Stop public IaaS breaches
Challenges with IaaS threats
Exploding log volume
Cloud environments generate millions of logs daily, creating a data avalanche that buries critical security signals in noise, making manual analysis impossible and storage costs unsustainable.
Alert overload
Routine admin tasks and everyday engineer activity across public clouds trigger a flood of alerts, masking the few that truly matter.
Coverage blindspots
Development teams leverage new IaaS services faster than rules and traditional anomaly detection can keep pace, continuously creating coverage gaps.
Investigation complexity
Investigating a cloud attack requires reconstructing the attack path from scattered logs, identities, and configurations, demanding deep cloud expertise from talent that's already in short supply.
How Exaforce empowers your cloud SOC
Always-on AI that empowers your SOC or our managed service to detect real attacks, accelerate investigations, and stop breaches.
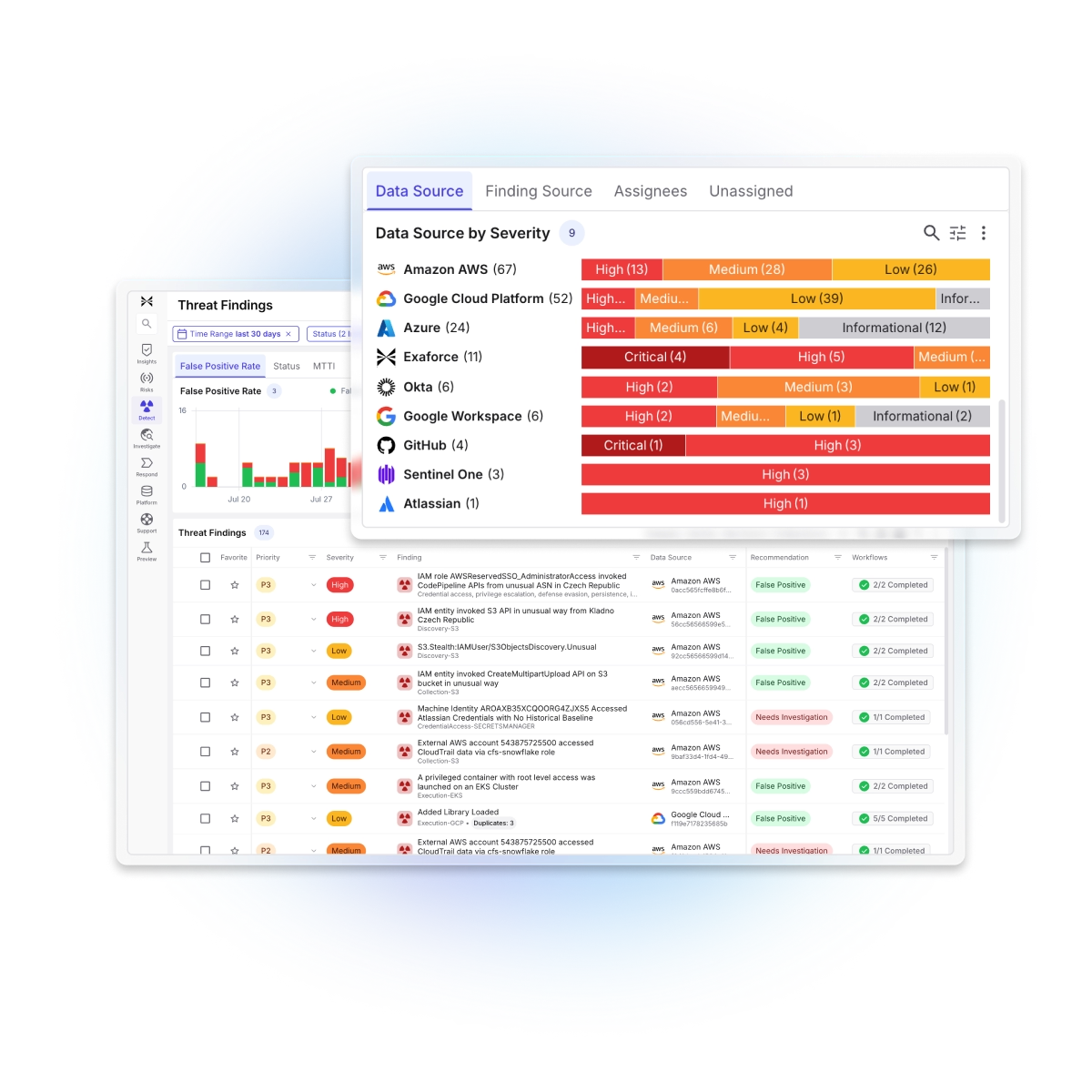
Exaforce cuts through cloud volume, leaving only real threats with full investigations.

Handles cloud scale
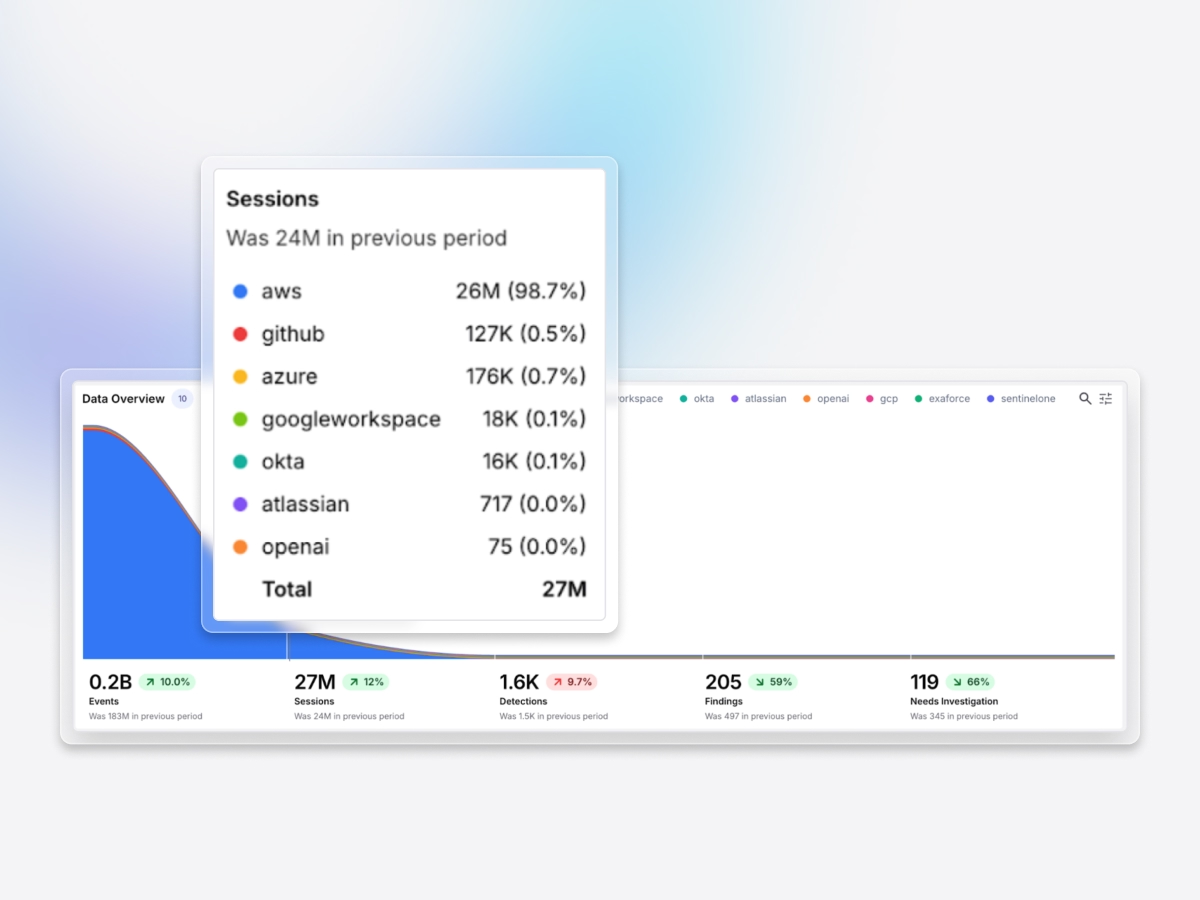
Exaforce intelligently deduplicates and transforms cloud data to slash storage costs while surfacing exactly what Exabots and analysts need for rapid triage, investigation, and response.
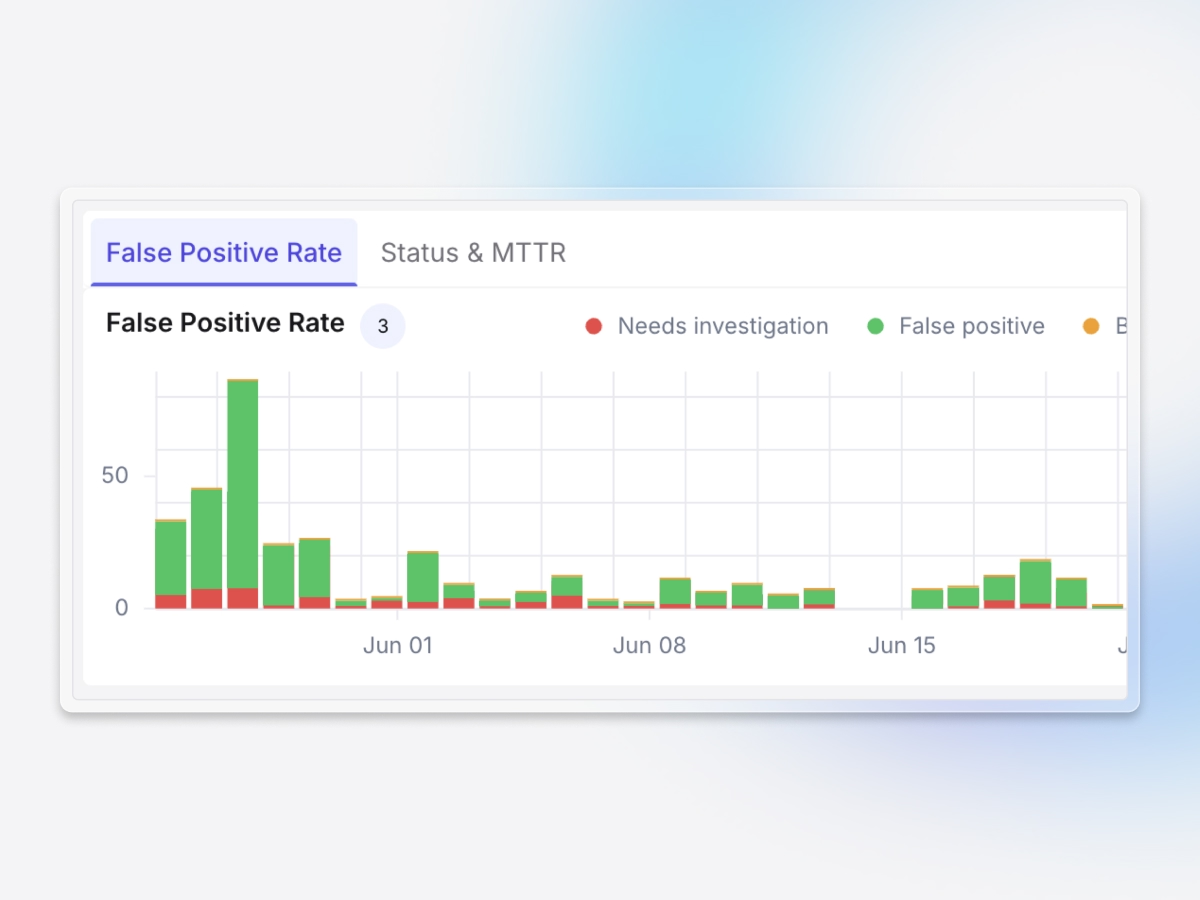

Reduced false-positive alerts
Cuts through the flood of alerts from everyday cloud activity, automatically dismissing false positives while escalating real threats that matter.


Detects what others miss
By stitching identities, events, and resource configurations (workloads, repositories, and more), across AWS, GCP, GitHub, and more, Exaforce uncovers blended attack paths that siloed rules overlook.
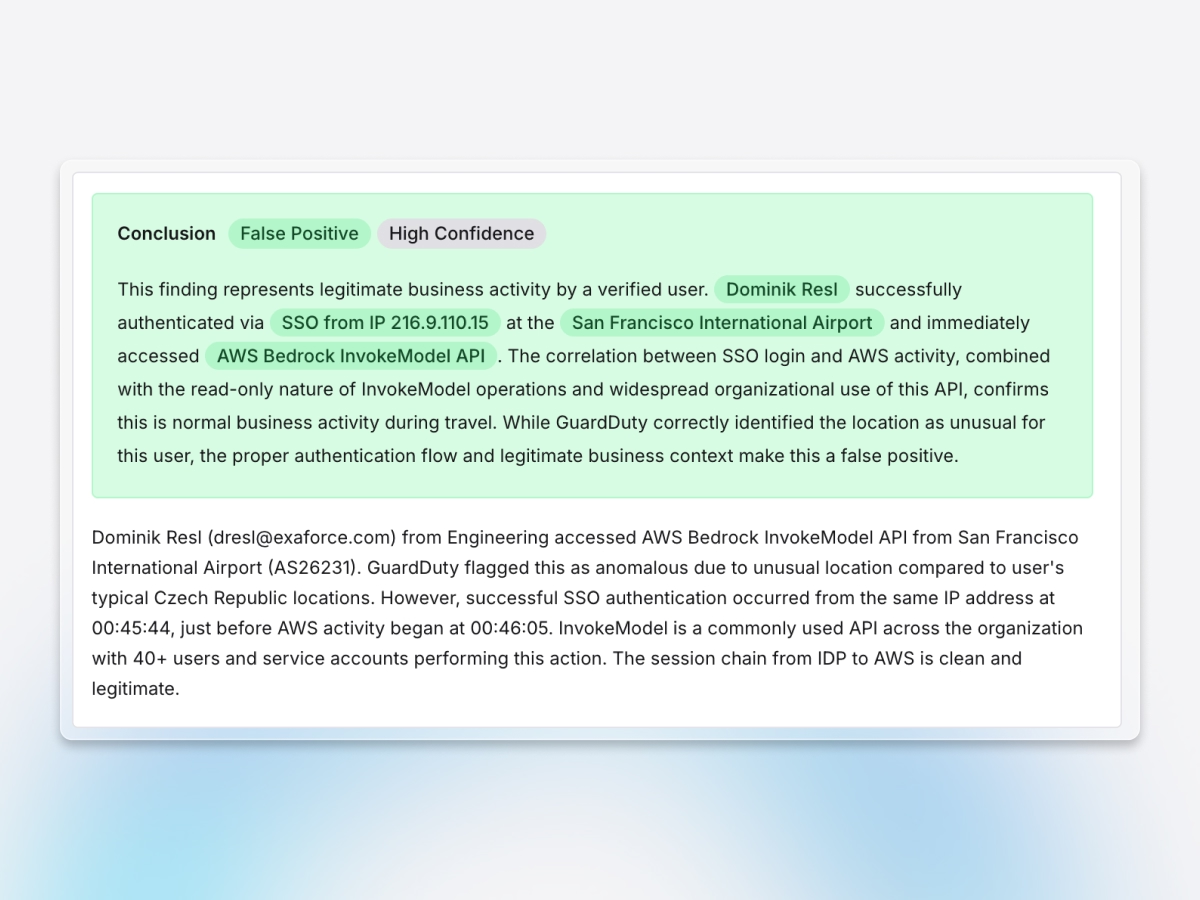

Simplify investigations
Exabots automatically reconstruct attack paths from scattered logs, identities, and configurations, delivering the deep cloud expertise your team needs without requiring specialized talent.
Exaforce has significantly improved our SOC efficacy by augmenting threat detection and response for AWS and Azure with AI. Its auto-triage of third-party alerts and rule-free detection streamlines our response and saves us dozens of hours, letting our team focus on mitigating threats, while their exploration capabilities offers greater visibility into all our Cloud services.
Frequently asked questions
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you



