Prevent account takeover
Identity coverage challenges
Increased attack surface
The explosion of cloud services, non-human identities, and AI agents blurs routine activity from malicious actions, forcing security teams to find the threat needle in an identity haystack.
Rising account takeover risks
Identities are the keys to cloud accounts, making them top targets for compromise and credential theft, especially high-privilege accounts used by admins and automation tools like CI/CD pipelines.
Missed signals
Identity compromises are getting faster, and critical clues, such as sudden role changes or unusual login patterns, can be hidden within fragmented logs, obscuring early signs of identity misuse.
Slow response
Understanding blast radius, confirming intent, revoking access, and rotating secrets is slow and error-prone in today’s IAM consoles, delaying response and extending attacker dwell time.
How Exaforce empowers your SOC with identity security
Understand identity permissions, eliminate false positives, accelerate triage, and deliver complete context across IaaS and SaaS accounts, whether it’s managed by your team or our MDR service.
Exaforce exposes hidden identity attacks and accelerates investigations

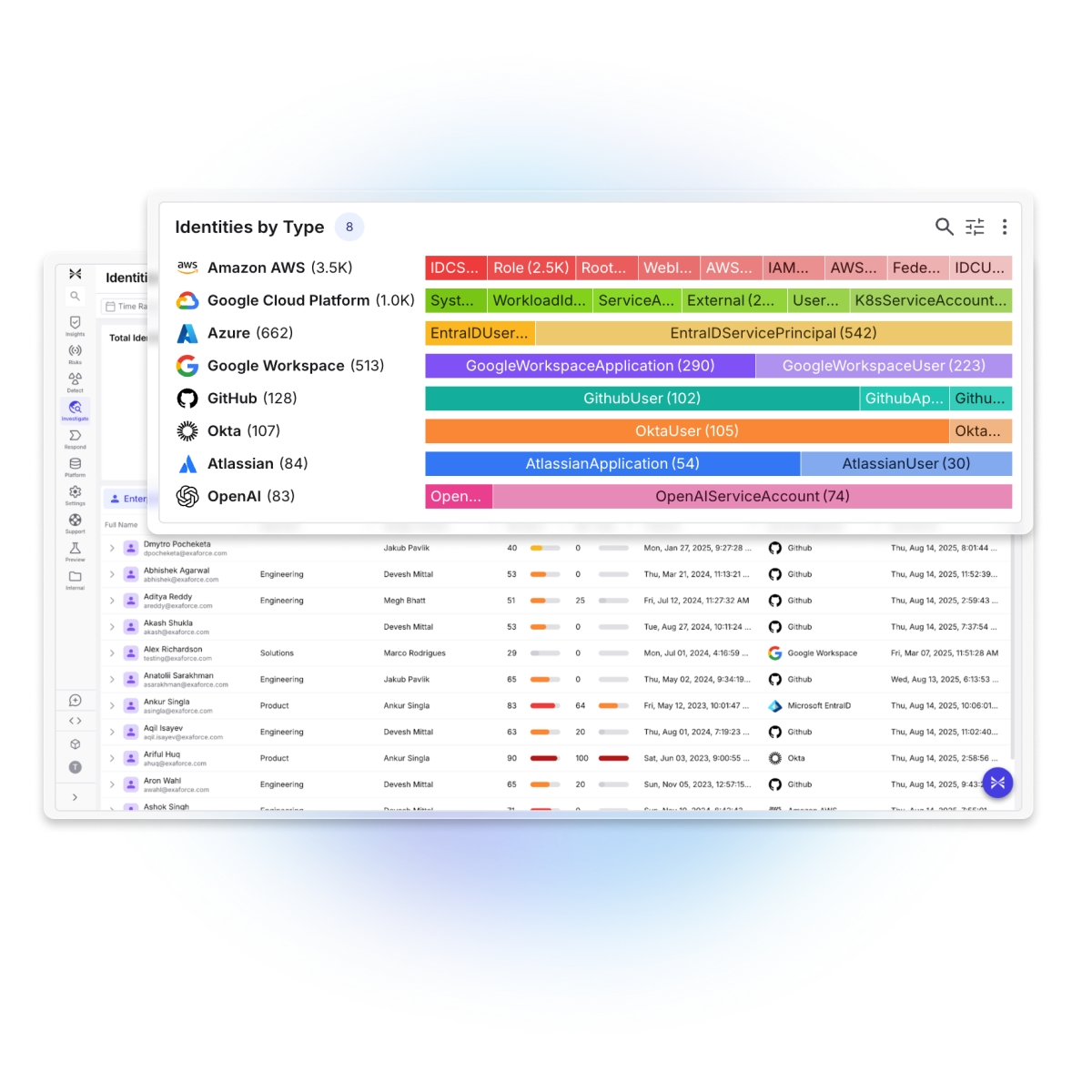
Comprehensive visibility
Exaforce provides a complete inventory of human, non-human, AI agent, and third-party identities, their effective permissions, credentials, and actions to provide complete visibility into identities.

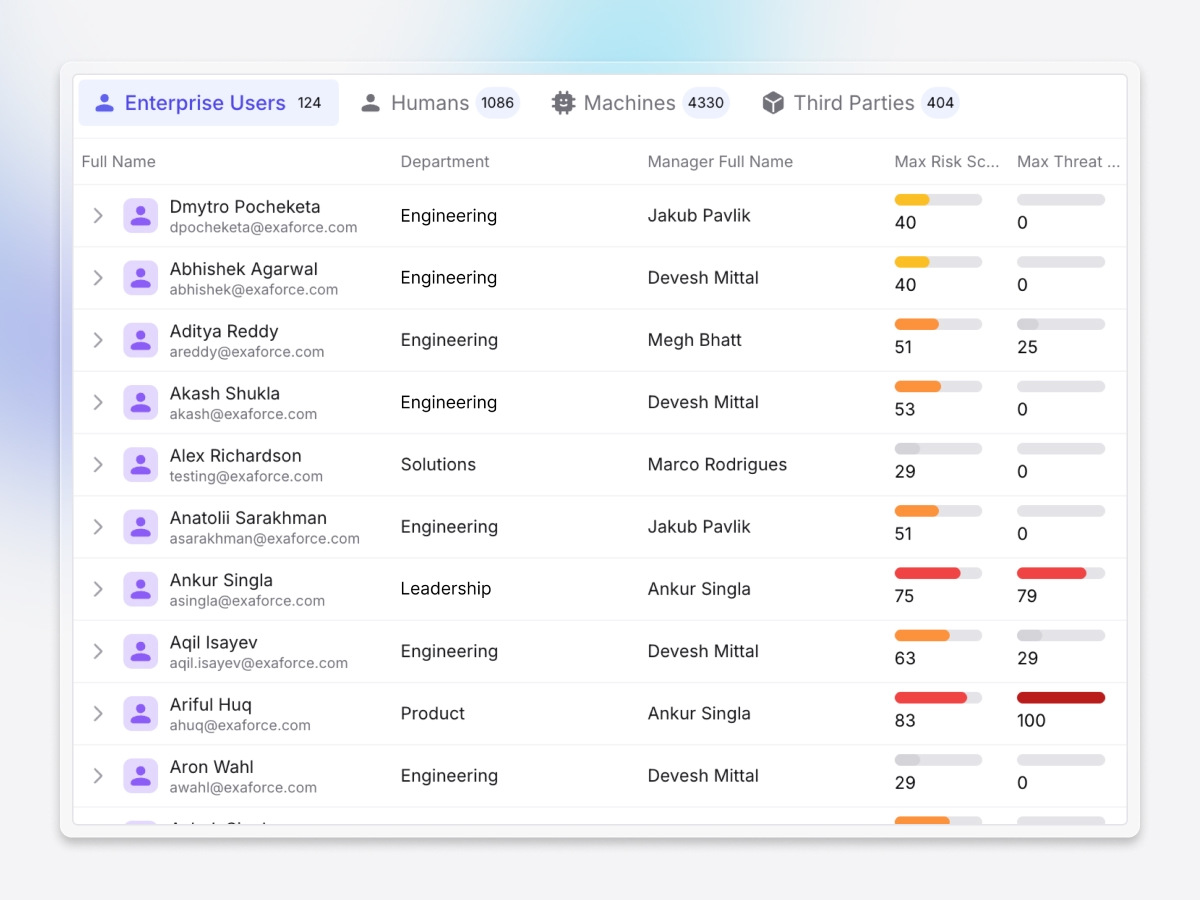
Stops account takeover
Continuously monitor high-privilege accounts and service identities for credential theft and abuse, detecting compromises across IaaS and SaaS before attackers can escalate.

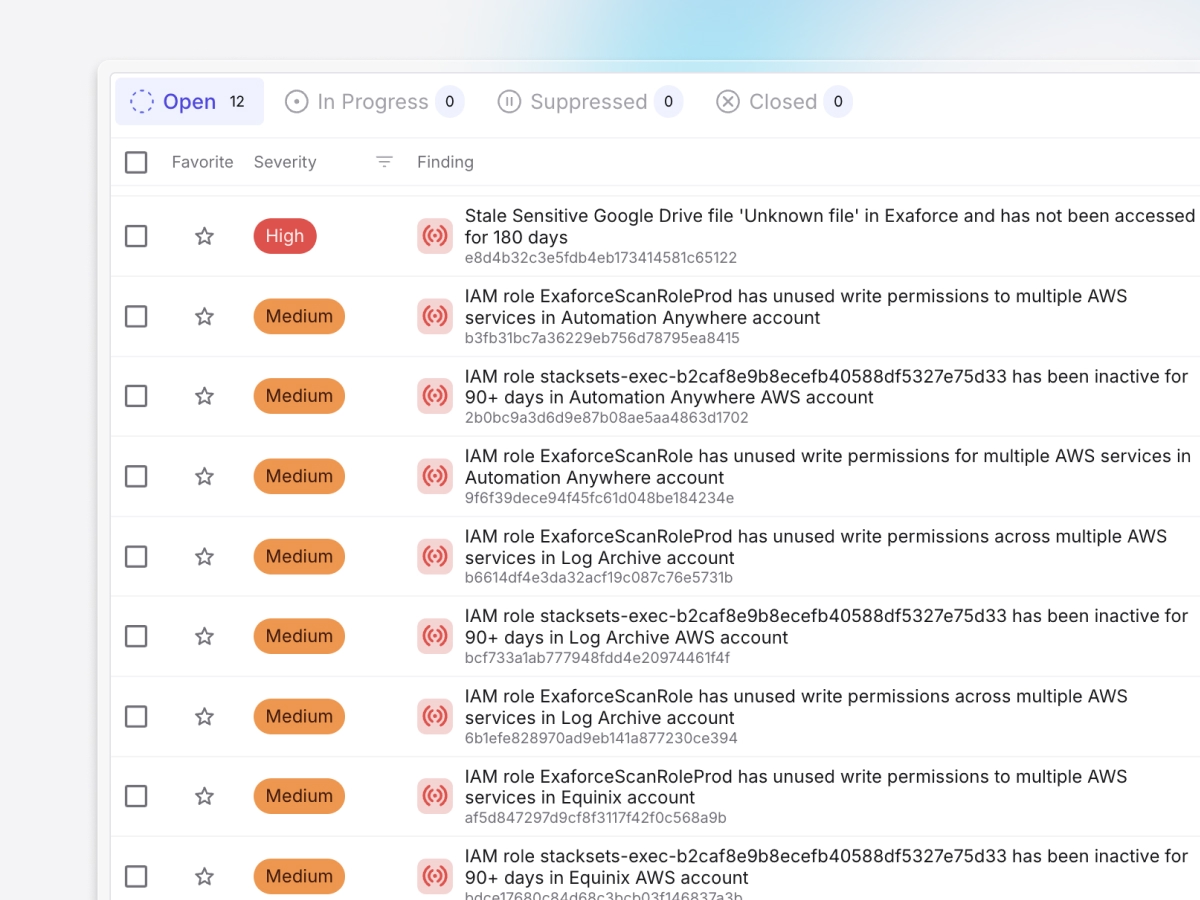
Catch hidden attack signals
Correlate fragmented identity logs to instantly surface buried indicators such as role changes, unusual logins, and permission escalations, exposing lateral movements and persistence attacks.
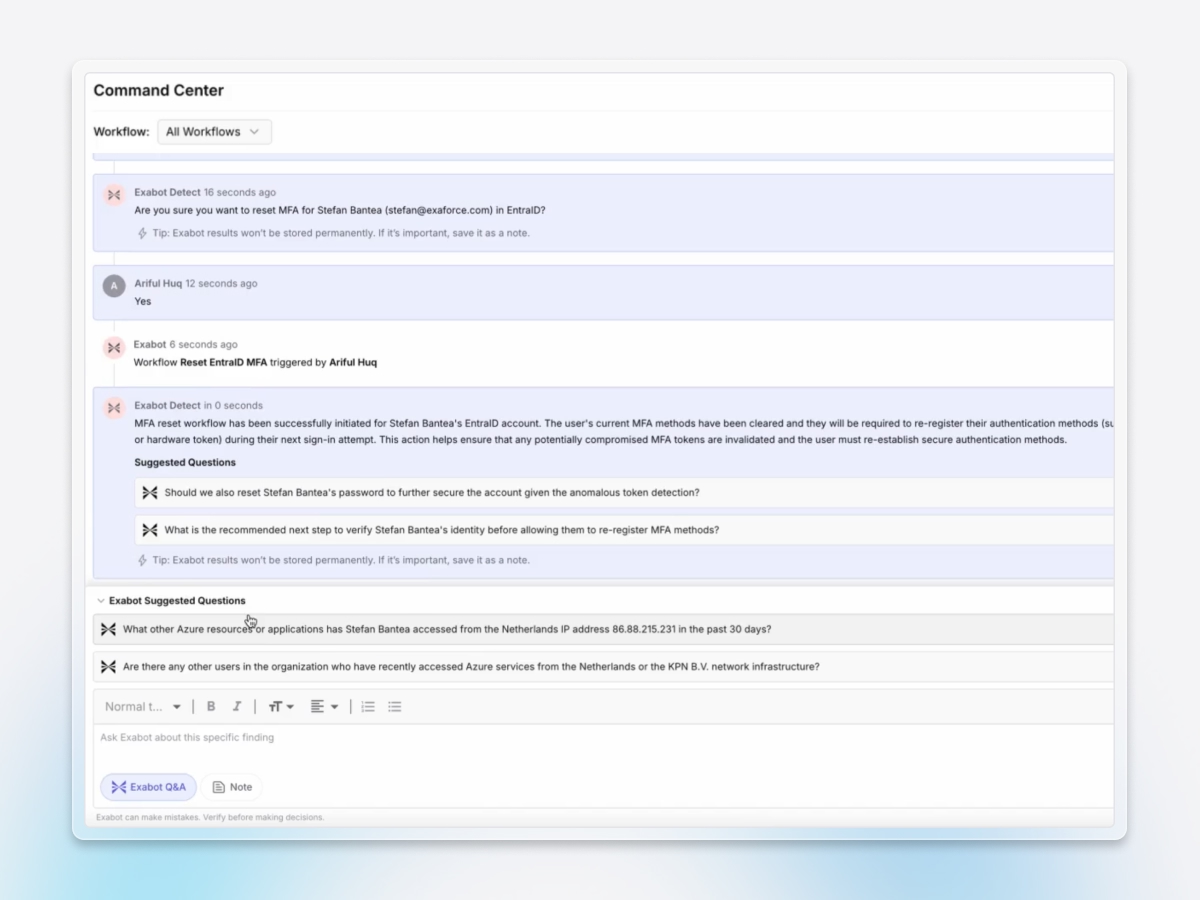

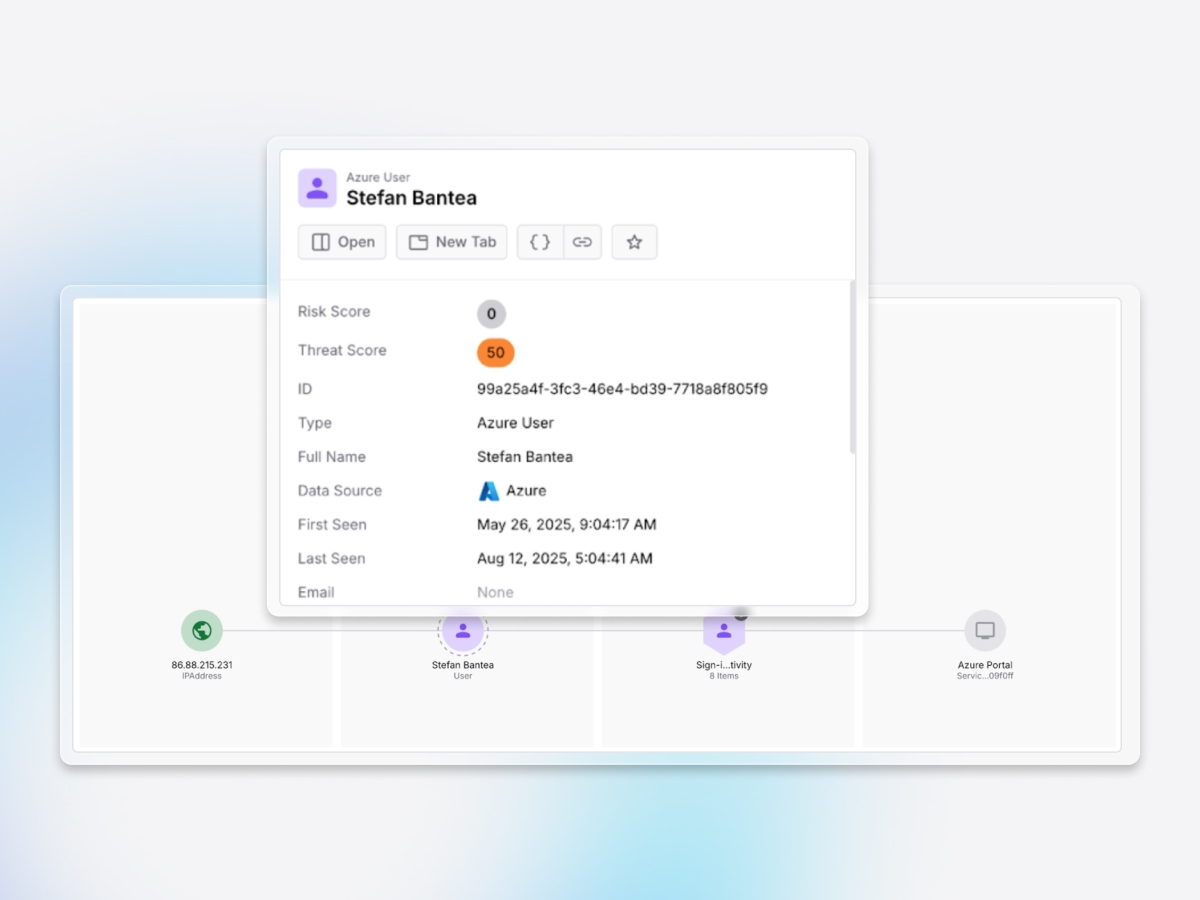
Accelerated response
Instantly maps blast radius, confirms malicious intent, and automates access revocation and secret rotation, reducing attacker dwell time from hours to minutes.
Pioneering early with Exaforce and their novel Agentic SOC platform has significantly enhanced our detection and response for cloud services, such as Github, used by our development teams, in spotting identity misuse. The platform delivered actionable cloud insights within 24 hours of onboarding - one example was identifying 3rd party vendor misuse of their credentials in our environment. The rich data platform provides quick answers to hard questions & tasks across our SaaS and IaaS environments.

Frequently asked questions
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you



