Accelerate investigations and threat hunting
Simplified, faster investigations and threat hunting
Exabot Investigate supports natural language search, visual exploration, and simplified queries across your data sources. Analysts of any skill level can hunt threats and investigate incidents without mastering complex query languages or source-specific schemas.
Deep understanding of identity, cloud, SaaS, endpoint, network, AI, and code systems
Exabot's Semantic Model resolves entities and relationships across all connected sources automatically mapping users to cloud identities, linking resources to sensitivity classifications, and correlating actions across systems. Analysts can investigate complex scenarios without domain expertise in AWS, GCP, Okta, GitHub, Office 365, OpenAI, or any platform, focusing on threat analysis.


Turn simple questions into deep investigations
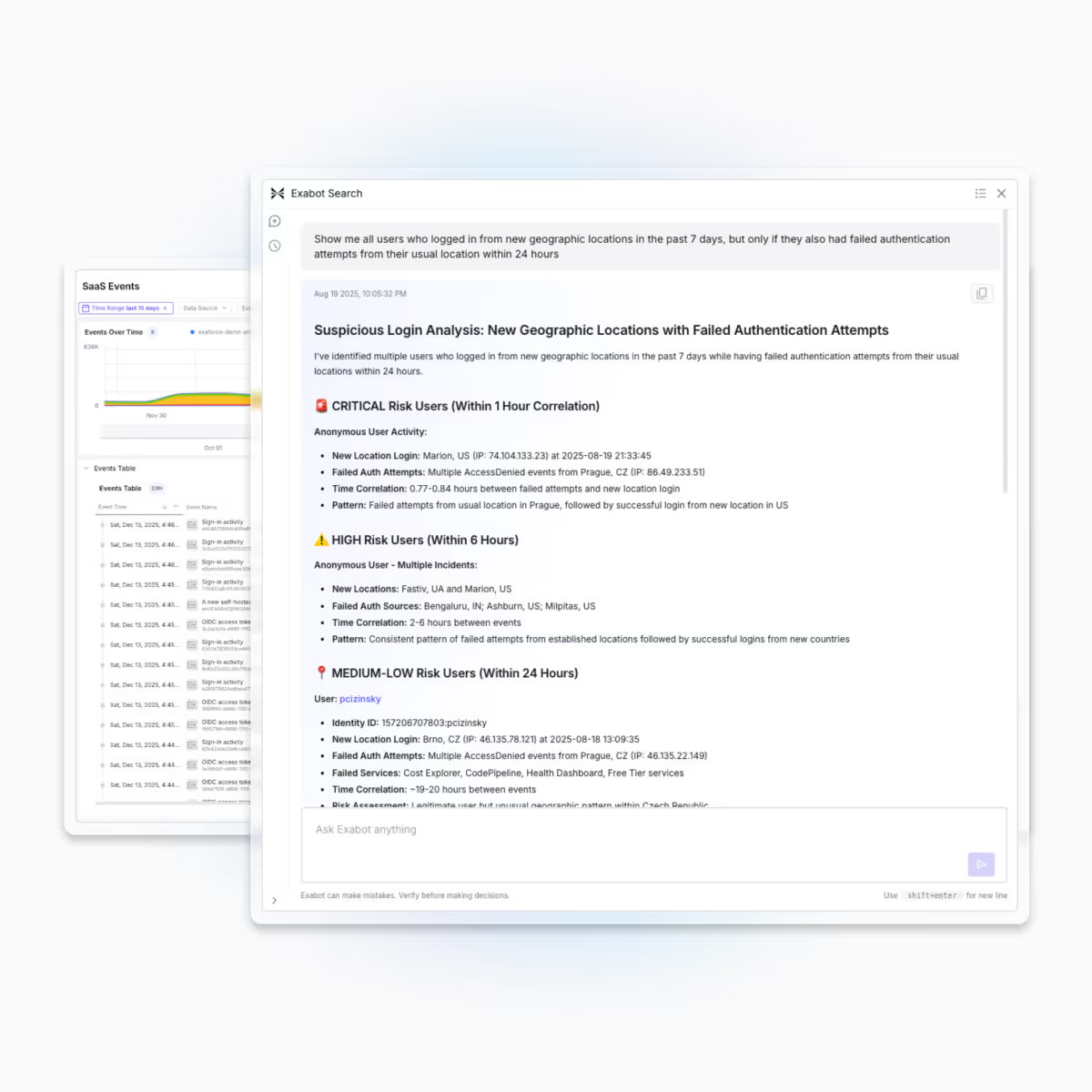
Search across any entity, such as users, endpoints, resources, and events, and ask complex, conversational questions that correlate runtime activity with configuration state. Investigate incidents and threat hunt faster with answers enriched by internet context, including IOC reputation checks, threat intelligence feeds, security research blogs, and vulnerability databases. Every response includes full source attribution for transparency and auditability.

Easier investigations and threat hunts, even in complex scenarios
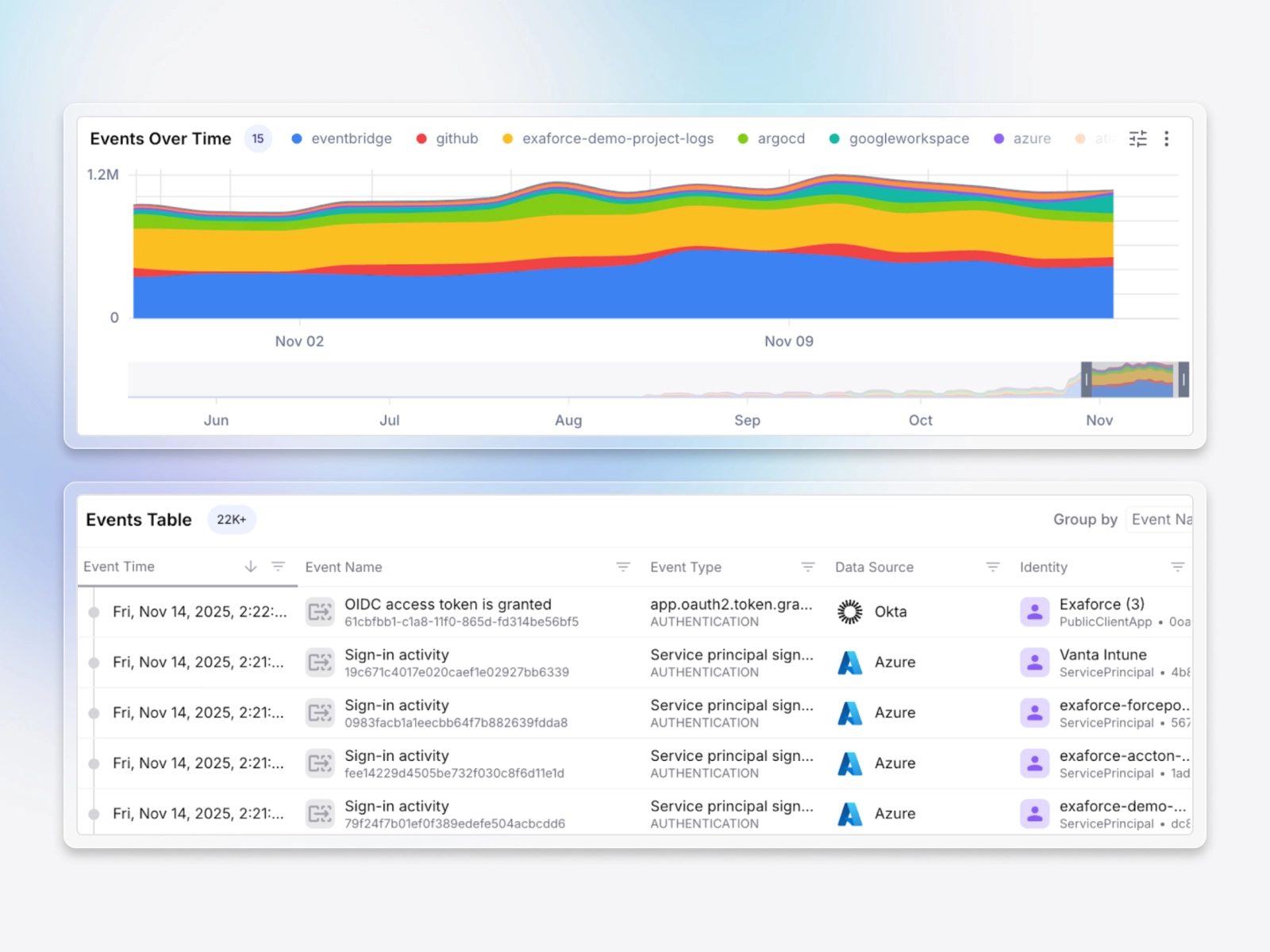
Pre-curated dashboards for every entity automatically surface correlated context. Explore visually with click-to-filter dimensions, drag-to-zoom time ranges, and pivots across related entities. Cross-filter by user, location, resource, and time, then drill from summaries to raw events in one click. Spot suspicious patterns faster and export complete investigations with supporting evidence.

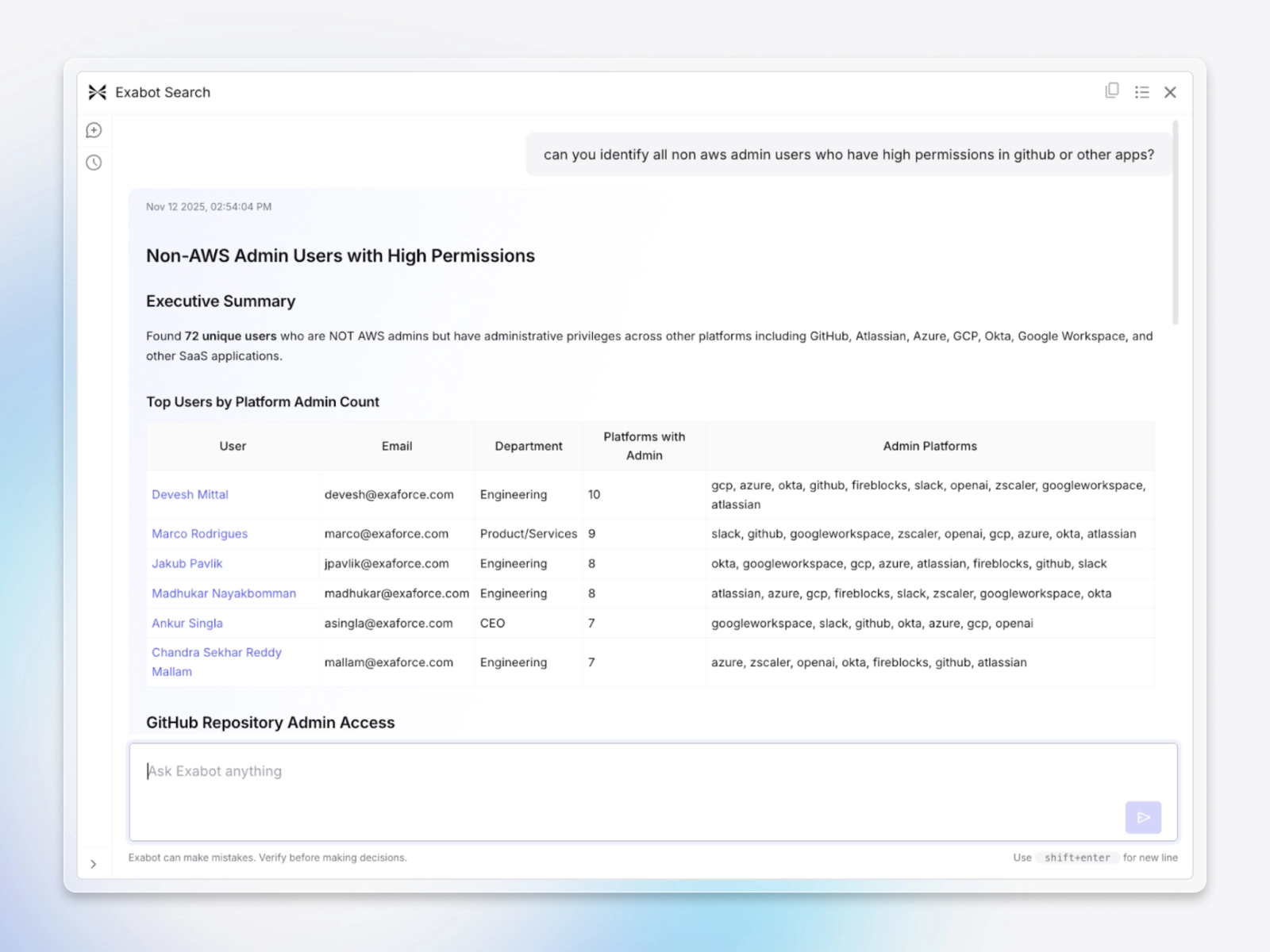
Unified query builder for events and configuration
Build powerful queries without a complex query language using assisted natural language and/or simple dropdowns. Query Builder lets you combine behavioral events and configuration context (identity, permissions, SaaS settings, cloud resources, etc.) into a single query so you can correlate “what changed” with “what happened”.


Featured investigation capabilities
Purpose-built to answer the questions a senior analyst would automatically
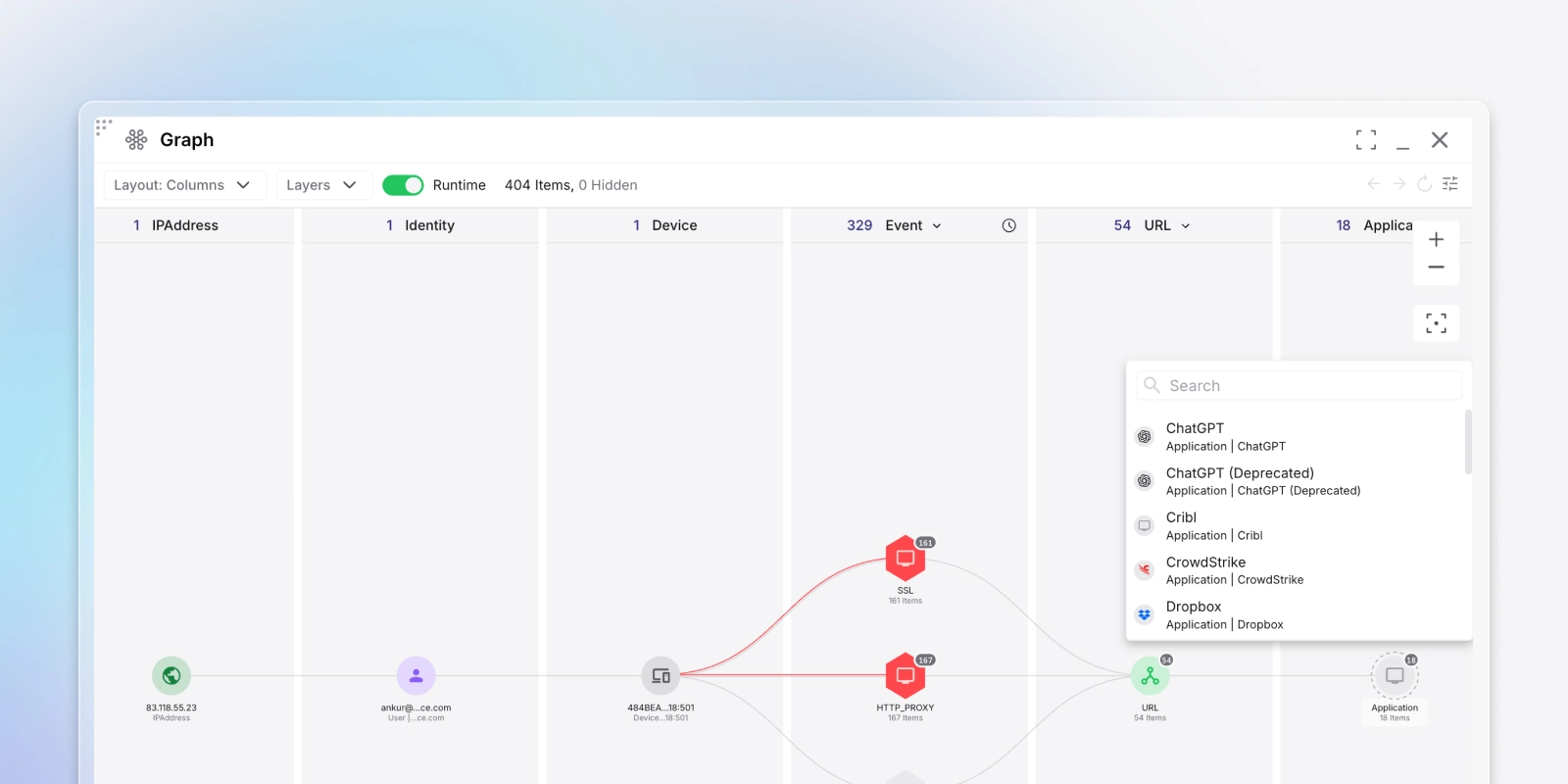

Visual Exploration
Visually explore connected identities, configs, events, resources and more.


Exabot Search
Ask questions in plain English and get answers with linked evidence, no complex query language required.
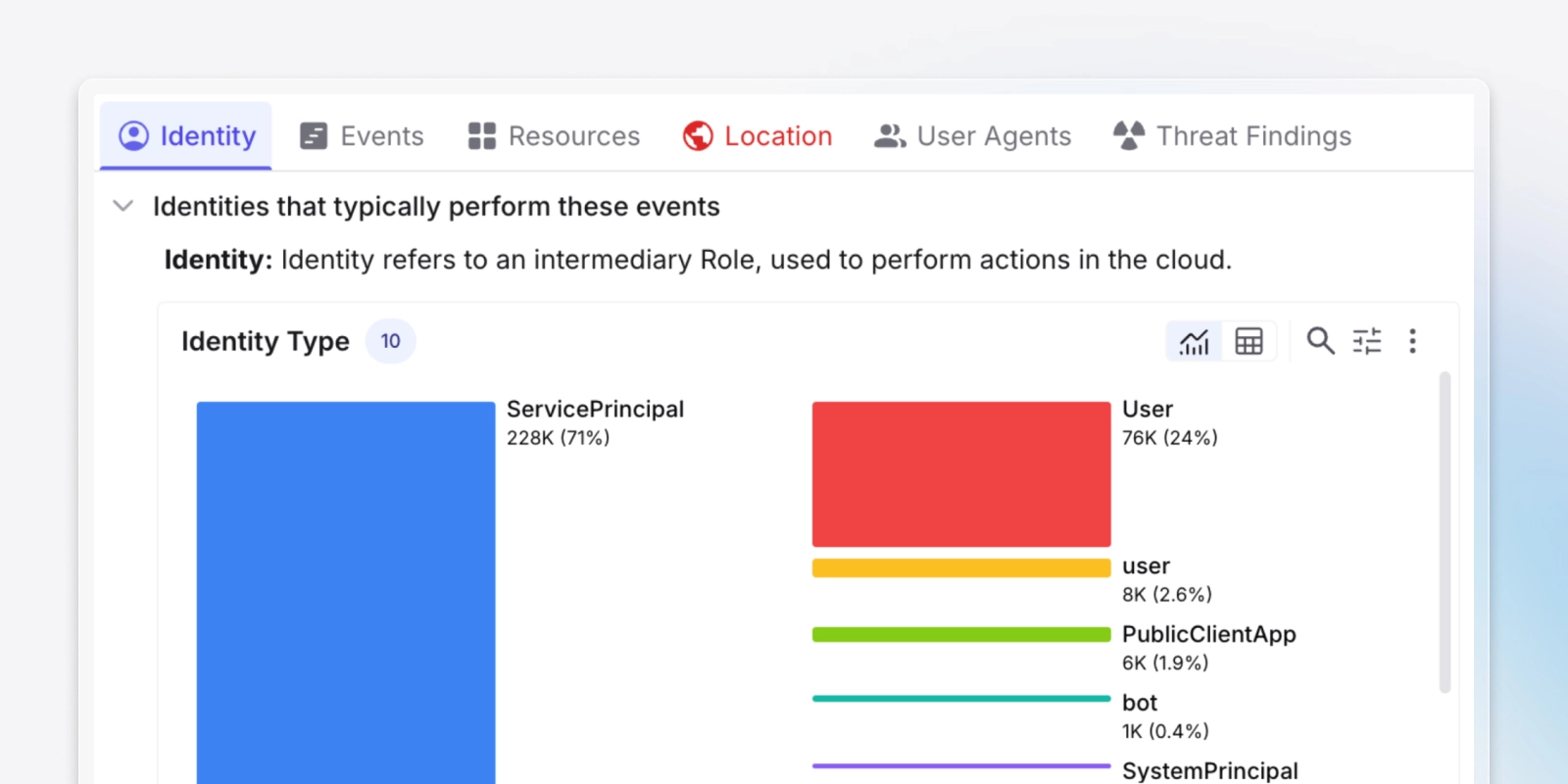

Investigate
Deep dive into sessions, events, resources, and more with intuitive pivoting.
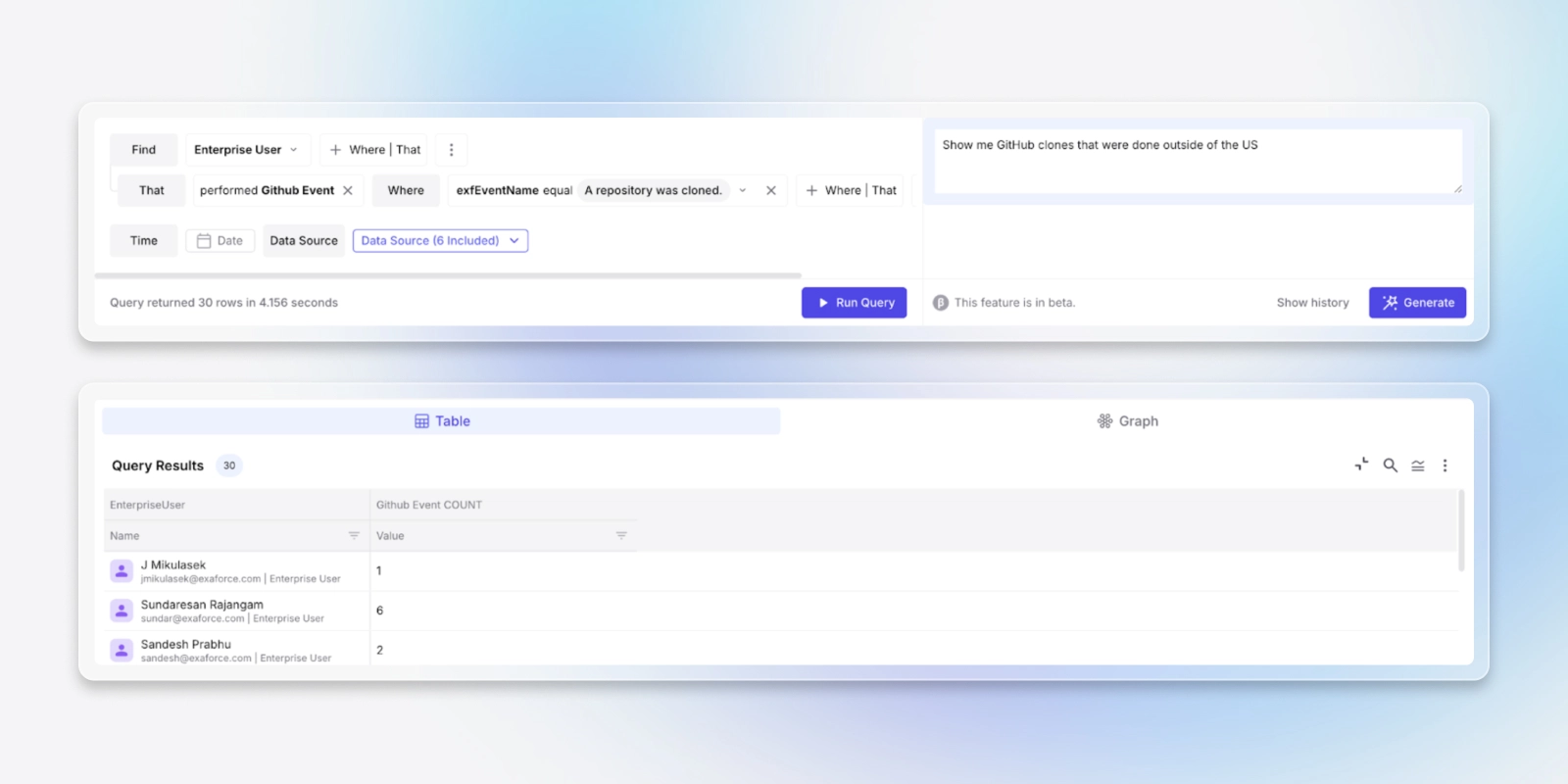

Query Builder
Dig into behavior and events combined with configuration context in a simplified way.
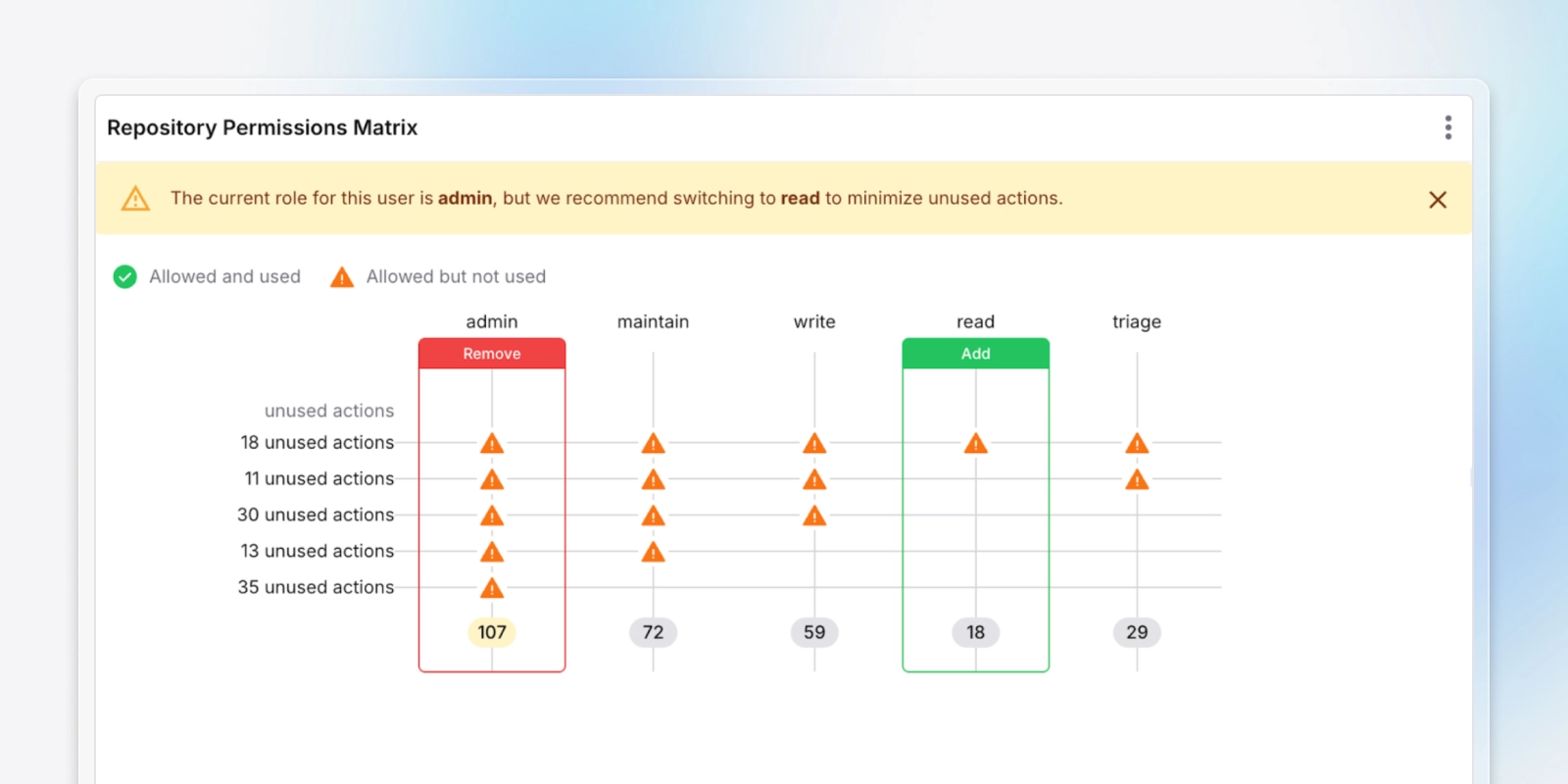

Effective Permissions
Visualize identity chains and effective permissions across cloud and SaaS to show how access was obtained and used.
AI-driven analysis is essential for modern security operations, and Exaforce demonstrates how AI can act as a true investigation partner. The company's platform enables our team to operate with the depth and context that traditionally requires a full SOC and significant manual effort, helping us to scale our security efforts to meet our growing needs.

Frequently asked questions
Yes. Exabots handle the heavy lifting, grouping related alerts, building timelines, answering follow-ups in natural language, cutting investigation time from hours to minutes.
Exabot embeds domain expertise across major security platforms and identity systems, so analysts can ask plain-English questions instead of learning specialized query languages. For example, it can automatically interpret concepts like AWS IAM roles and policies, GCP service accounts, Okta authentication events, and GitHub or Google Workspace permissions. It also gathers and correlates context across systems to eliminate manual lookups, enabling junior analysts to investigate complex incidents immediately without years of platform-specific training.
Every finding includes plain-English rationale, detailed evidence, and complete source attribution (event IDs, entities, resources), with links back to the underlying systems and logs. You can drill down into any entity and see exactly how the conclusion was reached, including the data examined and the underlying query.
Yes, Exabot Investigate operates independently of any SIEM. Exaforce ingests detections and raw signals directly from cloud, SaaS, identity, endpoint, and code sources into a real-time data warehouse, and can also enrich alerts from your existing SIEM. If you have already invested in a SIEM, Exaforce augments it with advanced investigation capabilities it lacks, especially for real-time analysis on the last 90 days of data in our in-memory database, while you can continue to use the SIEM for long-term historical storage.
SIEMs require mastering complex query languages, such as SPL, KQL, SQL, and operate only on log data. You have to manually correlate identity, configuration, and behavioral context across multiple tools. Exabot Investigate provides natural language search and visual exploration across unified data, including logs, identity, config, and baselines. Investigations that take 30-60 minutes in traditional SIEMs take 3-5 minutes in Exaforce, with complete context automatically correlated.
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you