Triage faster with more signal and less noise
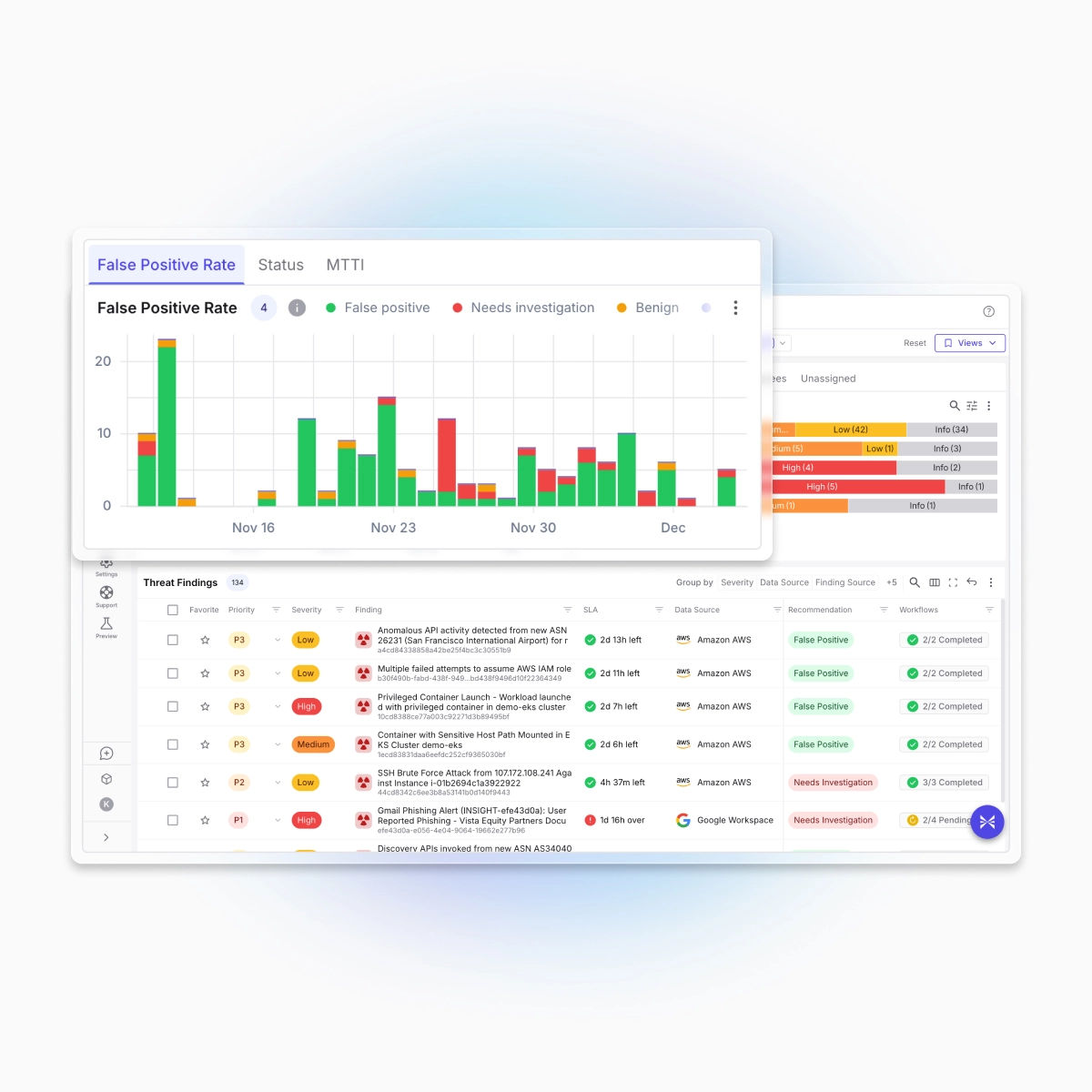
Intelligent triage that reduces false positives and MTTI
Exabot Triage correlates signals across IaaS, SaaS, identity, endpoints, code, and third-party tools like Splunk and CrowdStrike. It performs Tier 1-3 analysis in minutes by suppressing false positives, prioritizing with your business specific context, and routes the right work to the right owner.
Reduced false positives and noise
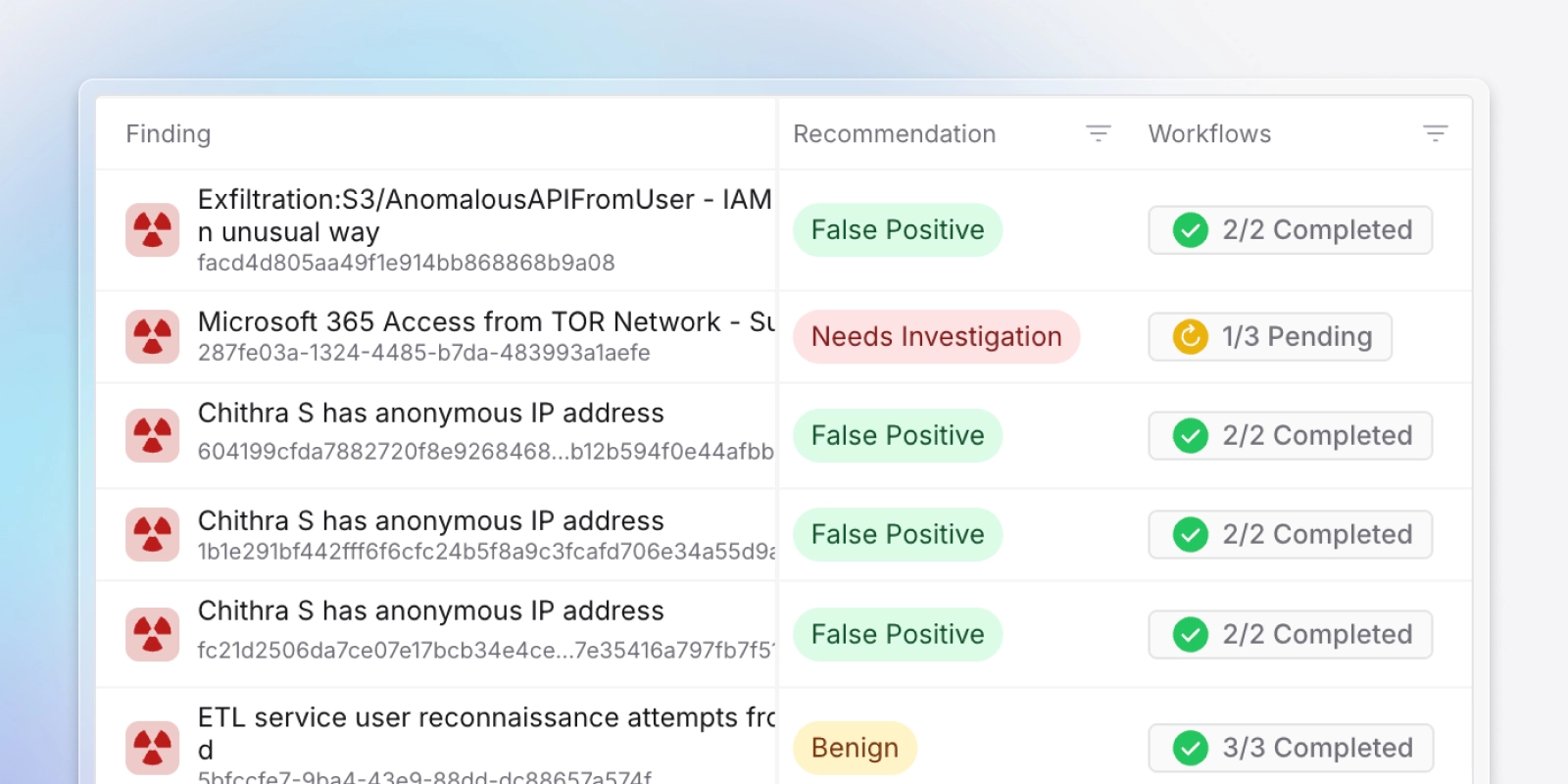
Exabot Triage collapses related alerts across SIEMs, EDRs, network security tools, and more into a single finding, removes duplicates, and applies environment‑aware analysis, historical analysis, and Business Context Rules to filter out false positives and benign activity, cutting irrelevant alerts by up to 80% so analysts focus on distinct, high‑value work.
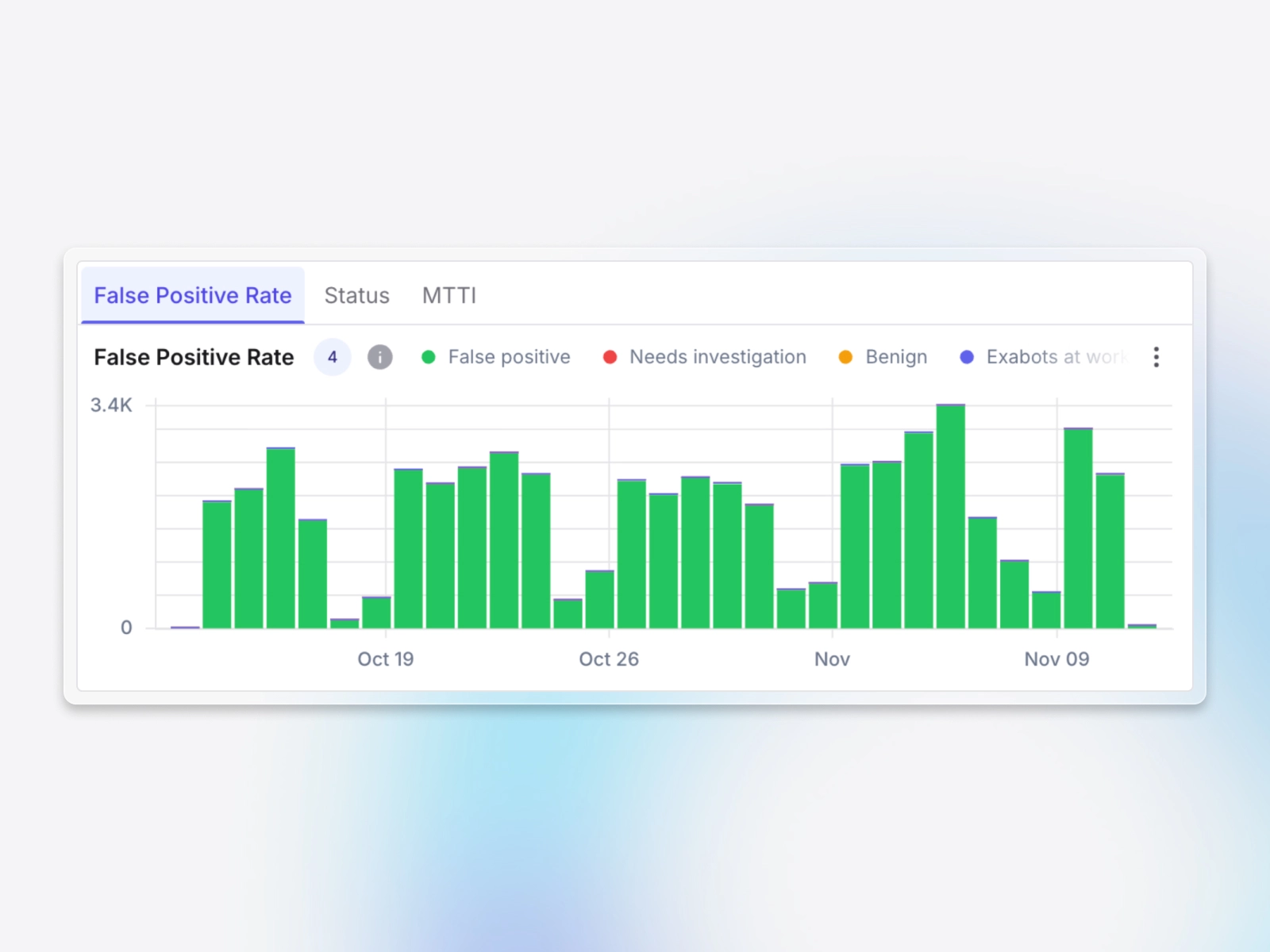

Deep contextual enrichment across your stack
Exabot pulls identity, session, configuration, and activity data from cloud, SaaS, AI, code, and endpoint systems to answer the design time questions the agents generates, the same critical questions a senior analyst would ask: who, what, where and how, and whether the activity matches normal behavior, then prioritizes the alert and summarizes the investigation for rapid triage.

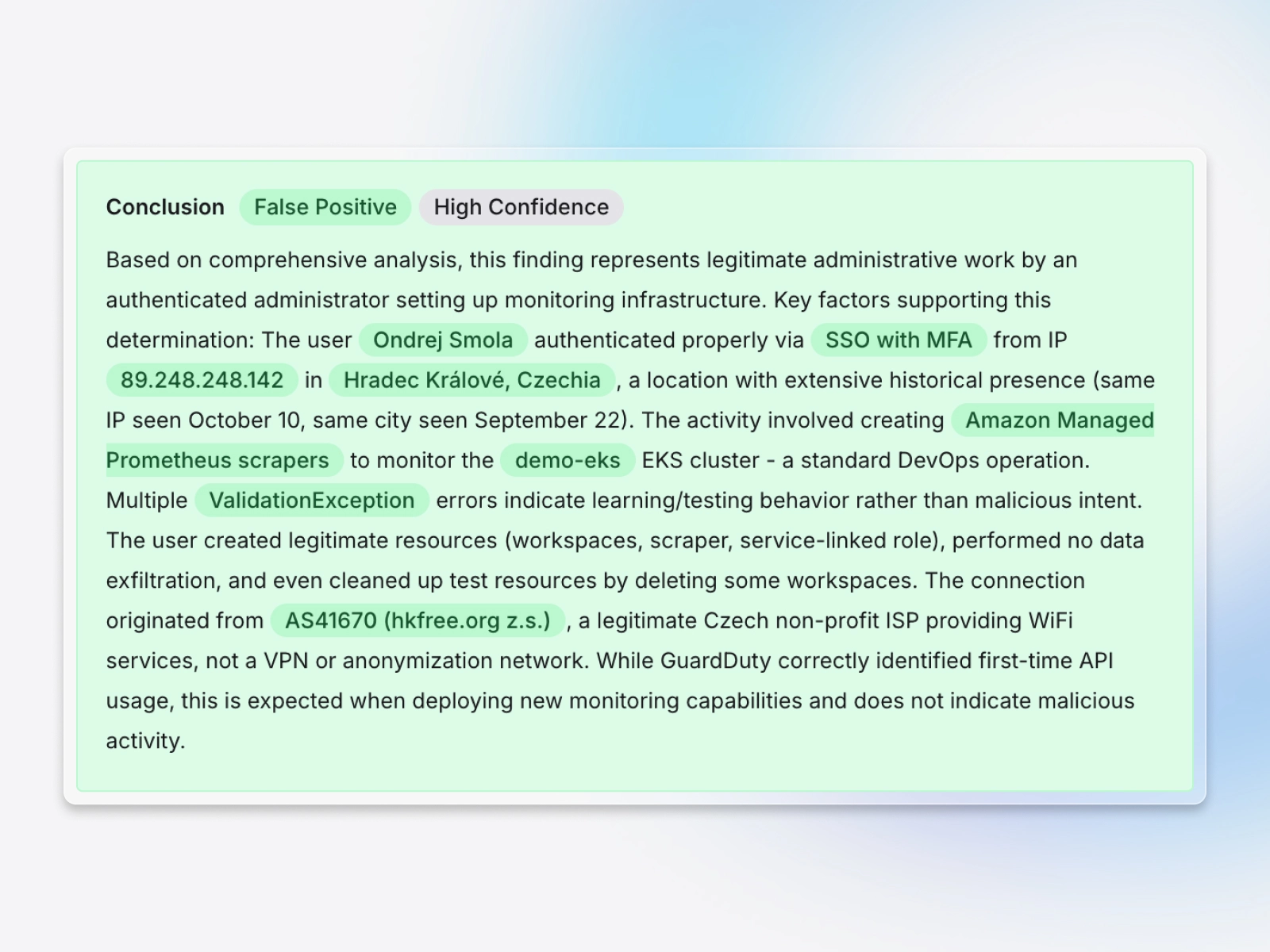
Explainable decisions you can trust
Every triage outcome includes a concise, plain English rationale, the key indicators that drove the decision, the affected principals and resources, and links to logs and evidence. Your analysts and auditors can see exactly why an alert was marked as a false positive, benign, or escalated and resolved.

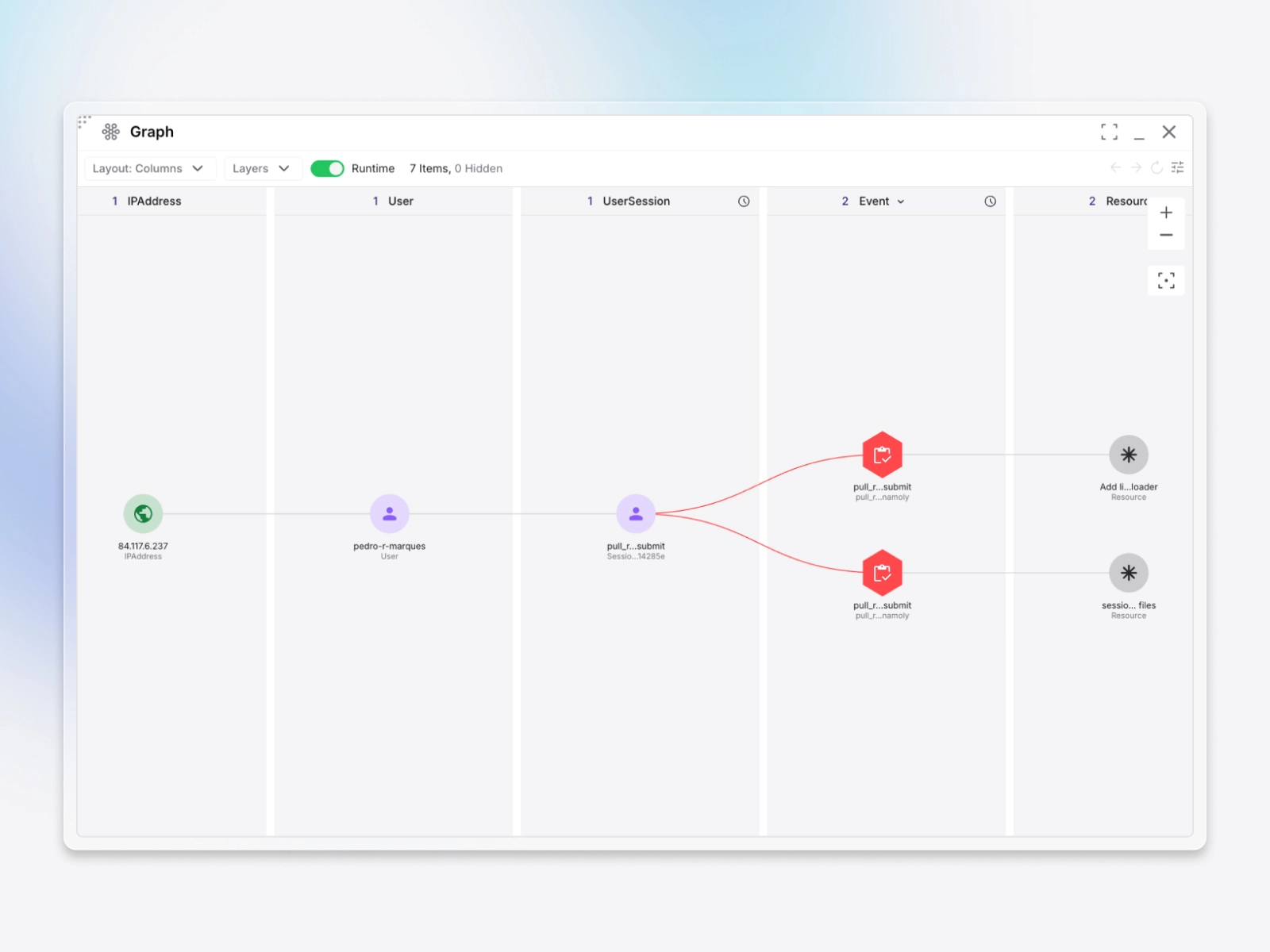
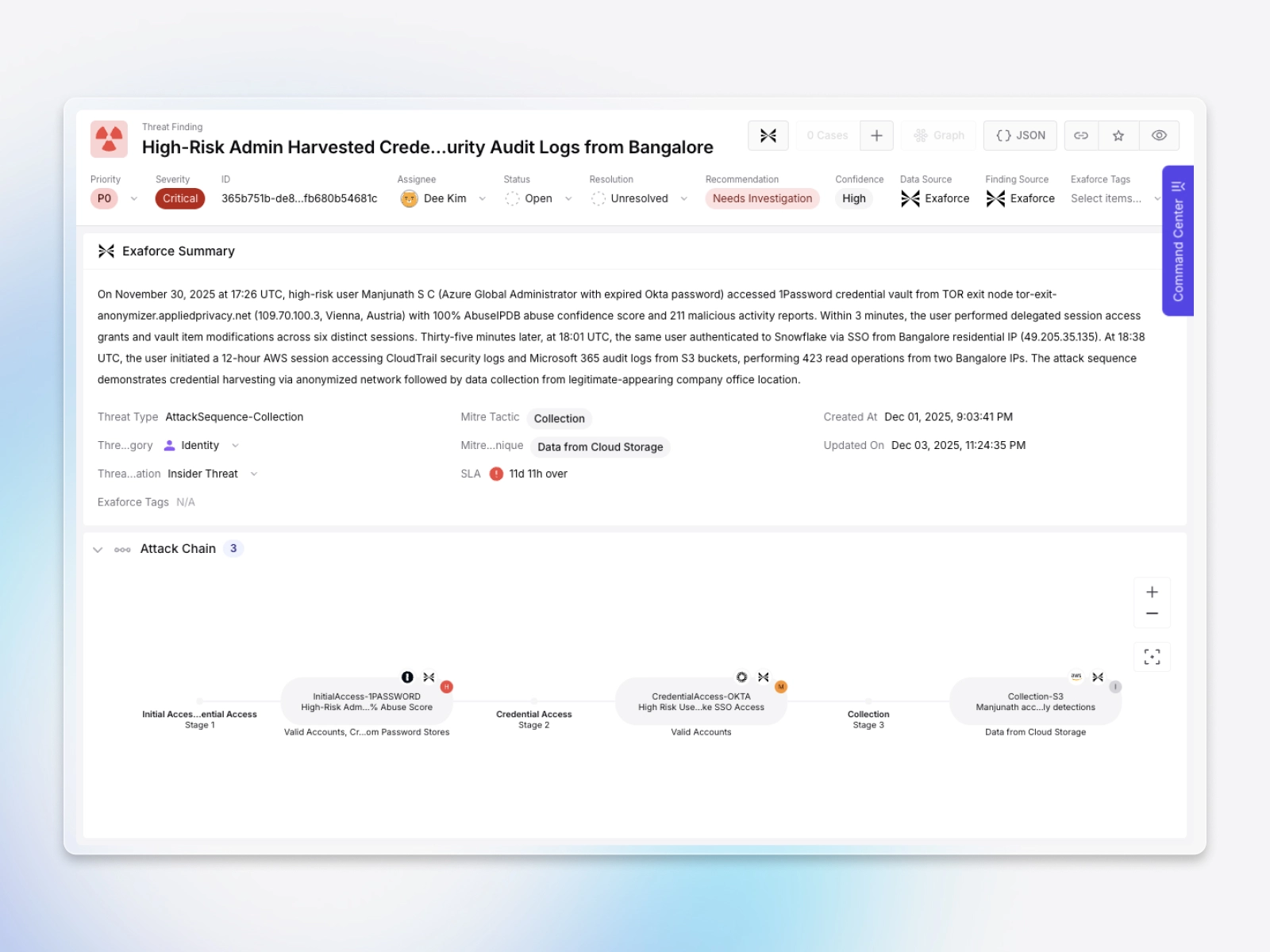
Attack Chains that stitch alerts into a single attack story
Exaforce automatically builds Attack Chains by correlating related alerts across your SIEM, identity providers, EDR, email/phishing tools, and Exaforce Detections into one end to end story with evidence and pivots back to the source, so analysts can see the full sequence of activity from initial access to escalation to lateral movement to impact and hand off a complete narrative in minutes.

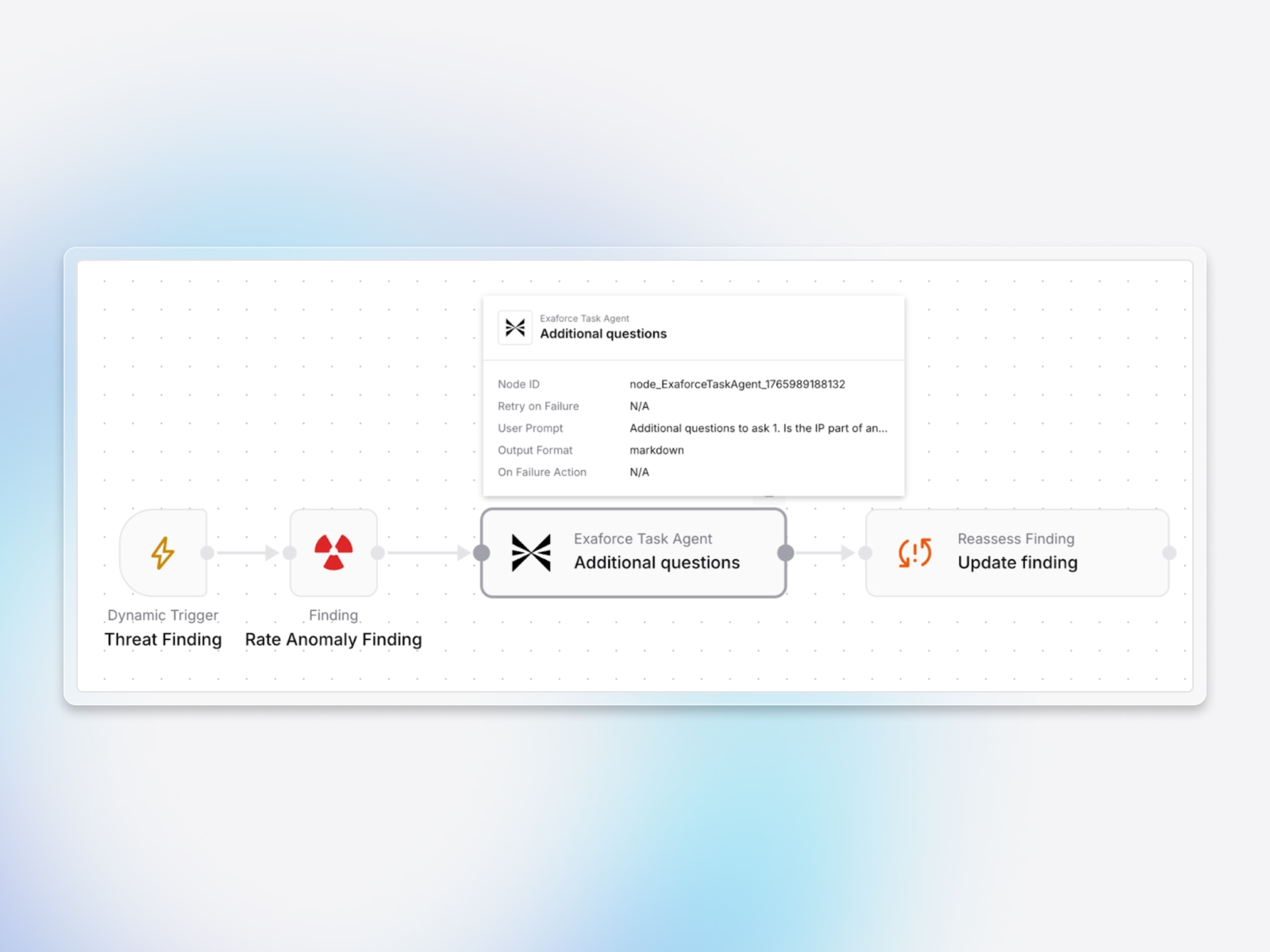
Customizable triage logic
Extend Exabot's investigation with custom questions tailored to specific alert types. Add questions that gather organization-specific information, improving triage fidelity, reducing false positives, and encoding investigative knowledge from your most experienced analysts.

Featured triage capabilities
Purpose‑built to reduce noise and accelerate decisions

Noise reduction engine
Automated false‑positive reduction and duplicate suppression
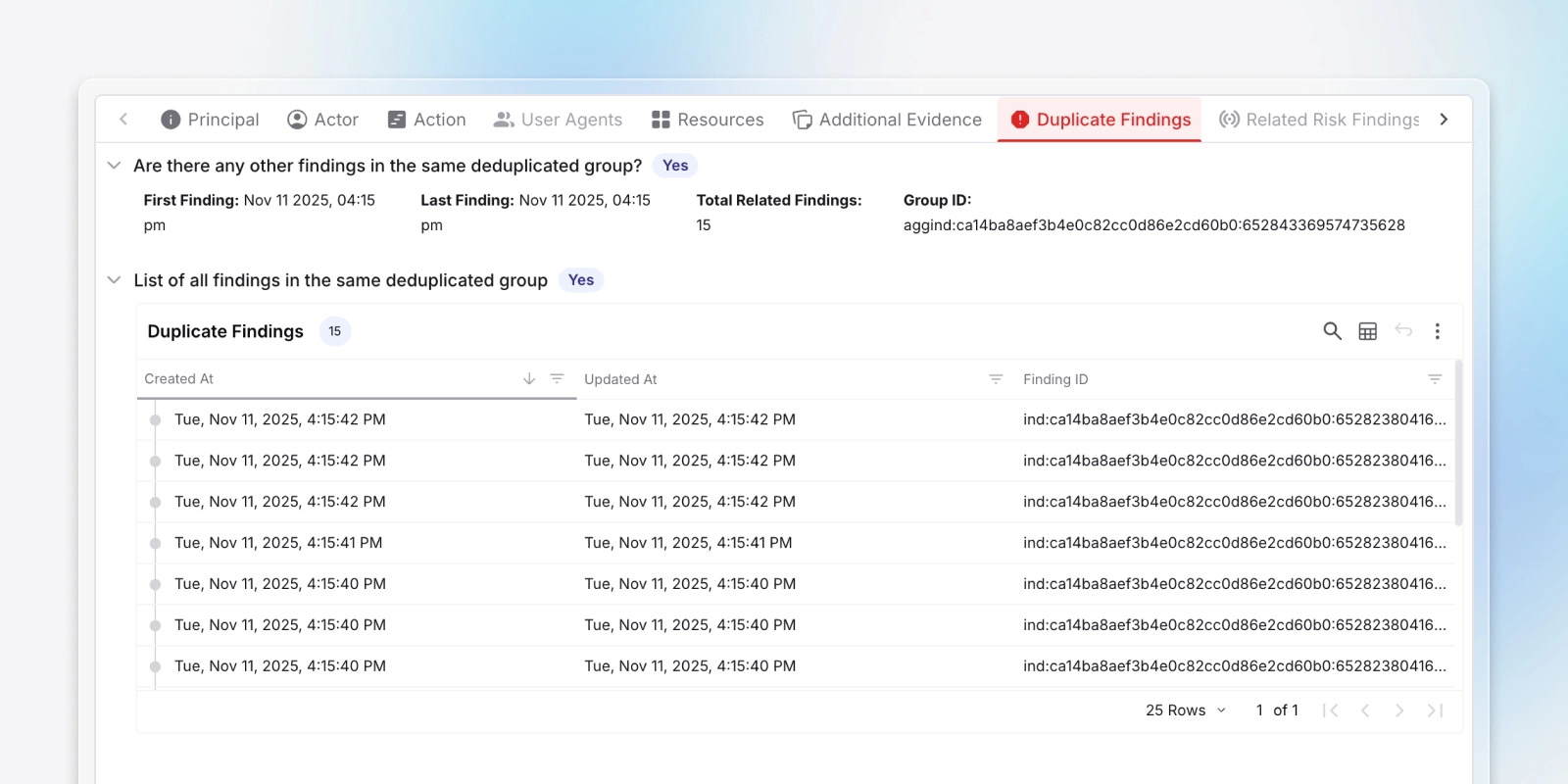

Deduplicate findings
Deduplicate multiple alerts with the same root cause to reduce redundant work
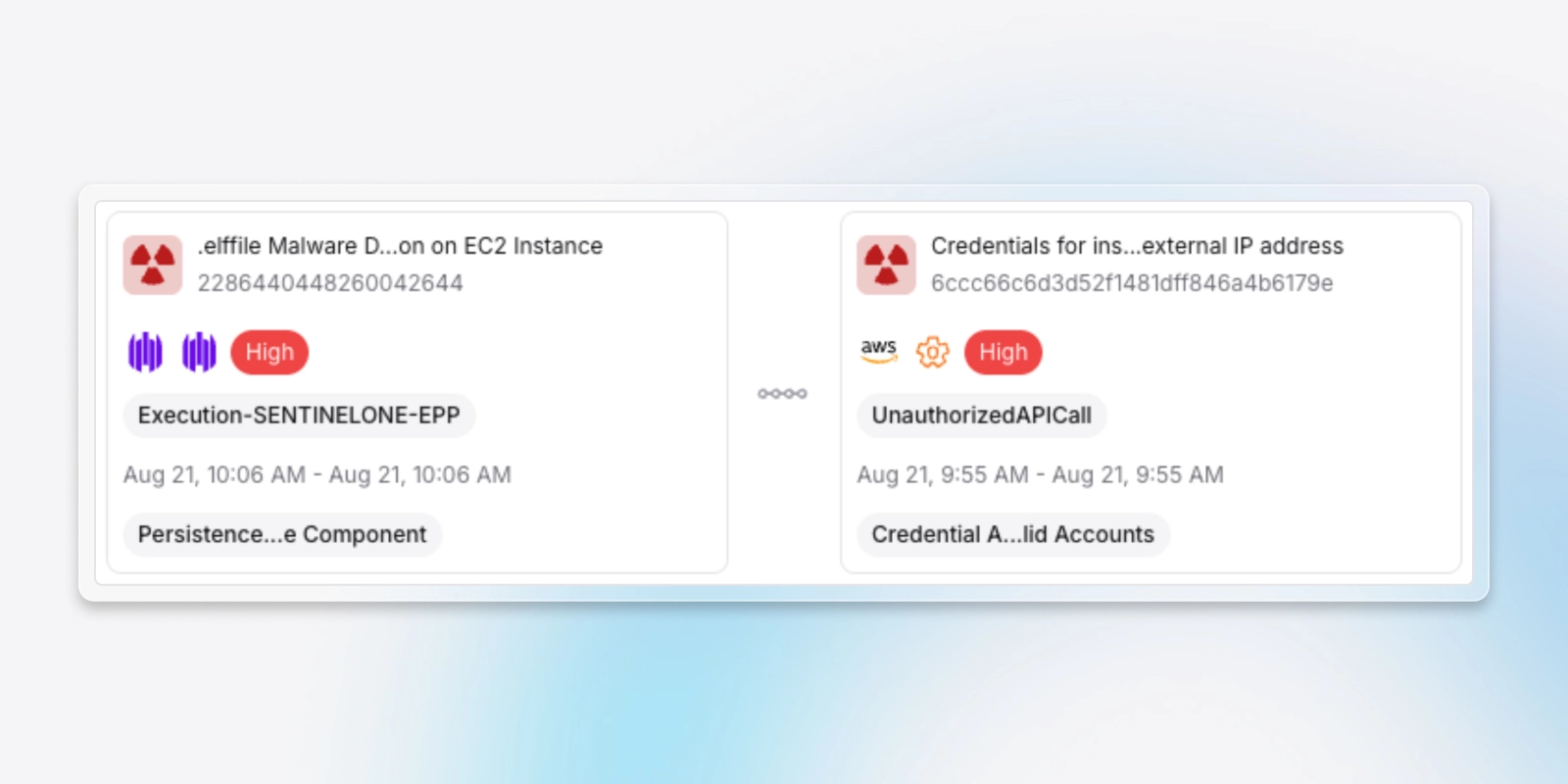

Attack chains
Chaining threats across multiple sources to tell the full attack story
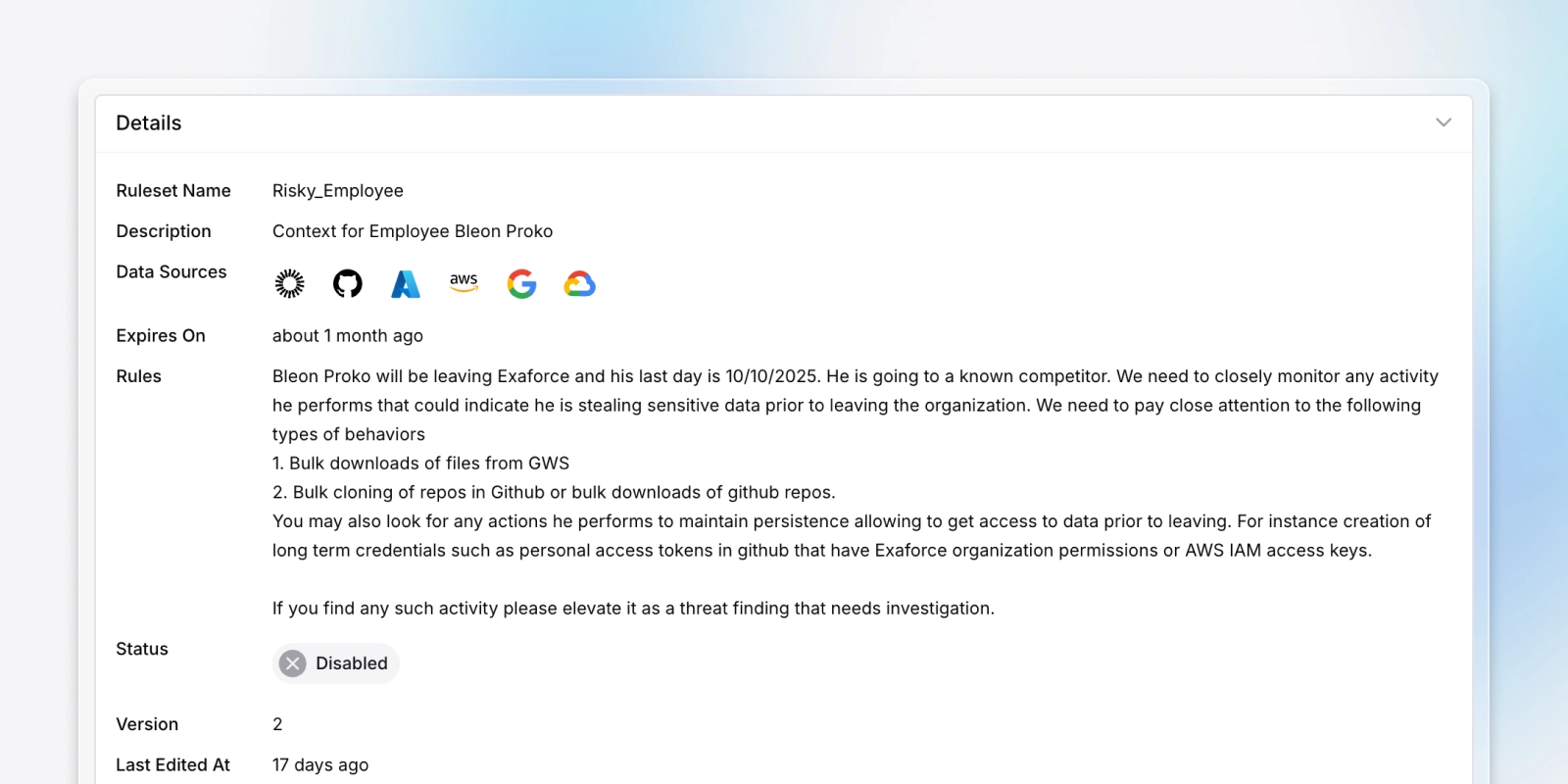

Business Context Rules
Encode environment‑specific knowledge to cut benign alerts and triage with context specific to your environment


Historical analysis
Use prior results captured in the Knowledge Model to continuously improve analysis and recommendations
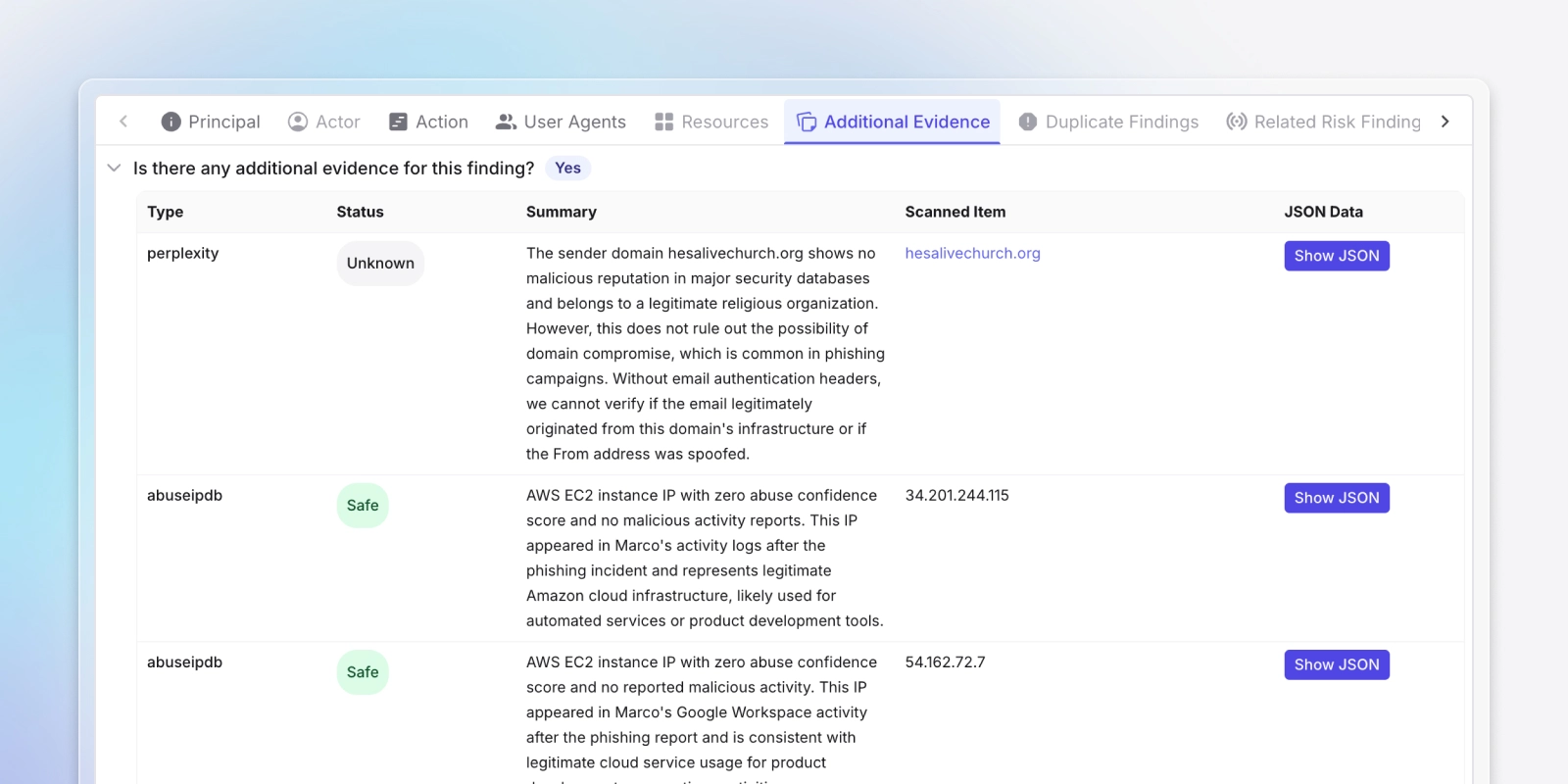

Enrichments from 3rd party intelligence sources
Automatically adds context from Perplexity and threat intelligence feeds like AbuseIPDB to every alert
CFS utilizes the Exaforce Agentic SOC platform, which has contributed to reducing investigation times, in some cases from hours to minutes. The platform's auto-triaging of alerts has significantly reduced manual effort, saving valuable time. For the past year, Exabots have provided 24x7 MDR capabilities, continuously monitoring our environment and supporting our security engineering & operations teams.

Frequently asked questions
Based on your specific risk tolerance you can choose to automatically close false positive alerts by leveraging our automation agents or keep them and close them manually. You can define the characteristics of the type, severity and priority of alerts to automatically close using our automation agents.
When alerts escalate to Tier 2/3, Exabots provide a complete investigation starting point above and beyond raw alerts. Analysts receive enriched context with identity resolution, session timelines, resource relationships, behavioral anomaly scores, and links to source logs, eliminating hours of manual context gathering. Investigation dashboards show entity graphs, related findings, and historical similar cases. Analysts can pivot directly into Exabot Investigate for deeper threat hunting with all context preserved, ask follow-up questions in natural language, and access the full audit trail of Exabot's reasoning. Handoffs become seamless, and L2/L3 analysts act immediately instead of rebuilding context from scratch.
Yes, all analyst actions (verdict changes, close reasons) are documented and fed into historical analysis. For every new alert, Exabot performs similarity matching against past investigations to identify comparable scenarios and their outcomes. If analysts consistently mark certain alert patterns as false positives or escalate specific combinations, future triage decisions incorporate these learnings automatically. This continuous feedback loop improves recommendation accuracy, reduces false positives unique to your environment, and aligns AI decisions with your team's institutional knowledge without manual model retraining.
Exabot enriches every alert with comprehensive context from our Semantic and Behavioral models, such as identity details, resource relationships, and baseline comparisons, so only alerts that truly require human judgment require analyst attention. It automatically deduplicates related alerts from multiple tools, groups findings into unified attack chains, prioritizes based on your business context (e.g., common behavior patterns in your environment), and clearly marks false positives with supporting evidence. Analysts receive fewer, higher-quality investigations rather than drowning in noise.
Yes. Exabot Triage operates on data ingested directly from your cloud, SaaS, identity, endpoint, and code sources through our integrations. Our Semantic and Behavioral models provide all the necessary context for high-fidelity triage, including entity resolution, relationship mapping, baseline comparisons, and anomaly scoring. This architecture delivers predictable, precise outcomes without depending on a SIEM. When beneficial, Exabot can query external SIEMs for low volume data and deterministic data.
Traditional SOARs enrich alerts after they fire, executing playbooks to gather additional context. Exabot Triage fundamentally improves alert fidelity by understanding the semantics of each alert and automatically enriching it with relevant context from our Semantic and Behavioral models, answering investigative questions much like a senior analyst would. It correlates threat findings across multiple data sources to construct complete attack narratives, deduplicates related alerts, and applies environment-specific context to prioritize and reduce false positives. The result is fewer alerts that require human oversight, as most have been thoroughly investigated with clear recommendations.
Explore how Exaforce can help transform your security operations
See what Exabots + humans can do for you













