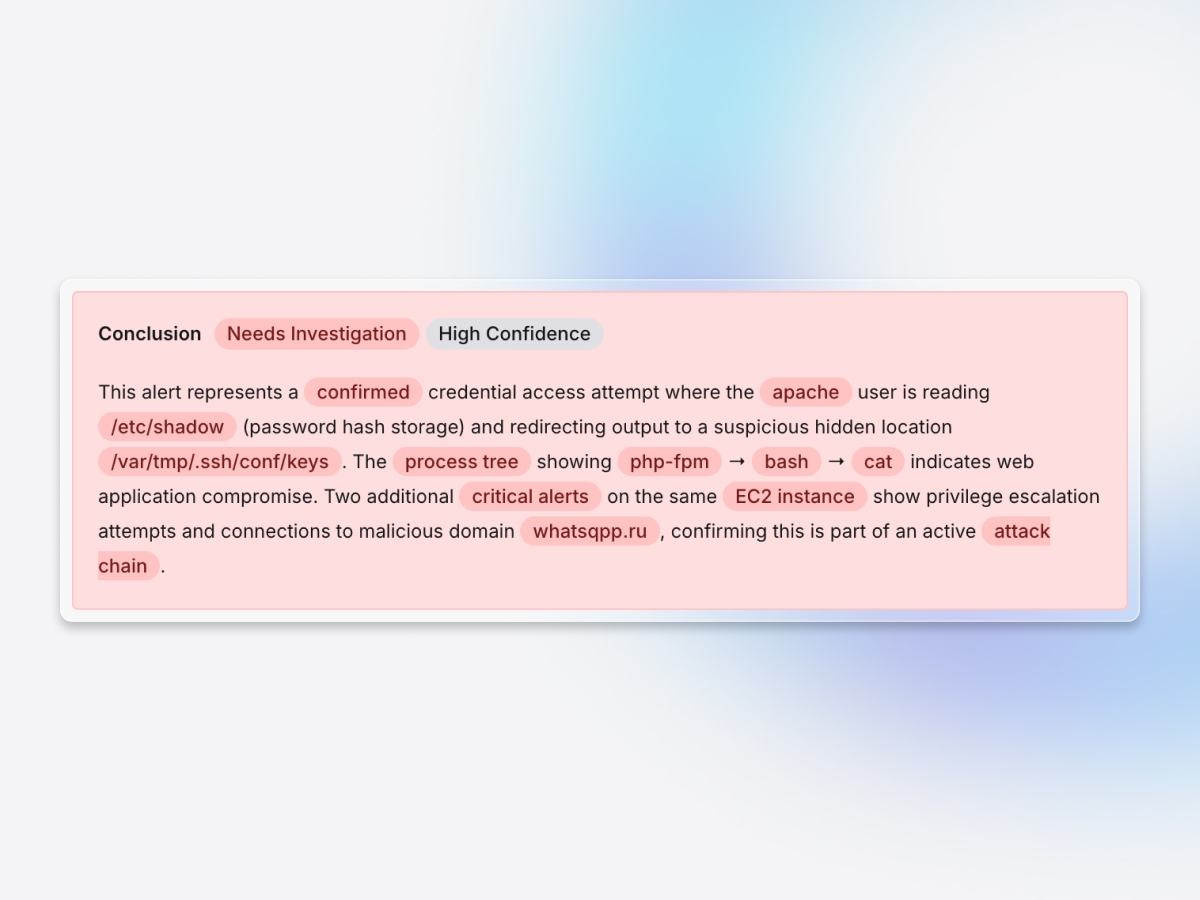
Cross-system contextualized findings
Connects endpoint alerts to their cloud and identity impact, exposing the full kill chain from initial compromise through lateral movement to data exfiltration that endpoint-only tools can't see.
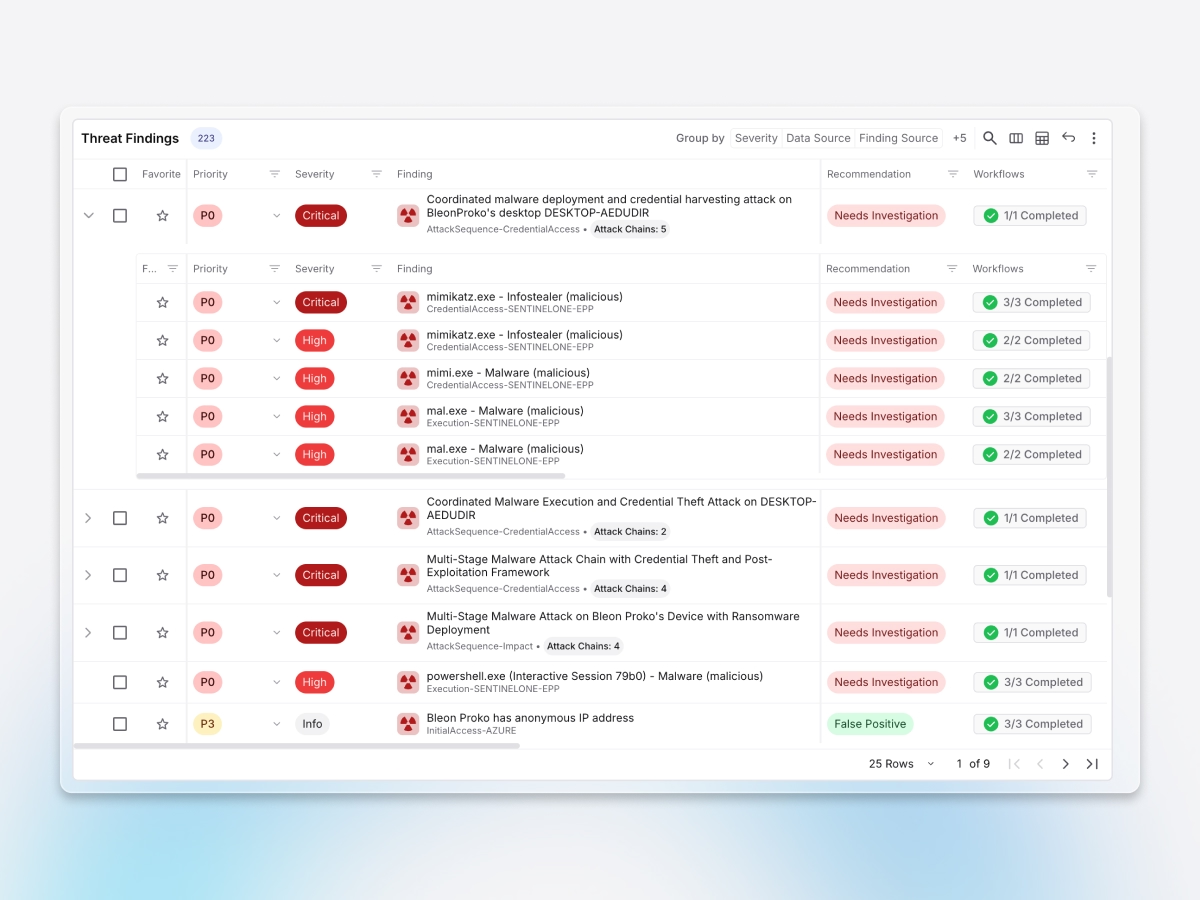

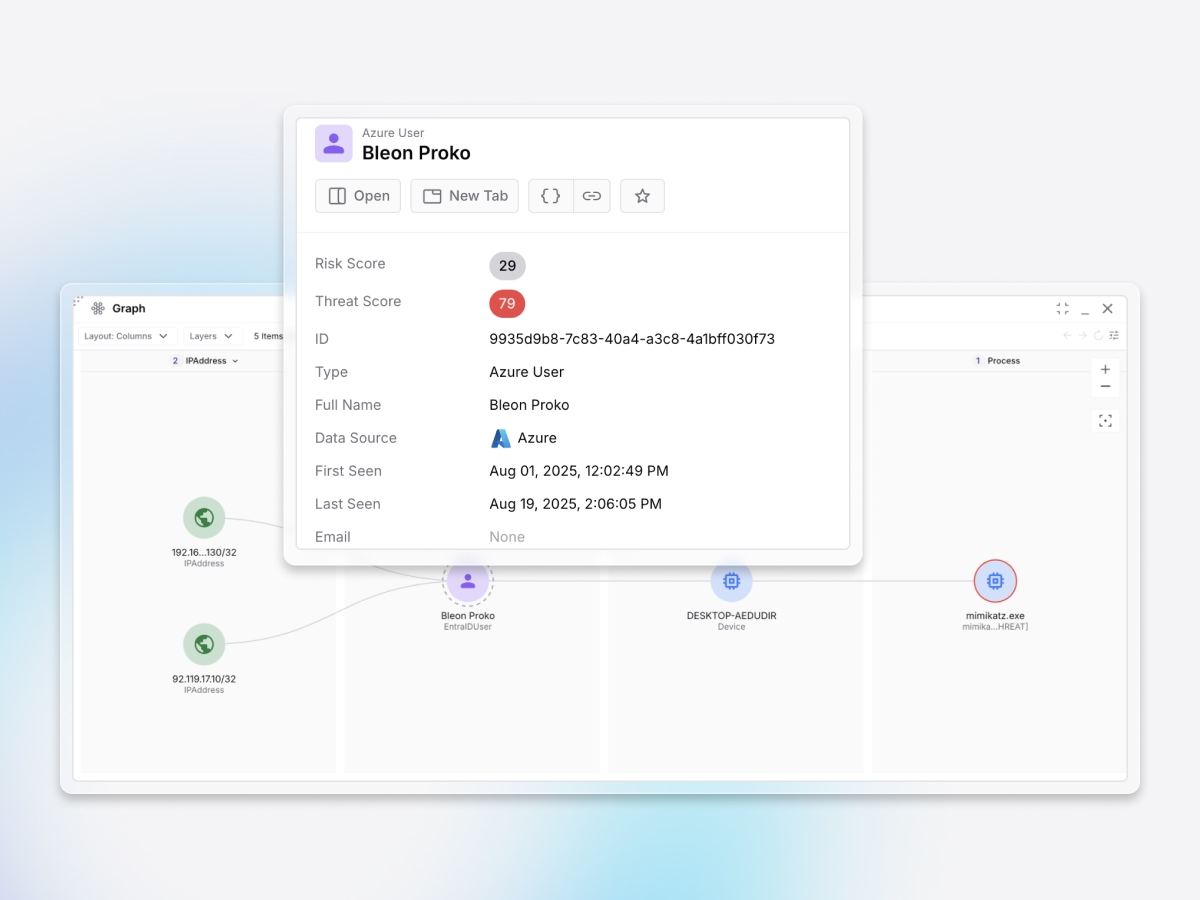
Accelerate investigations
Unifies endpoint, cloud, and identity telemetry into a single attack timeline, reducing investigation time from hours to minutes with automatic evidence correlation and visual attack mapping.
Before Exaforce, security was a key top of mind challenge. Now we see everything, with the visibility and coverage to protect our entire platform.

Frequently asked questions
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you



