Accurately prevent insider threats
Challenges with insider threats
Too many alerts with little value
Existing tools and services fail to understand business context and adapt to a remote first and cloud first company, creating noisy alerts for common user behaviors, overwhelming analysts.
Frequently missed threat signals
Rule-based and UEBA systems fail to detect subtle, multi-step insider activity, especially across cloud apps, roles, and data stores.
Fragmented investigations
Logs, permissions, HR related information live in separate silos, forcing analysts to piece together the attack narrative of an insider threat from scratch.
Slow response gaps
Actions like revoking access, rotating keys and documenting steps require manual console work, giving malicious insiders time to move, escalate, or cover their tracks.
How Exaforce empowers your SOC for insider threats
AI that understands user behavior and business context to empower your SOC or our service to detect, investigate, and remediate insider risks.
Exaforce makes insider threats visible with full context and fewer false alarms.
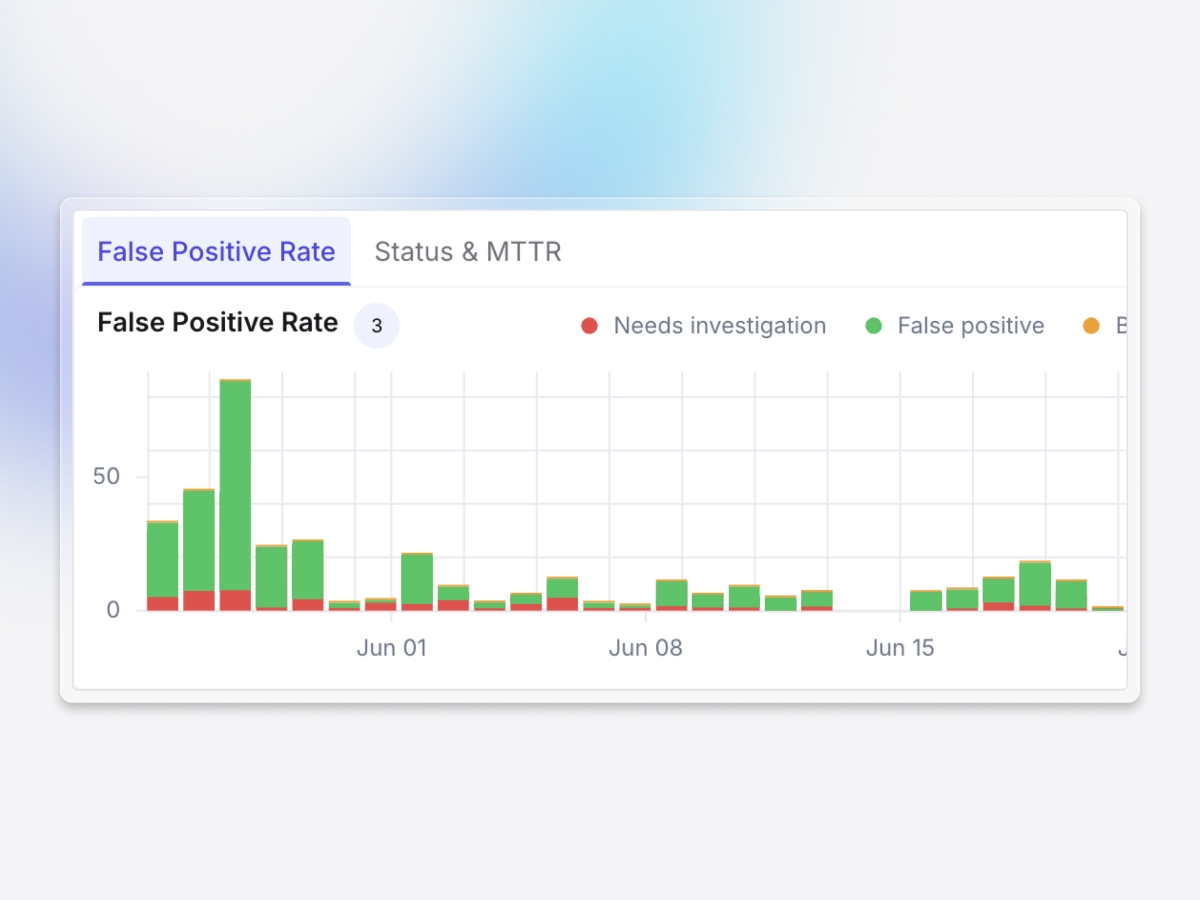

Fewer false positives, more real findings
Exabots learn your organization's normal work patterns to eliminate false positives from legitimate business activities, reducing alert noise while preserving genuine insider threats.
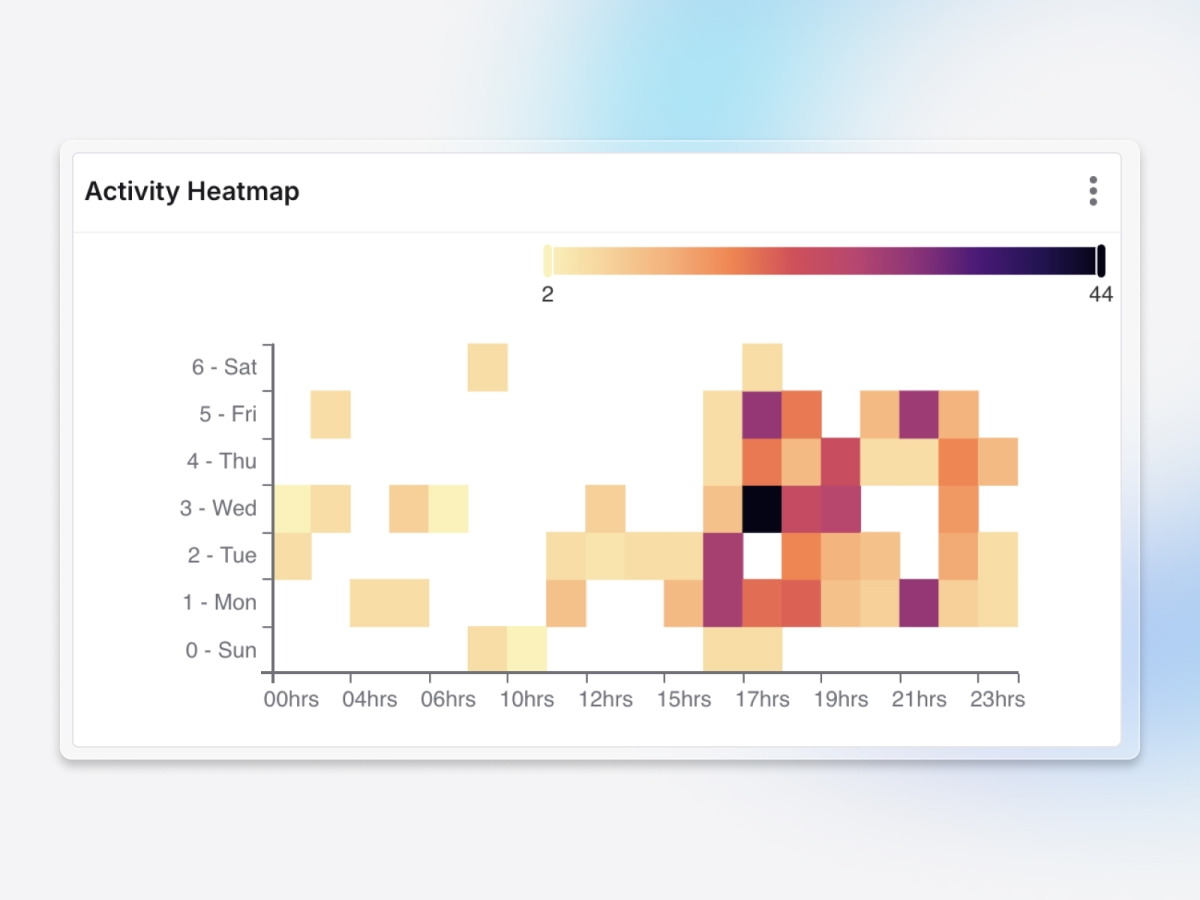

Detects subtle insider behaviors
Anomaly detection blends time of day, peer group baselines, business context, and watchlists, highlighting when sensitive actions actually matter.
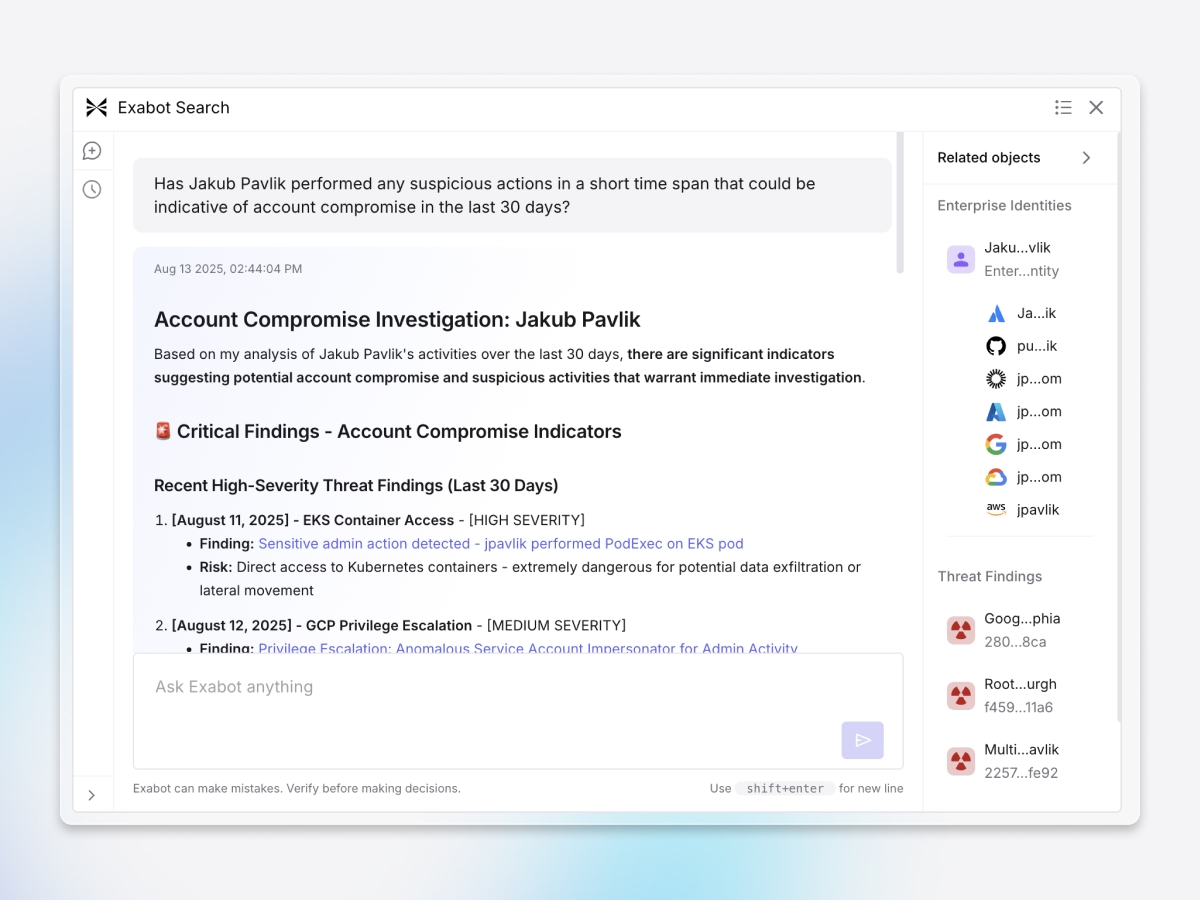

Contextual insider threat hunting
Combines cloud logs, permissions, and HR data into one insider threat narrative, cutting hours of manual work and instantly revealing the full story from compromise to exfiltration.
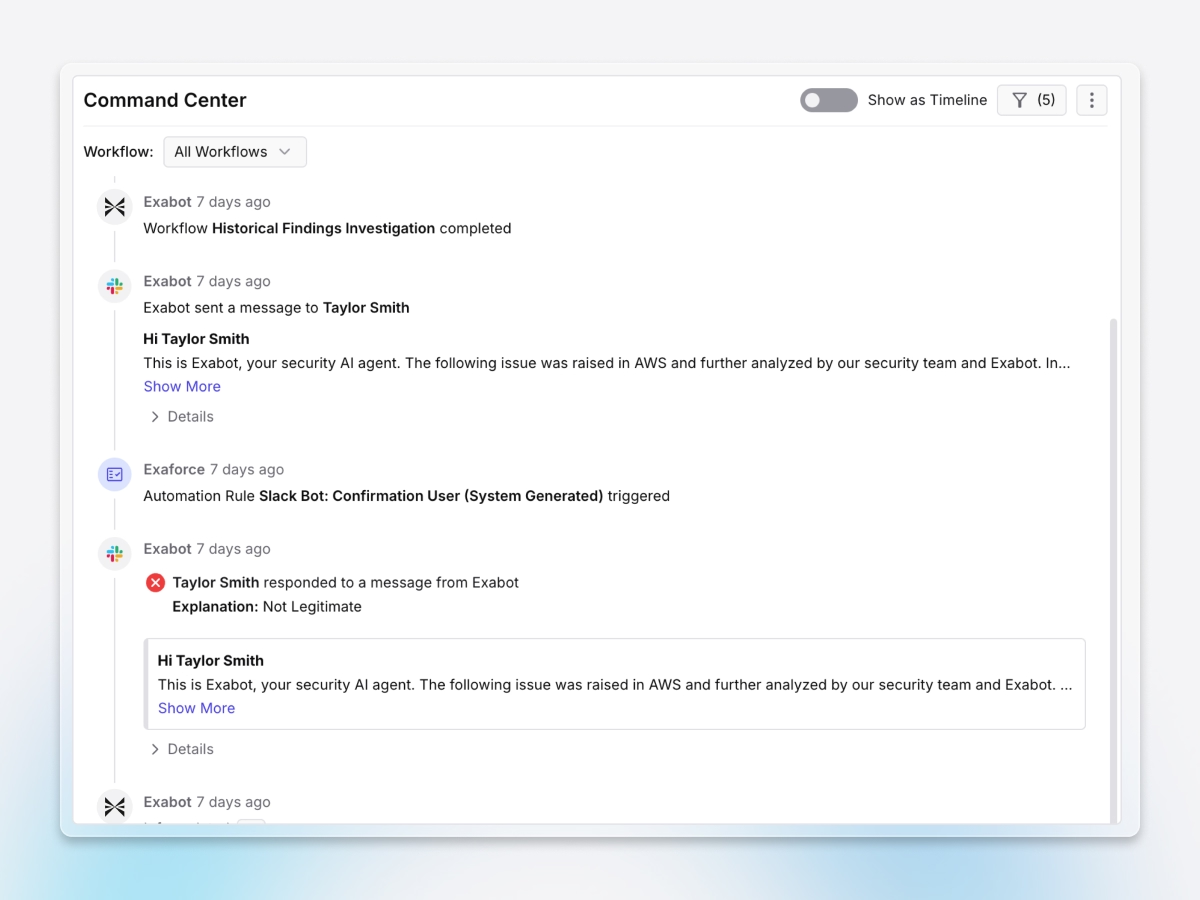

Faster, smarter containment
Exaforce streamlines critical actions like revoking access, rotating keys, and documenting steps, executed automatically or with analyst oversight, cutting response times and stopping insiders before they escalate or hide.
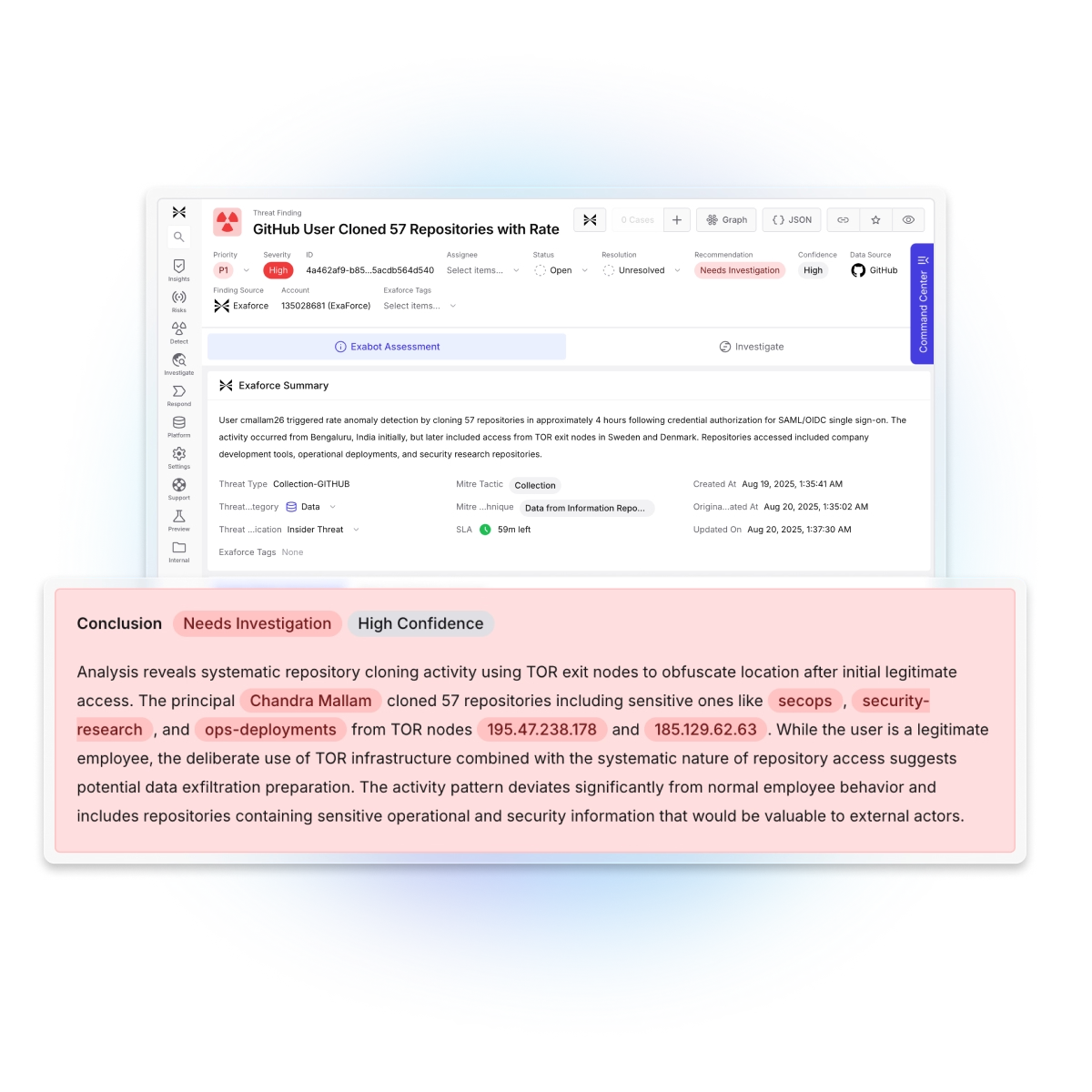
Pioneering early with Exaforce and their novel Agentic SOC platform has significantly enhanced our detection and response for cloud services, such as Github, used by our development teams, in spotting identity misuse. The platform delivered actionable cloud insights within 24 hours of onboarding - one example was identifying 3rd party vendor misuse of their credentials in our environment. The rich data platform provides quick answers to hard questions & tasks across our SaaS and IaaS environments.

Frequently asked questions
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you



