At Exaforce, as we work with our initial set of design partners to reduce the human burden on SOC teams, we’re gaining valuable insights into current cloud usage patterns that reveal a larger and more dynamic threat surface. While many organizations invest in robust security tools like CSPM, SIEM, and SOAR, these solutions often miss the nuances of evolving behaviors and real-time threats.
Use Case: Single IAM User With Long Term Credentials Accessed From Multiple Locations
A device manufacturing company relies on a single IAM user with long term credentials for various tasks such as device testing, telemetry collection, and metrics gathering across multiple factories in different geographic regions. This consolidated identity is used from varied operating systems (e.g., Linux, Windows) and environments, which amplifies risk.
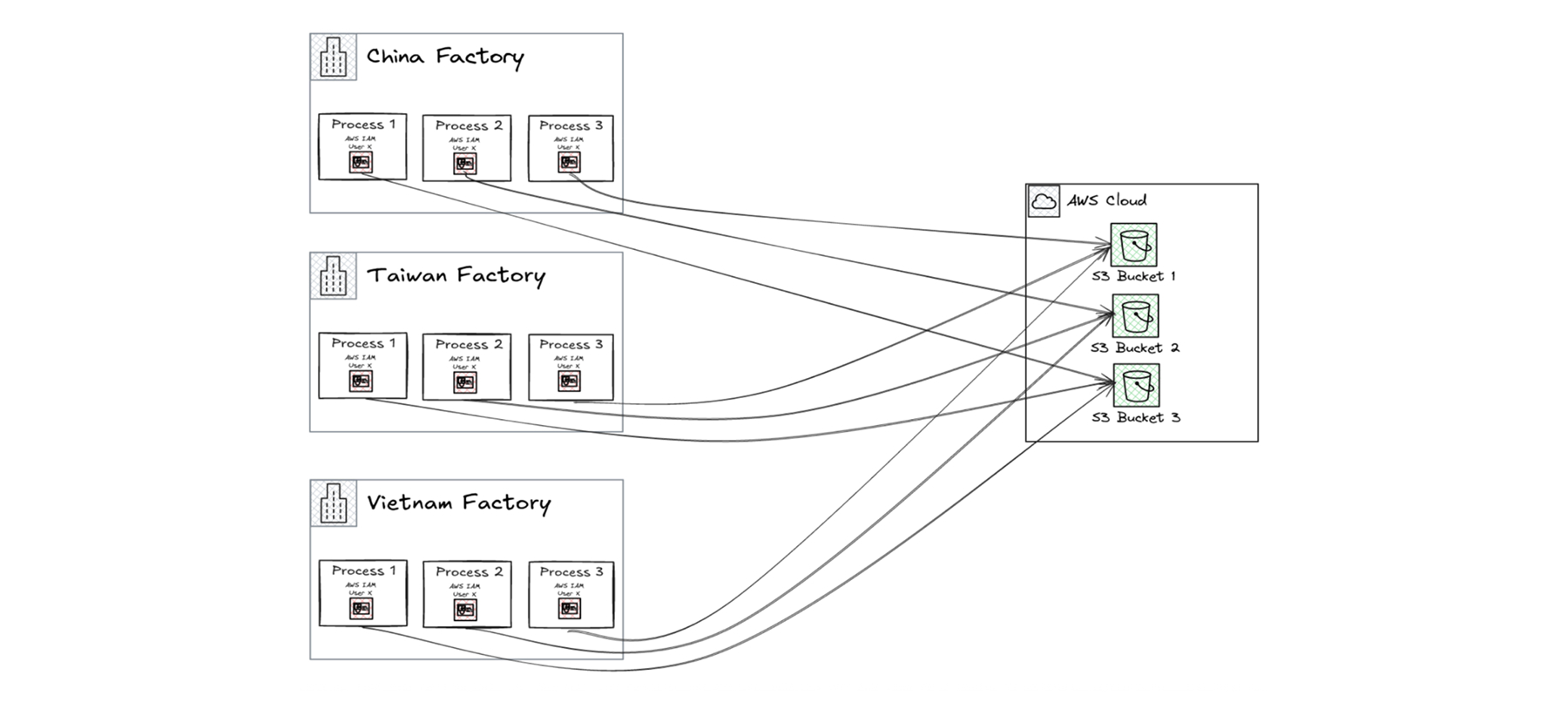
Threat Vectors and Monitoring Recommendations
To mitigate the risks associated with such a setup, focus on continuous threat monitoring with these priority measures:
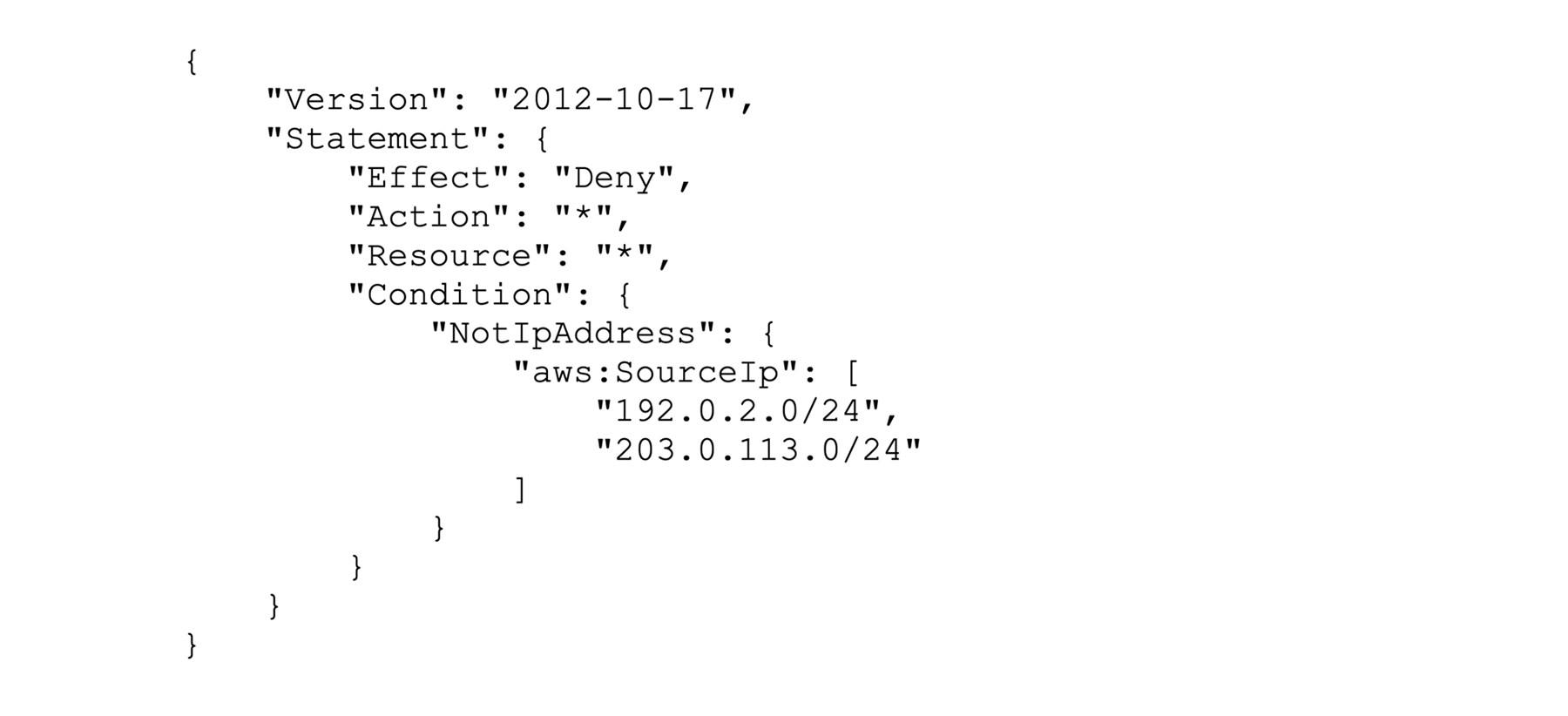
- IP Allow-Listing
- Define and enforce an allowed list of IP addresses for each factory.
- Alert on any access attempts from unauthorized IPs.
- Tool: AWS using policy conditions. Below is an example to deny everything but CIDR 192.0.2.0/24, 203.0.113.0/24
2. Resource Access Monitoring
- Continuously monitor and log which resources the IAM user accesses.
- Correlate access patterns with expected behavior for each factory or task.
- Tool: SIEM platforms integrated with cloudtrail logs.
3. Regular Credential Rotation
- Implement strict policies to rotate long term credentials periodically.
- Automate token rotation and integrate alerts for unusual rotation delays.
4. User Agent and Device Validation
- Identify and allow only a predefined list of acceptable user agents (e.g., specific OS versions like Linux and Windows Server) for each use case.
- Flag anomalies such as access from unexpected operating systems (e.g., macOS when not approved).
- Tool: SIEM platforms to co-related EDR and AWS cloudtrail logs and generate detections
Use Case: Long-Term IAM User Credentials in GitHub Pipelines
One of our SaaS provider partners is using long-term AWS IAM user credentials directly into their GitHub Actions CI/CD pipelines as static GitHub secrets, allowing automation scripts to deploy services into AWS. This practice poses significant security risks; credentials stored in CI/CD pipelines can easily become exposed through accidental leaks or external breaches—as seen recently with Sisense (April 2024) and TinaCMS (Dec 2024)—enabling attackers to gain unauthorized cloud access, escalate privileges, and exfiltrate sensitive data.

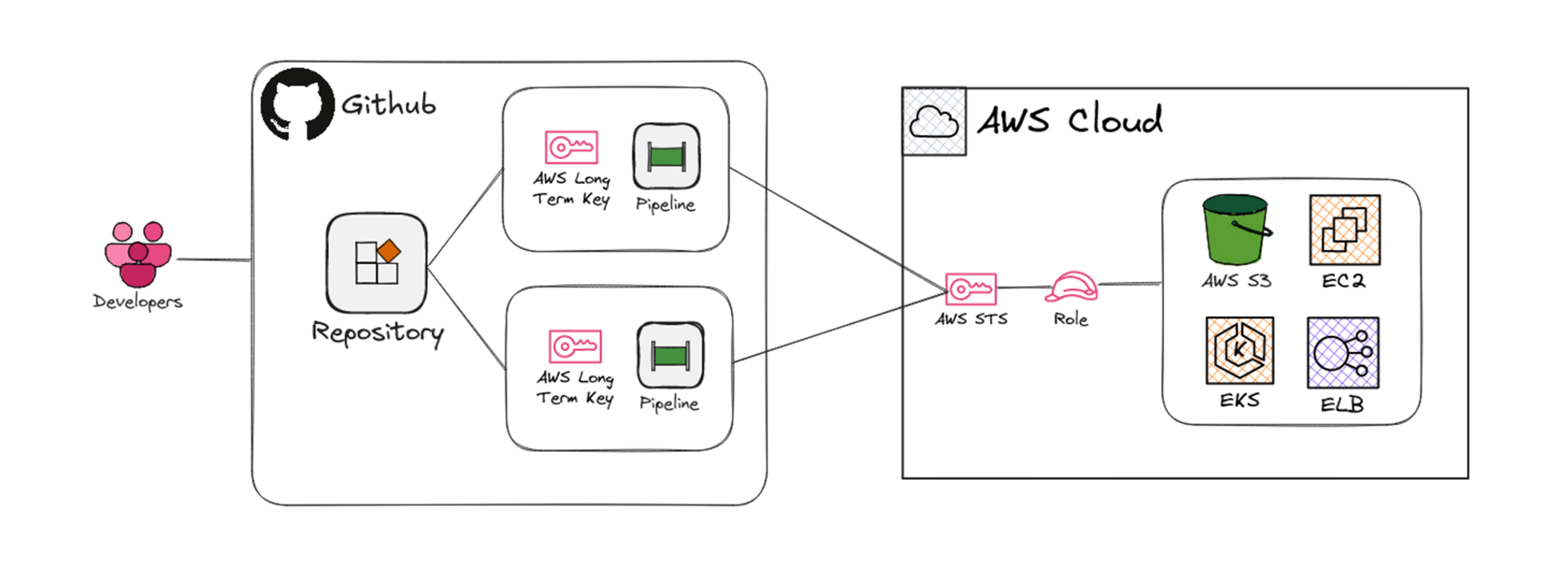
Threat Vectors and Monitoring Recommendations
To monitor and detect threats associated with this anti-pattern, consider these prioritized measures:
1. Credential Usage Monitoring
- Continuously monitor IAM user activity and set alerts for any anomalous actions, such as unusual access patterns, region shifts, or privilege escalation attempts.
- Tool: SIEM platform integrated with cloudtrail logs.
2. Regular Credential Rotation
- Implement strict policies to rotate long term credentials periodically.
- Automate token rotation and integrate alerts for unusual rotation delays.
Remediation: Short-lived Credentials via OIDC
Transition to GitHub Actions’ OpenID Connect (OIDC) integration, enabling temporary credentials instead of embedding long-term keys, minimizing risk exposure.
Ineffective Use of Permission Sets in Multi-Account Environments
A cloud-first SaaS provider is misusing AWS permission sets by provisioning direct access in the management accounts where sensitive permission sets and policies are defined instead of correctly provisioning them across member accounts. This setup complicates policy management and leaves the management account largely unmonitored, creating blind spots where identity threats can emerge before affecting production or staging.
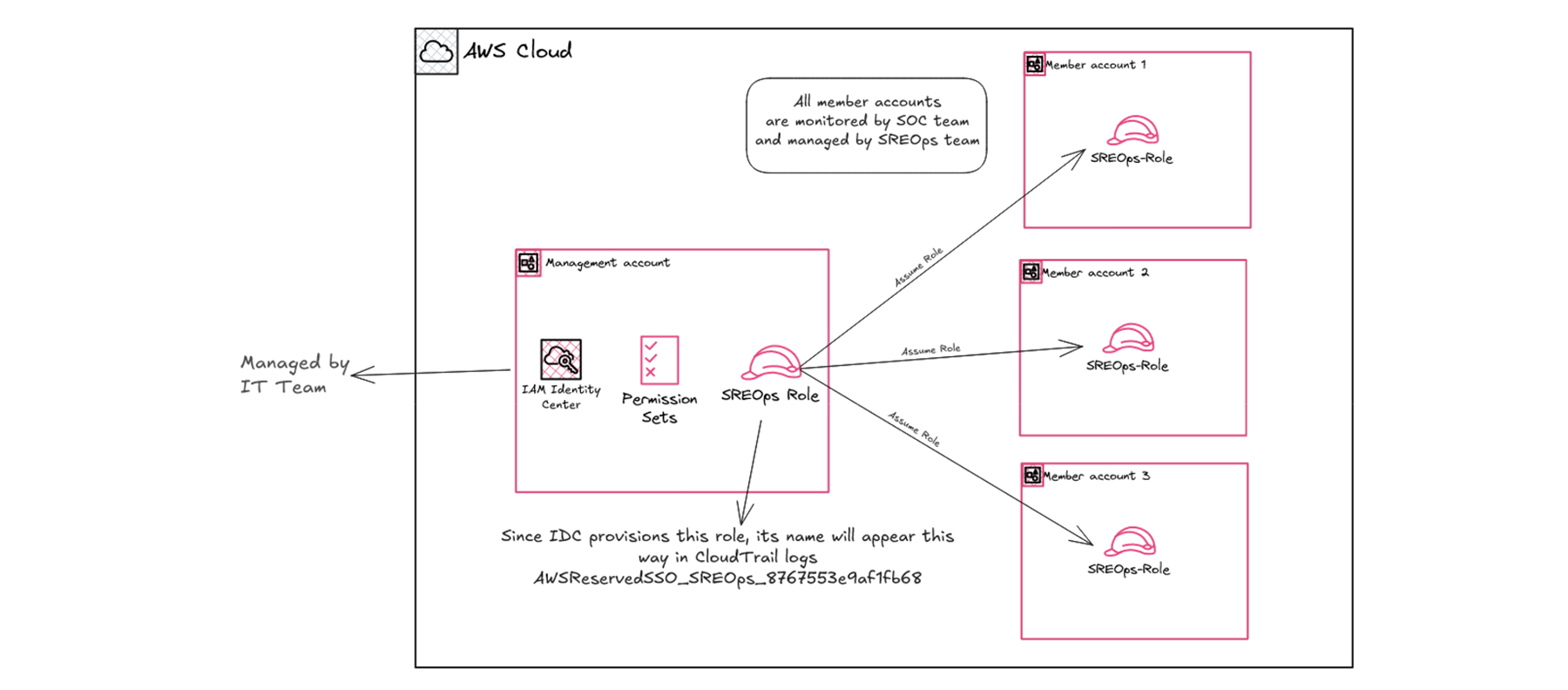
Threat Vectors and Monitoring Recommendations
1. Monitoring Management Account Activity
- Monitor all IAM and policy changes in the management account using AWS Tools: SIEM Tool integrated with CloudTrail logs. Detections should trigger alerts on any modifications to permission sets or cross-account role assumptions.
2. Misconfigured Trust Relationships:
- Audit and continuously validate trust policies for cross-account roles to ensure they only allow intended access.
- Tools: AWS Config rules to flag deviations from approved configurations.
3. Policy Drift and Unauthorized Changes:
- Implement automated periodic reviews of permission sets and associated IAM roles. This ensures that any drift or unauthorized changes are quickly detected and remediated.
- Tools: SIEM Tool integrated with CloudTrail logs.
Root User Access Delegated to a Third Party
Delegating root user access to a third party for managing AWS billing and administration may seem low-risk, but it leaves the company without direct oversight of its highest-privilege account. When the root credentials including long-term passwords and MFA tokens are controlled externally, the risk escalates dramatically: if the third party is compromised or mismanages their controls, attackers could gain unrestricted access to the entire AWS environment.
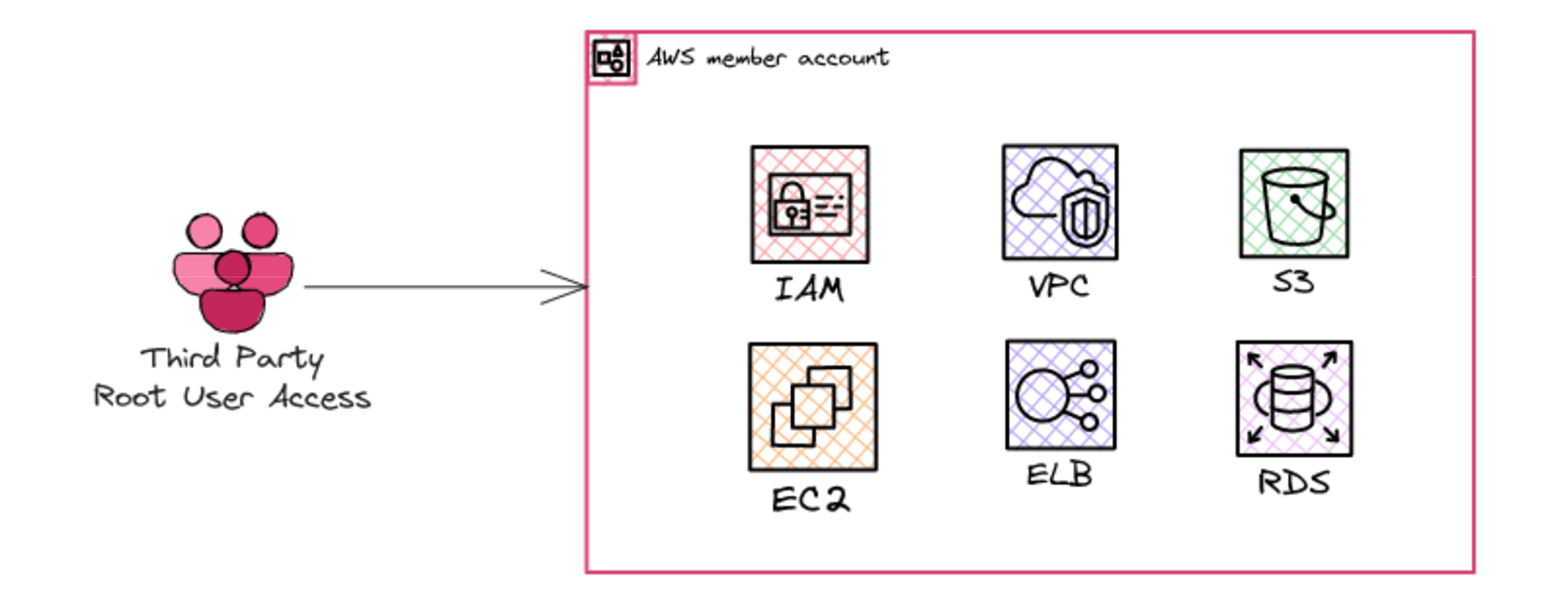
Threat Vectors and Monitoring Recommendations
- Monitoring Unauthorized Root Activity
- Monitor all root user actions via CloudTrail and SIEM alerts for any anomalous behavior.
- Tools: SIEM Tool integrated with CloudTrail logs.
- Third-Party Compromise
- Regularly audit third-party access and security posture
- Tool: Identity access management tool.
Remediation: Centralized root access
Remediate by removing root access and migrating to centrally manage root access using AssumeRoot, which issues short-term credentials for privileged tasks.
Contact us to learn how Exaforce leverages Exabots to address these challenges.