A day in the life of a SOC analyst on triage duty
Imagine starting your workday faced with a barrage of security alerts, each signaling a potential threat to your organization's data and systems, but only if you find the needle in the haystack of findings. As a triage analyst, your first task is to monitor these incoming alerts from security information and event management (SIEMs), endpoint detection and response (EDR), intrusion detection systems (IDS), email security, and more. And those are just the security tools. As an analyst, you should also make sure to dig into the raw logs from network tools, identity providers, and more. Visibility across endpoints, networks, cloud platforms, and SaaS applications is critical, yet managing this extensive data can be overwhelming.
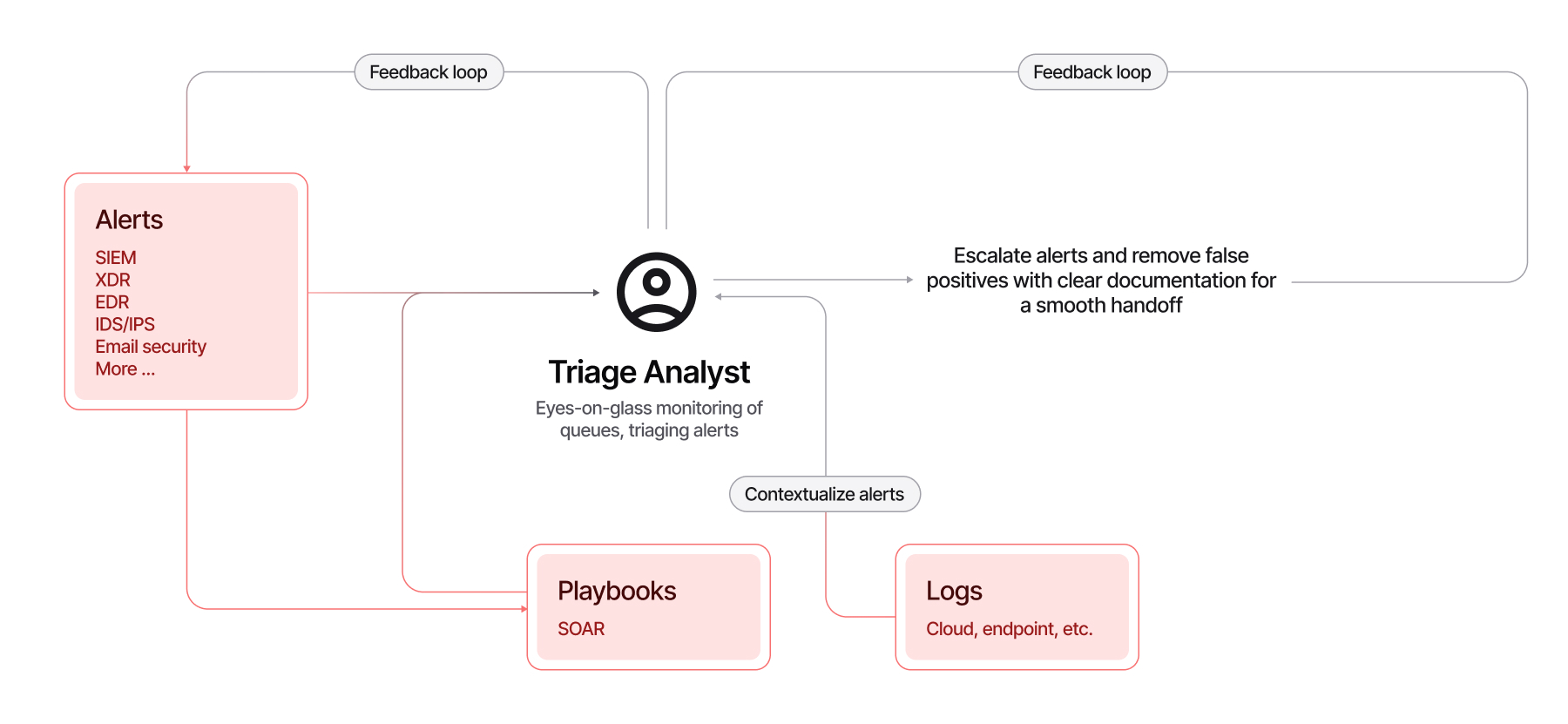
After intake, the initial review is essential. Analysts spend a considerable amount of their time verifying alerts to filter out false positives, confirming log sufficiency, and ensuring quality evidence for deeper investigations. Prioritization follows, classifying each alert by severity (critical, high, medium, or low) and priority based on urgency, impact, and asset sensitivity.
Enriching these alerts through additional context and correlation is another time-intensive step. Analysts must gather more information from various systems and logs, cross-reference affected entities against known user behavior or prior incidents, and identify patterns that indicate larger attack campaigns or benign events like the CEO traveling. This process can be tedious and error-prone due to disconnected tools and inconsistent data formats.
Incident classification, basic response, containment, and escalation require meticulous documentation and clear communication among teams. Ensuring a smooth handoff between Level 1 analysts performing initial triage and advanced Level 2 or 3 analysts is often a challenge in traditional SOC processes. Most often, AI is used to automate repetitive Tier 1 work; however, significant bottlenecks and stress arise from alert escalation to Tier 2 or Tier 3 analysts, where a lack of expertise and insufficient data lead to poor contextualization.
Challenges facing triage analysis today
Triage analysts face several persistent challenges that hinder their efficiency and effectiveness. Existing solutions (SIEMs, SOARs, etc.) are not designed to handle these challenges, instead exacerbating the situation by becoming increasingly noisy and rigid:
- High false positive rate wastes time: Tier 1s must wade through alerts that are often irrelevant, up to 99% in some cases, leading to alert fatigue and time loss.
- Fragmented tools make triaging and enrichment slow and manual: Tier 1 analysts must piece together context from disconnected security and non-security systems, correlating logs, enriching alerts, and investigating manually, all of which slows response and increases error rates.
- Unrealistic skill demands on junior analysts: Triaging often spans cloud, identity, endpoint, Kubernetes, SaaS, and more, requiring broad technical knowledge that's hard to expect from entry-level talent.
- Lack of feedback stifles improvements: Without feedback from downstream teams or visibility into case outcomes, Tier 1 analysts struggle to improve accuracy over time. Similarly, Tier 1 analysts can struggle to provide quality feedback upstream to improve detections for fear of not providing good or accurate analysis.
- Increased pressure from understaffed teams: Staffing gaps push more alerts onto fewer shoulders, compounding all of the above issues. For many organizations, this alone can push having a SOC out of reach.
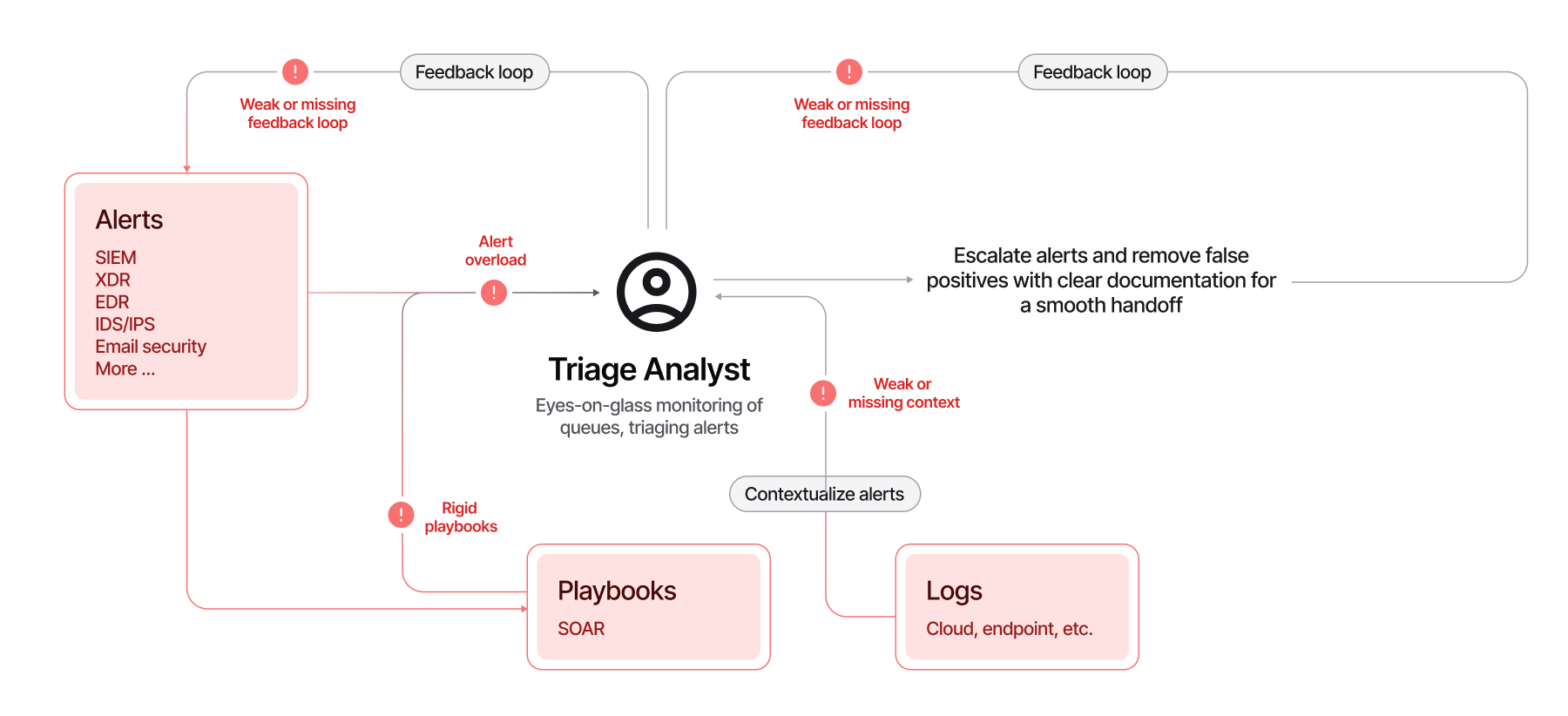
These challenges underscore the critical need for a more streamlined, intelligent approach to triaging alerts in the SOC, not just for the high-volume, routine work of Tier 1, but for the tough, often-escalated cases that traditionally land with Tier 2 and Tier 3.
Transforming triage with AI-powered automation
Recent advancements in AI (GenAI and ML) create an opportunity to fundamentally change the triage process and the role of analysts in triaging. We built Exaforce from the ground up to leverage these advancements to improve the whole SOC lifecycle, including the triage, investigation, and response processes.
Reducing noise with automatic false positive reduction
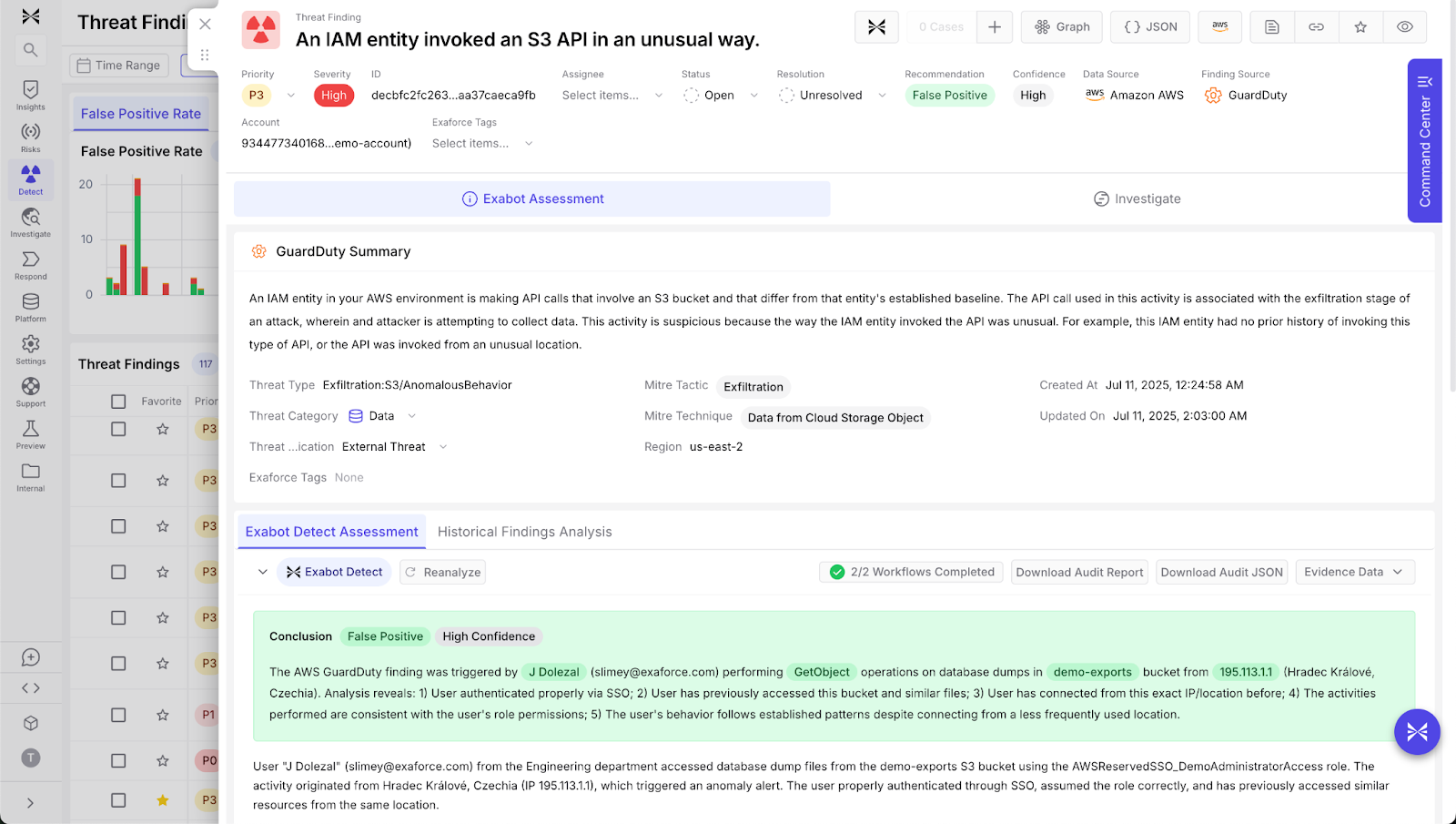
Exaforce reduces noise faced by analysts by automatically identifying and marking false positives. It integrates logs, configurations, identities, threat intelligence feeds, and even code repository configurations to provide highly accurate initial analysis. Leveraging multiple AI techniques, Exaforce can further reduce the alert volume by deduplicating like alerts and chaining related findings, even across systems and tools.
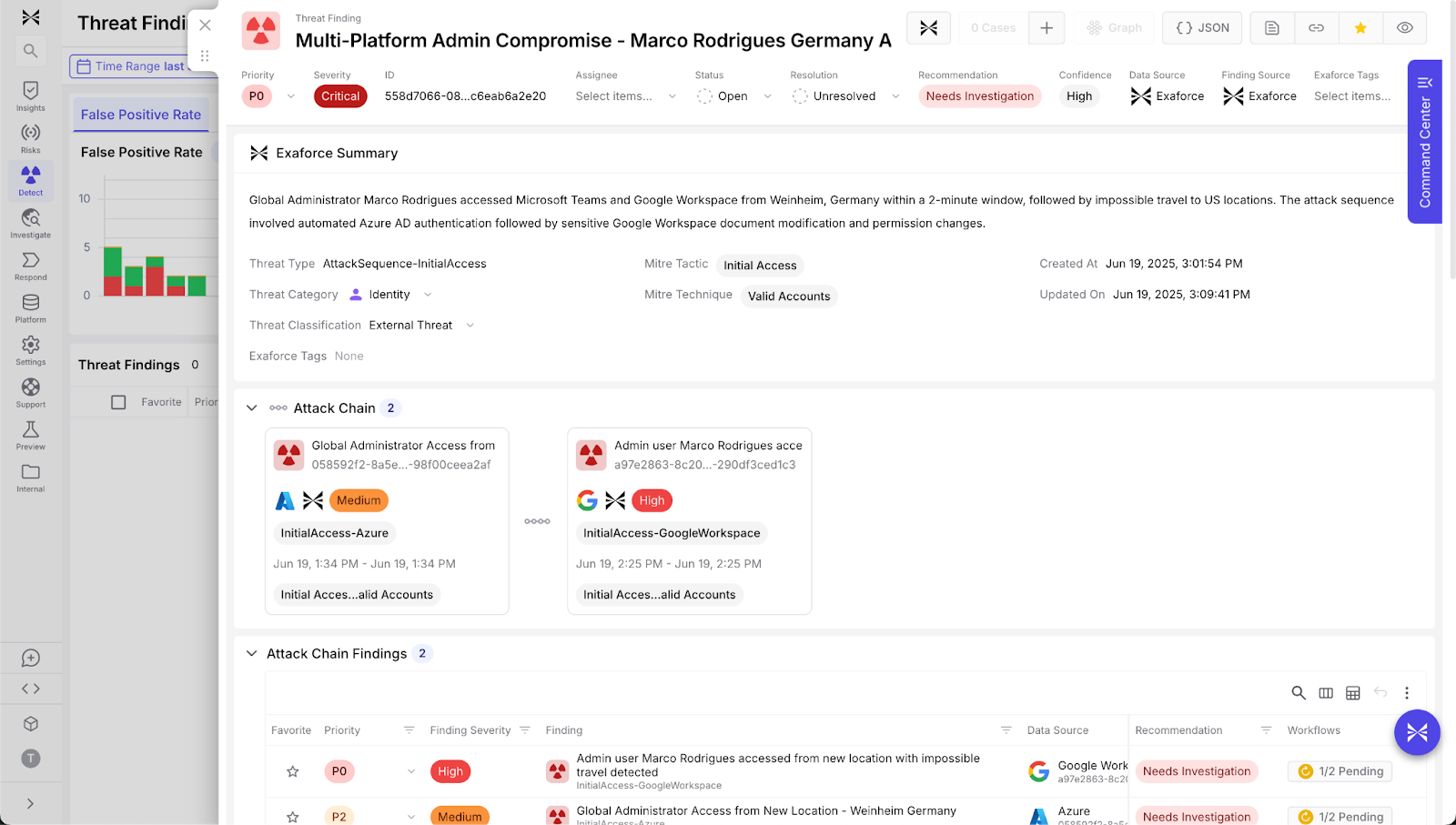
Analysts receive clear summaries outlining the reasoning behind each decision, encompassing details about the principal, understanding of the user and entity locations, all actions taken during the session, details about the resource, and deep behavioral analysis of users and their peers’ behaviors. For example, when AWS GuardDuty flags suspicious user activity, Exaforce's triage agent evaluates multiple indicators like user identity, session details, location of the user, and resource naming conventions to discern if it’s a genuine threat or a benign event such as a test scenario.
Quick workflows with automated human-in-the-loop
This is where Exaforce, as an integrated platform, blurs the lines between triage and response. Exaforce automates analyst workflows through integrated channels like Slack to quickly confirm suspicious behaviors directly with users and managers. This reduces analyst burdens significantly, eliminating manual investigative tasks for straightforward confirmations, accelerating response times, and allowing analysts to concentrate on more complex issues.
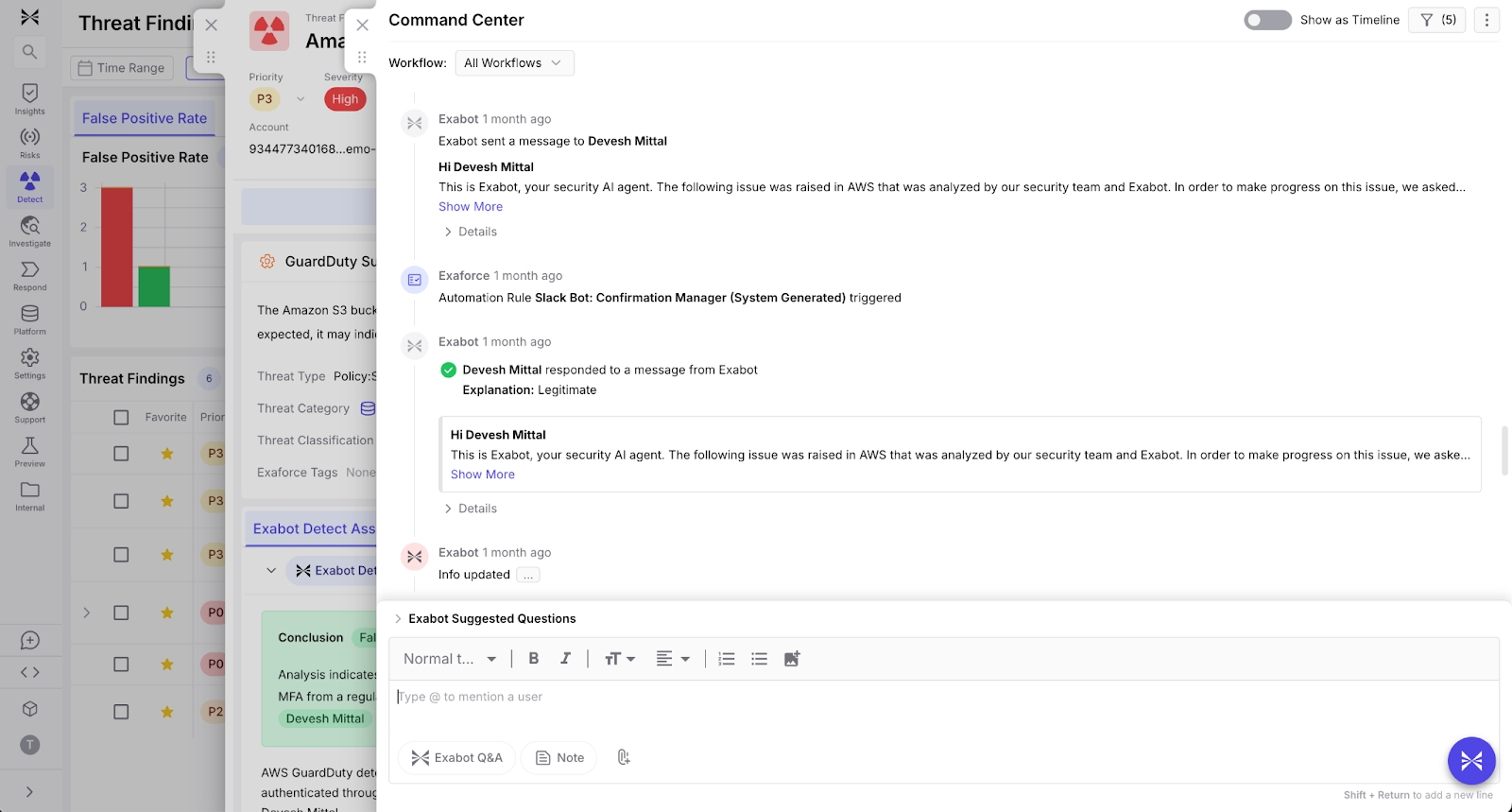
Continuous learning and contextual customization
Exaforce learns continuously by incorporating historical context and analyst feedback. Previous alerts that were deemed “Needs Investigation” and moved to “False Positive” will be added to the context for all subsequent alerts’ analysis, improving the accuracy of the triage. When an alert that was first tagged Needs Investigation is later cleared as a False Positive, that outcome becomes part of the AI history, refining how future alerts are scored. The engine also cross‑references the results of similar alerts, even those that ultimately followed the original resolution, to give every new alert a richer, context‑aware assessment.
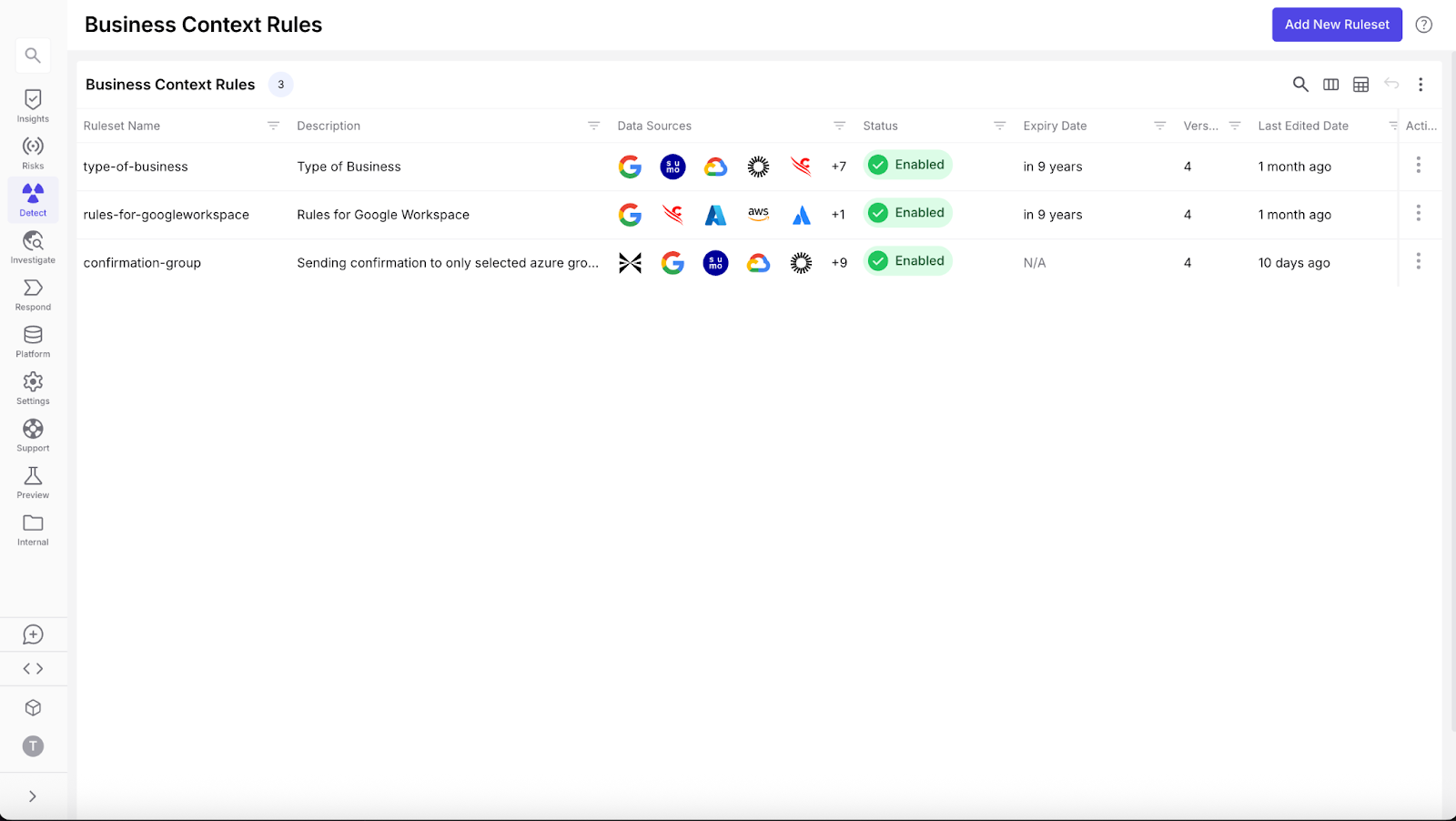
Organizations can also add customized Business Context Rules directly into the platform, tailoring the triage and response processes specifically to their operational and risk profiles, resulting in increasingly accurate and relevant threat detection. For example, at a leading biotechnology provider, the business context includes a list of known-safe VPN gateway IPs. When users switch between these IPs, such as between corporate VPN gateways, Exabots recognize this behavior as expected, rather than flagging it as impossible travel, reducing false positives without compromising detection fidelity.
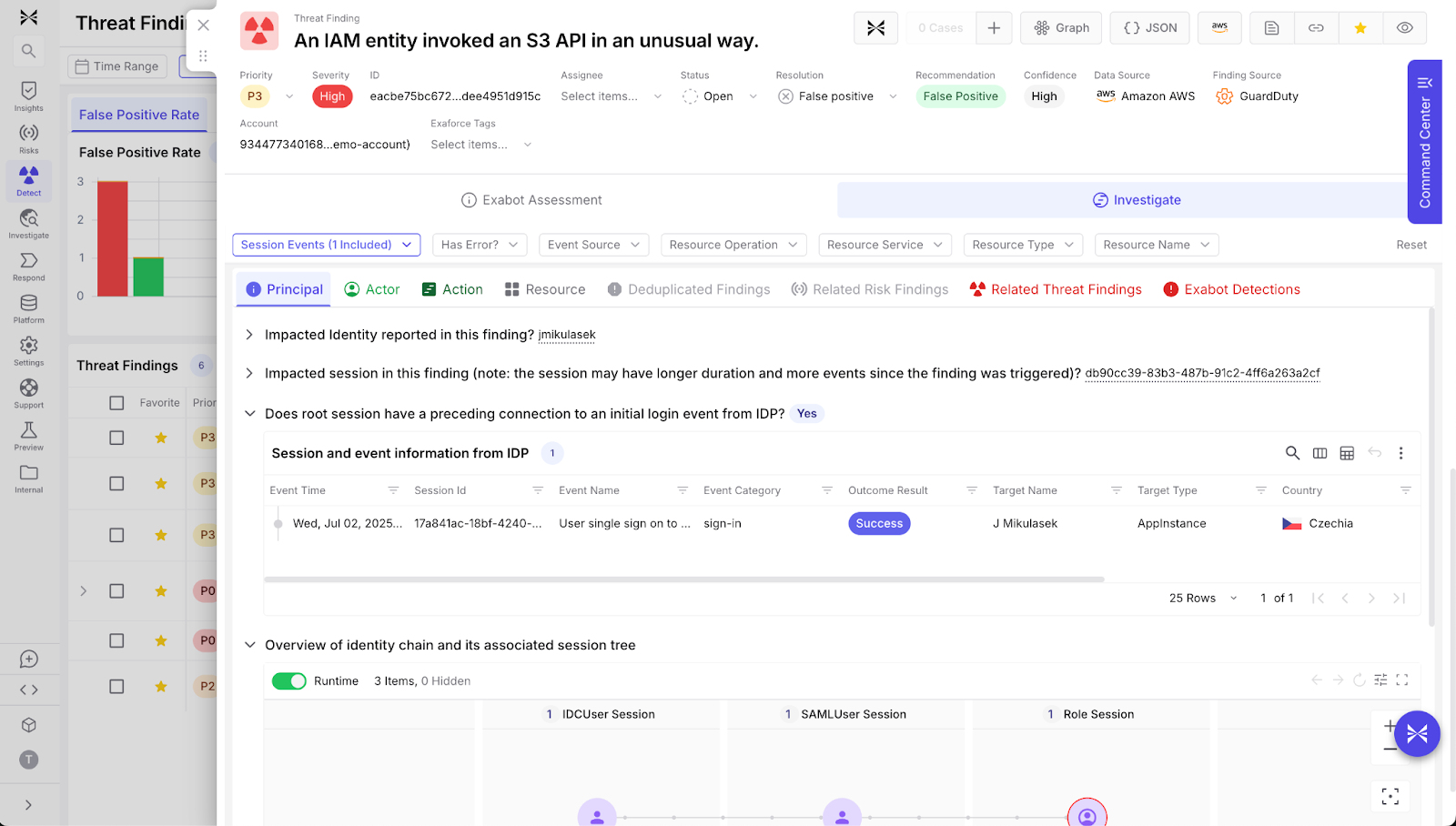
Enhanced alert contextualization and investigation
Exaforce automatically enriches alerts by correlating context across sessions and systems, answering critical investigation questions typically requiring expert analysts with knowledge of both security, cloud, DevOps, endpoints, and more. This allows it to deeply contextualize any alert across IaaS services like EKS, SaaS services like Google Drive, version control systems like GitHub, and more in only a way that an expert in the field could. All of this is summarized in highly digestible ways, while the data behind the summaries remains available when the alert is passed on to the investigation team. This significantly simplifies and accelerates the investigation of alerts that aren't automatically triaged.
Empowering teams of all sizes
Exaforce democratizes advanced SOC capabilities, empowering even understaffed or smaller teams to achieve high-level security operations. Automating complex triage processes eliminates much of the burden on Tier 1 analysts and unblocks the rest of the SOC process. Through this, Exaforce allows organizations with or without dedicated SOC teams to maintain robust, proactive security postures.
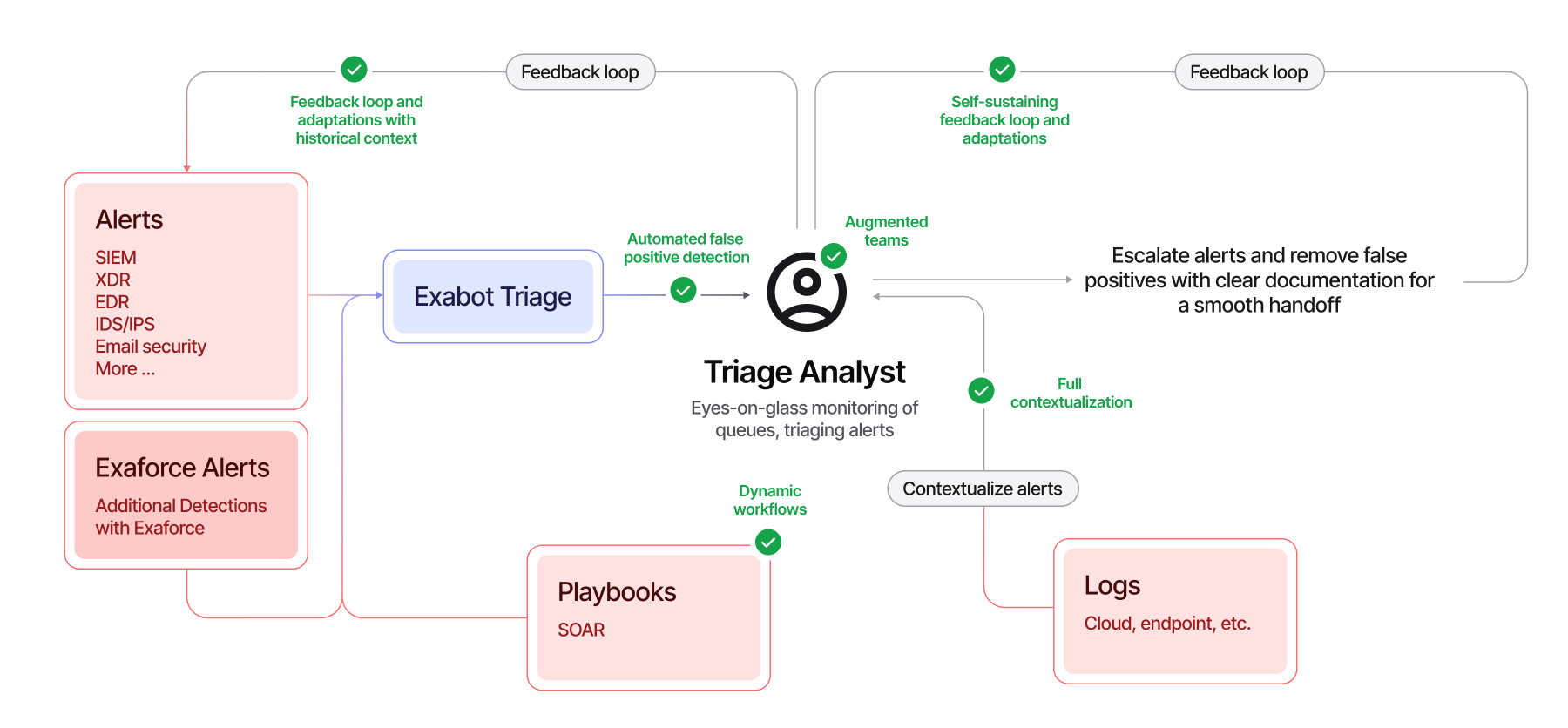
Triaging, without the turmoil
Triage shouldn’t be the most tedious part of a SOC analyst’s job, but today, it often is. High false positive rates, time-consuming investigations, fragmented tools, and broken feedback loops make it hard for Tier 1 through Tier 3 analysts to work efficiently or improve outcomes over time. And with handoffs between tiers introducing delays and inconsistencies, even the best triage efforts can break down before real response begins.
Exaforce changes that by embedding triage into an agentic SOC platform. It automates enrichment, prioritization, and contextualization while preserving shared insights across teams and tools. This alleviates the back pressure of high false positives by triaging them automatically, and automates enrichment across tools and platforms with the knowledge of the most skilled analyst, reducing the burden on understaffed teams and improving downstream and upstream processes. Instead of treating triage as an isolated step, Exaforce makes it the foundation of a continuous, AI-driven workflow, one where context flows naturally, feedback loops stay intact, and analysts are empowered to act faster and smarter. Because triage alone doesn’t make an AI SOC, but the right platform with the right transformational process can.






