Stop SaaS data breaches

Challenges with SaaS security
Gaps in detection coverage
Critical SaaS applications such as GWS, GitHub, OpenAI, and JIRA remain under-monitored, leaving blind spots where attackers can access some of your company’s most sensitive data.
Limited visibility into user actions
Most teams can’t answer who did what, when, and where across SaaS and IdP managed environments, slowing investigations, insider threat detection, and threat hunting.
Compliance gaps in SaaS environments
Default SaaS controls often fall short of audit and regulatory requirements, whether it’s limited log retention or missing policy enforcement, leaving organizations exposed to compliance risk.
Risky misconfigurations and poor hygiene
Weak or missing MFA, missing security controls, excessive permissions, and other misconfigurations create an open door for attackers and make enforcing consistent SaaS security hygiene difficult.
How Exaforce empowers your SOC for SaaS security
Exaforce’s AI-powered SaaS threat detection correlates identity, endpoint, and cloud activity to slash false positives and expose real compromises with full visibility and automated workflows to augment your SOC team or our service.
Exaforce connects the dots across SaaS, exposing real risks instantly
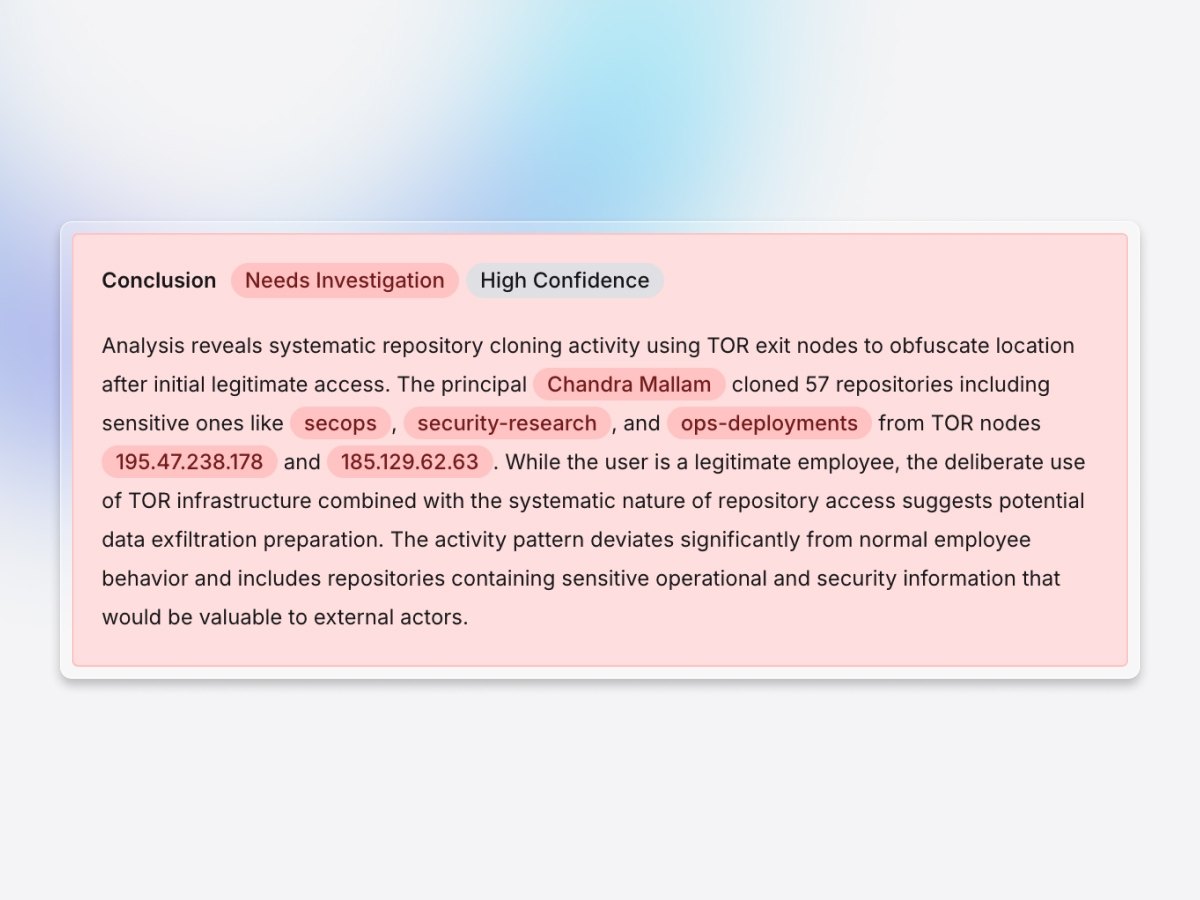

Comprehensive SaaS coverage
Exaforce monitors collaboration, version control systems, and other critical apps with ML-based detections, closing blind spots where sensitive data could be exposed.
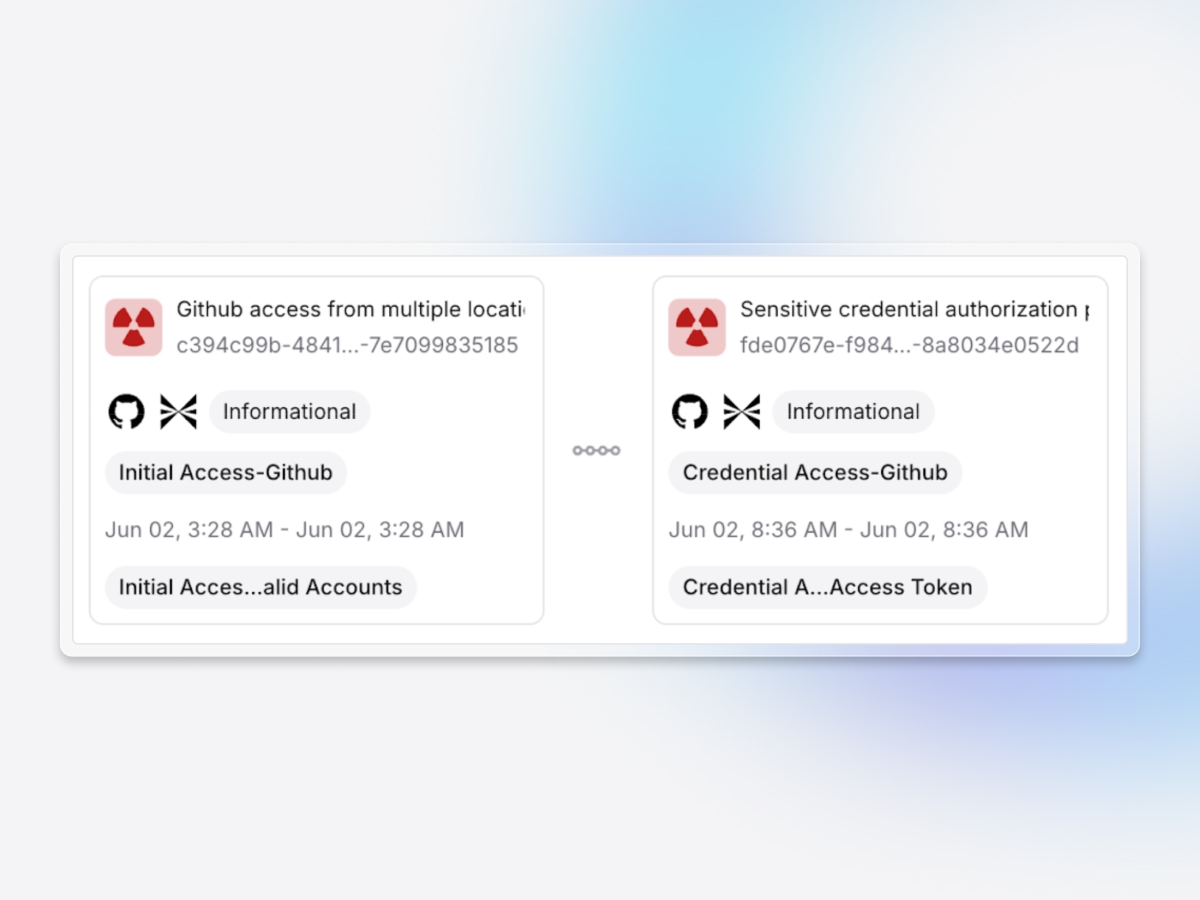

Full user action visibility
Exaforce tracks every action across SaaS environments and stitches related events together across systems, creating clear timelines that accelerate investigations and insider threat detection.
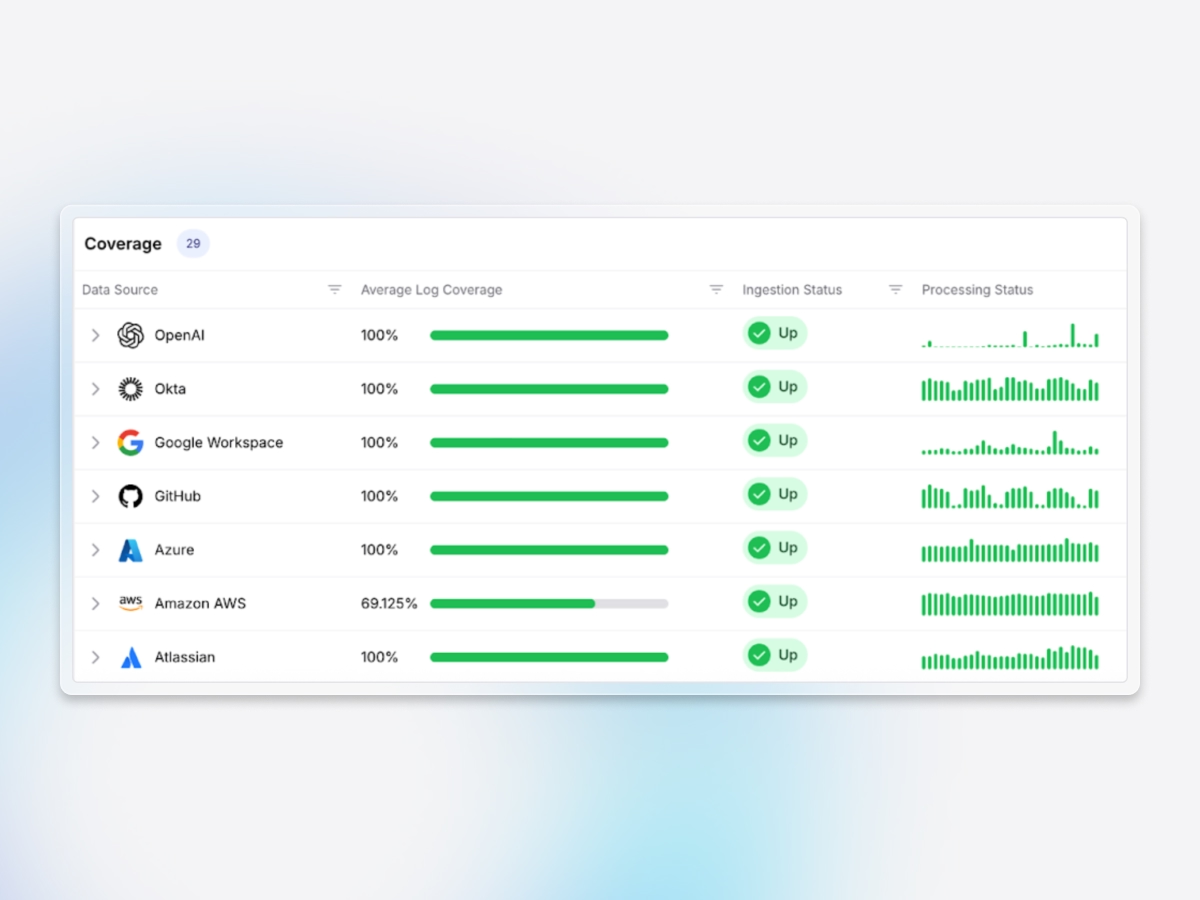

Built-in compliance coverage
Exaforce helps organizations meet compliance requirements across SaaS environments with extended log retention and continuous checks against configuration requirements.
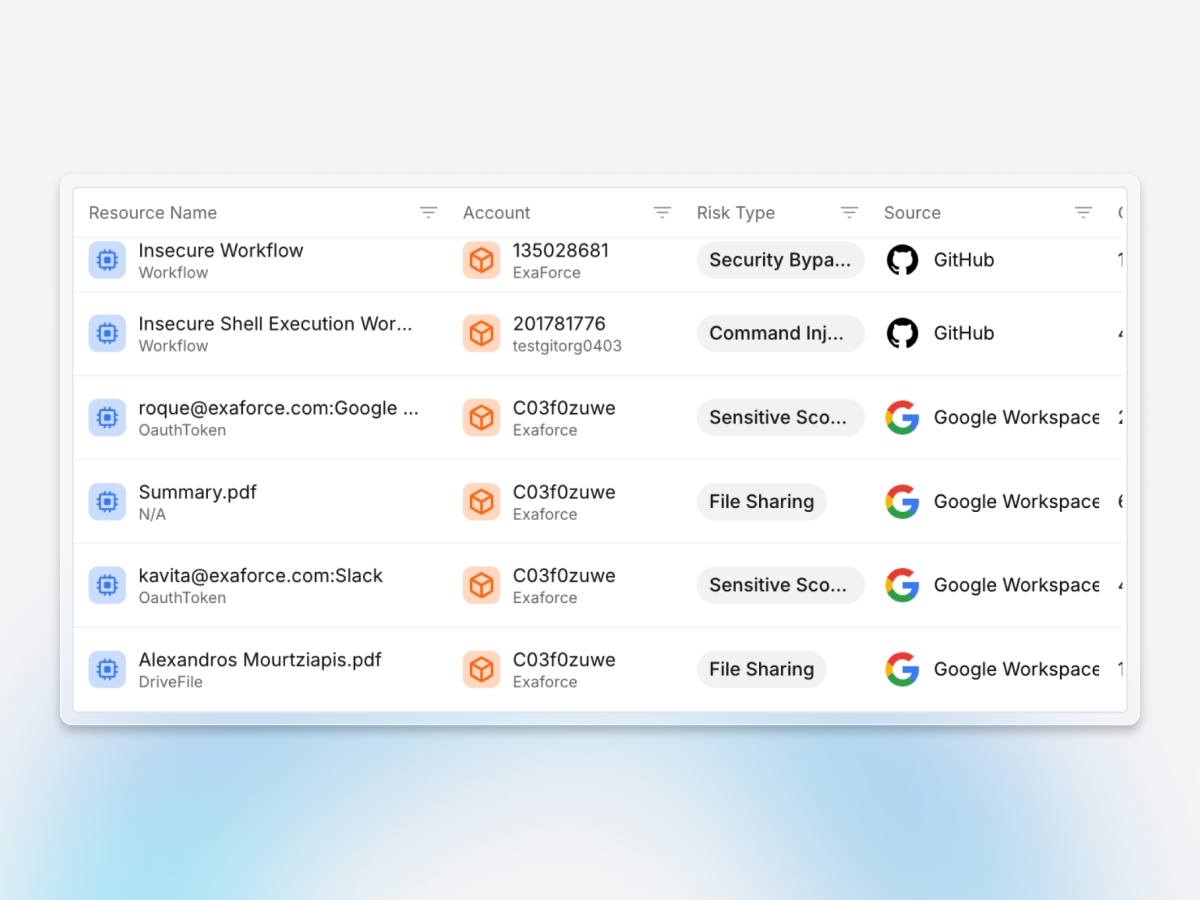

Continuous configuration assurance
Exaforce automatically detects weak controls and configurations like public exposures, missing MFA, or excessive permissions, guiding remediation to enforce strong SaaS hygiene.
Exaforce has transformed our SOC operations by filling critical gaps—especially in detection and response for our SaaS tools, where native capabilities fall short. Investigation times have been cut by 50% thanks to their agentic workflows that automate routine tasks like user confirmation, enabling our team to focus on strategic threats.

Frequently asked questions
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you



