Find and stop real phishing attacks

Challenges with email security
Analyst overload from phishing alerts
Security teams face a constant flood of reported phishing emails, overwhelming analysts with repetitive investigations that slow response times and increase burnout.
Increased sophistication of attacks
AI-driven attackers are crafting increasingly complex campaigns with malicious links, weaponized attachments, and spoofed senders that evade traditional gateways and directly target users.
Unclear blast radius and impact
Security teams often struggle to determine the full scope of a reported phishing event, including which users were affected, what access they had, which systems were involved, and what data may be at risk.
Fragmented investigations across tools
Validating a phishing alert frequently requires correlating email signals with endpoint detections, SaaS activity, and identity logs, forcing analysts to pivot across multiple systems instead of seeing the full picture in one place.
How Exaforce empowers your SOC for email security
Always-active AI defense that digs past subject lines, following links, attachments, and identity traces, to pinpoint and neutralize email-borne threats before they gain a foothold, managed by your SOC team or ours.
Exaforce instantly triages and accelerates phishing investigations
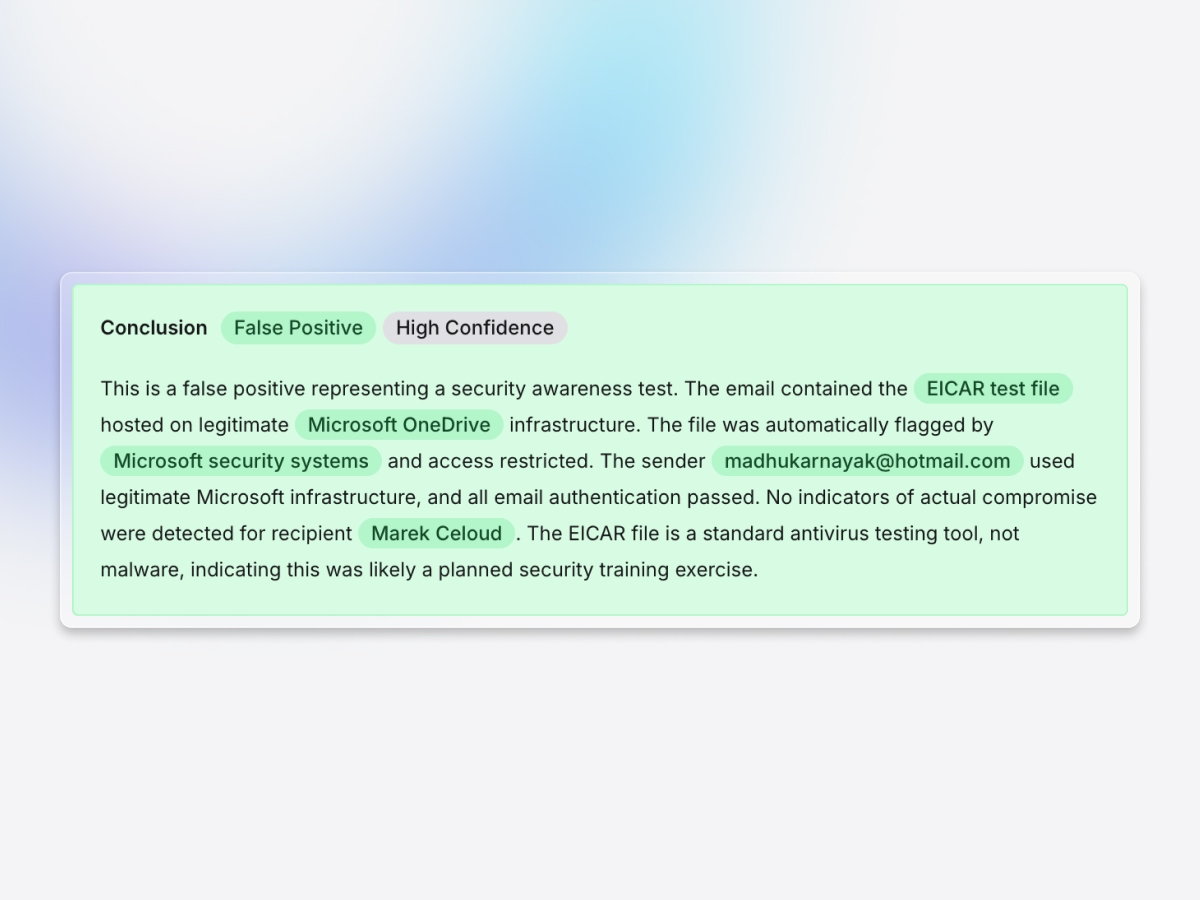

Reduced phishing overload
Exaforce reduces the manual burden by automatically triaging and enriching reported phishing alerts, cutting noise, and letting teams focus on the threats that matter.
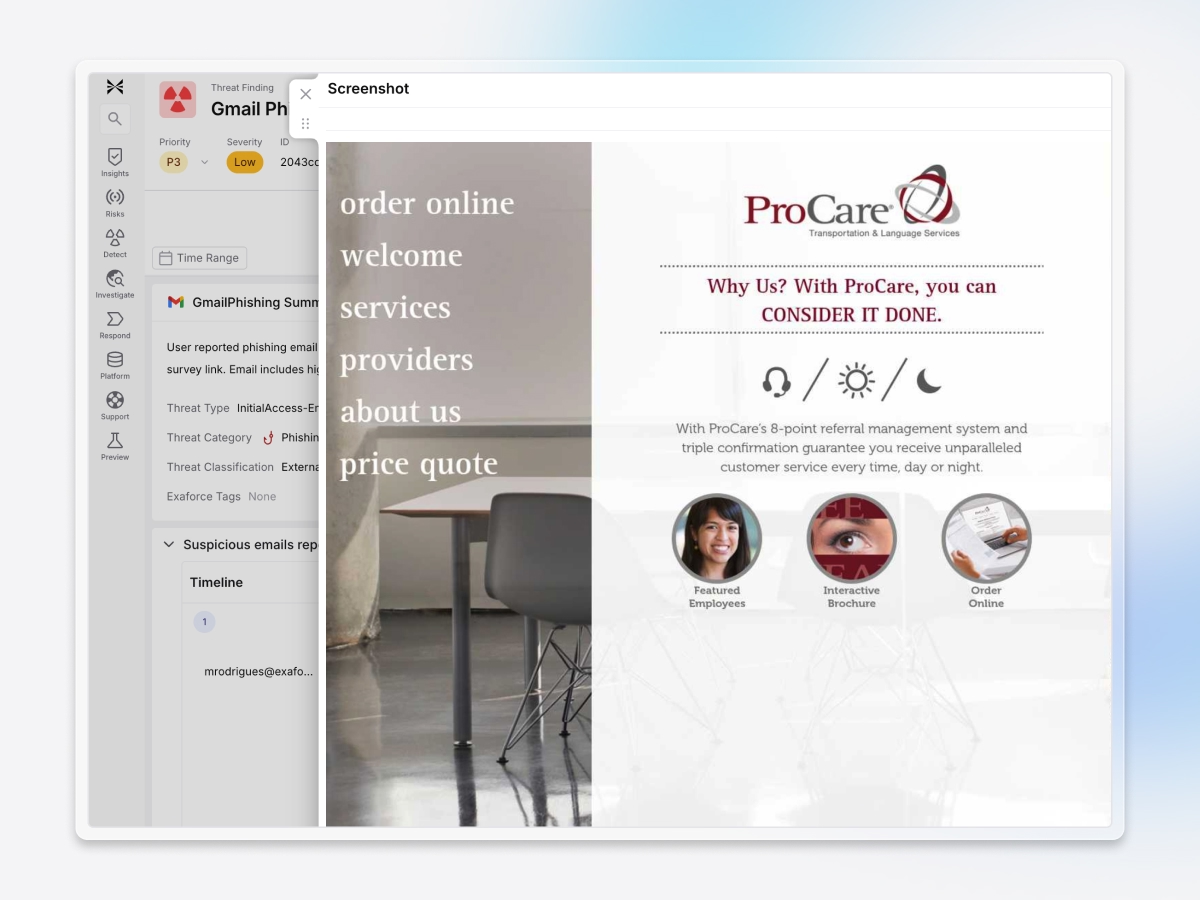

Stay ahead of evolving attacks
Exaforce ingests raw email logs, headers, and HTML to capture full click-path evidence, identify malicious URLs, and render embedded links so analysts can quickly confirm whether the emails are malicious or spoofed.
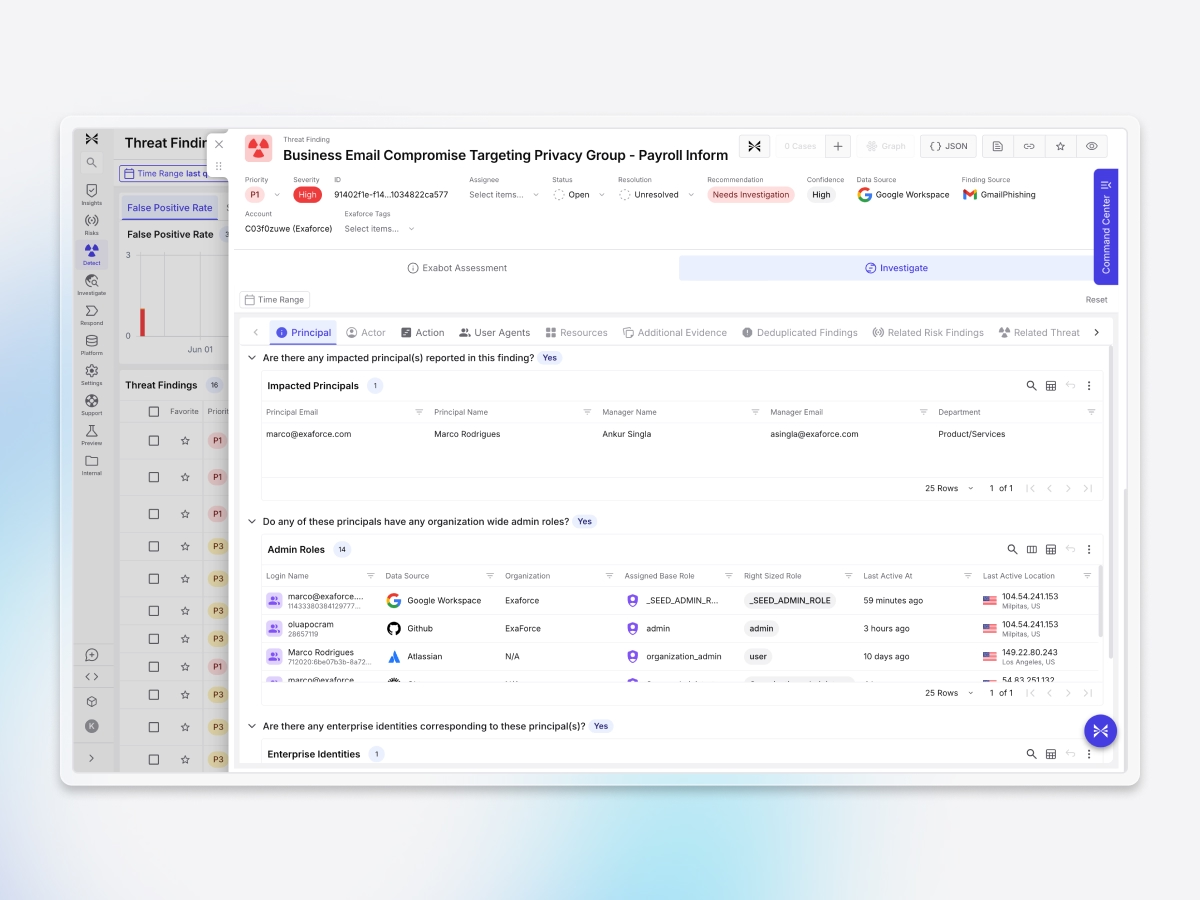

Automated impact analysis
Exaforce automatically traces user activity, access permissions, and data access to map the impact of a phishing event, giving analysts clear visibility into affected users, systems, and data.
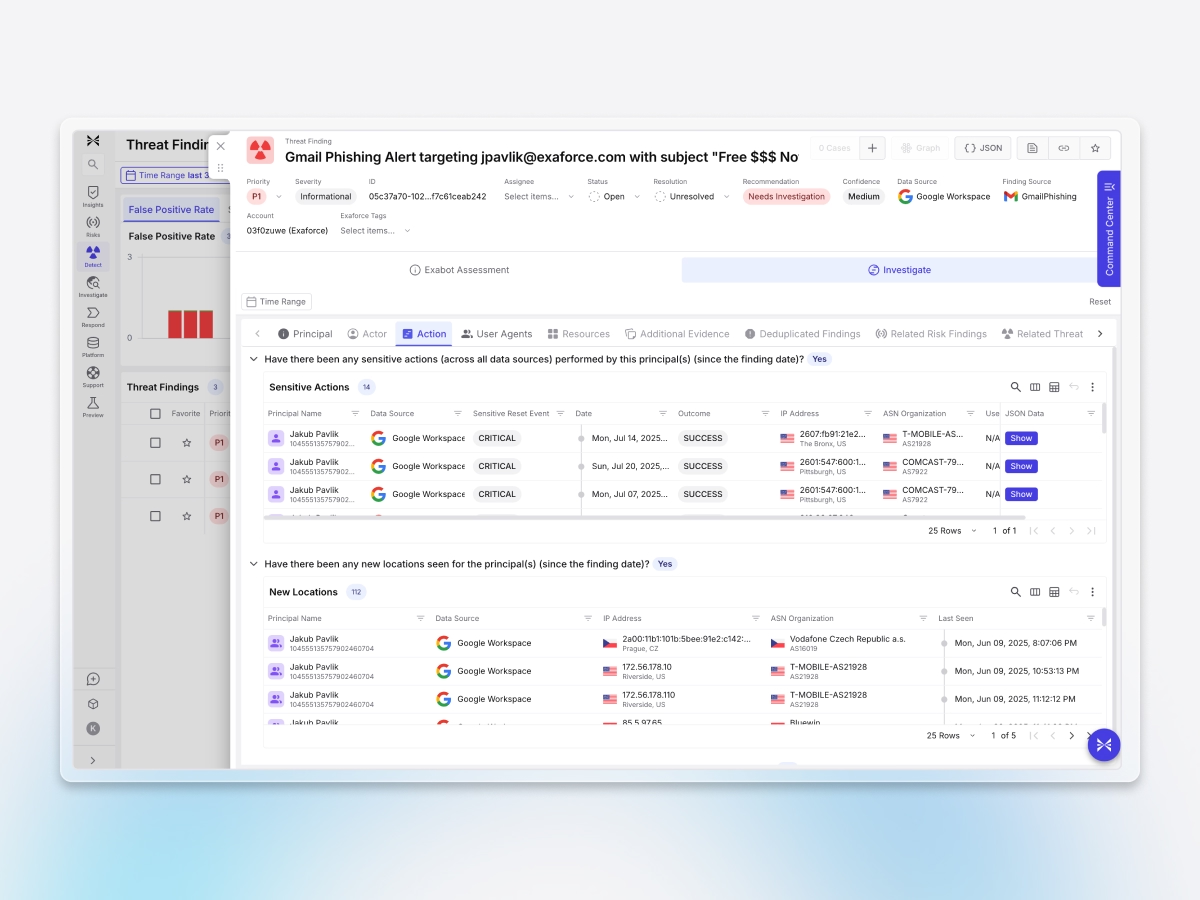

See the full attack path
Exaforce correlates email alerts with endpoint, SaaS, and identity signals into a unified investigation, eliminating tool-hopping and accelerating response.
With Exaforce, our confidence in our Opsec capabilities has grown multi-fold. Where Exaforce stands apart is the detection and response. The ability to sift through GuardDuty alerts and come up with human readable alerts and actionable mitigations solves a big pain point for Fuze. Another advantage which we've not found elsewhere is the ability to correlate actions across data sources and come up with visualizations, which has helped us unearth patterns that we were unaware of.

Frequently asked questions
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you



