Why compliance matters
Let’s face it, most startups treat compliance like airplane wings; they build the whole plane, get ready for takeoff, then realize they need to bolt them on while already rolling down the runway.
We took a different path.
From day zero, compliance was part of the blueprint. While engineering built our Agentic SOC platform, the entire company worked hand in hand to ensure our security, governance, and operational practices were aligned with the most rigorous standards like SOC 2. Compliance was ingrained from the start, woven directly into how the platform was architected and how we operate every day.
Our earliest design partners came from the front lines of regulated industries, healthcare, finance, and life sciences. These weren’t just logo-chasing partnerships. They were formative relationships shaping our platform’s core features. And if we wanted them to stick around and trust us, we had to speak their language: compliance.
So we got to work. No shortcuts. No delayed timelines. Just a stubborn commitment to doing things right, from the start.
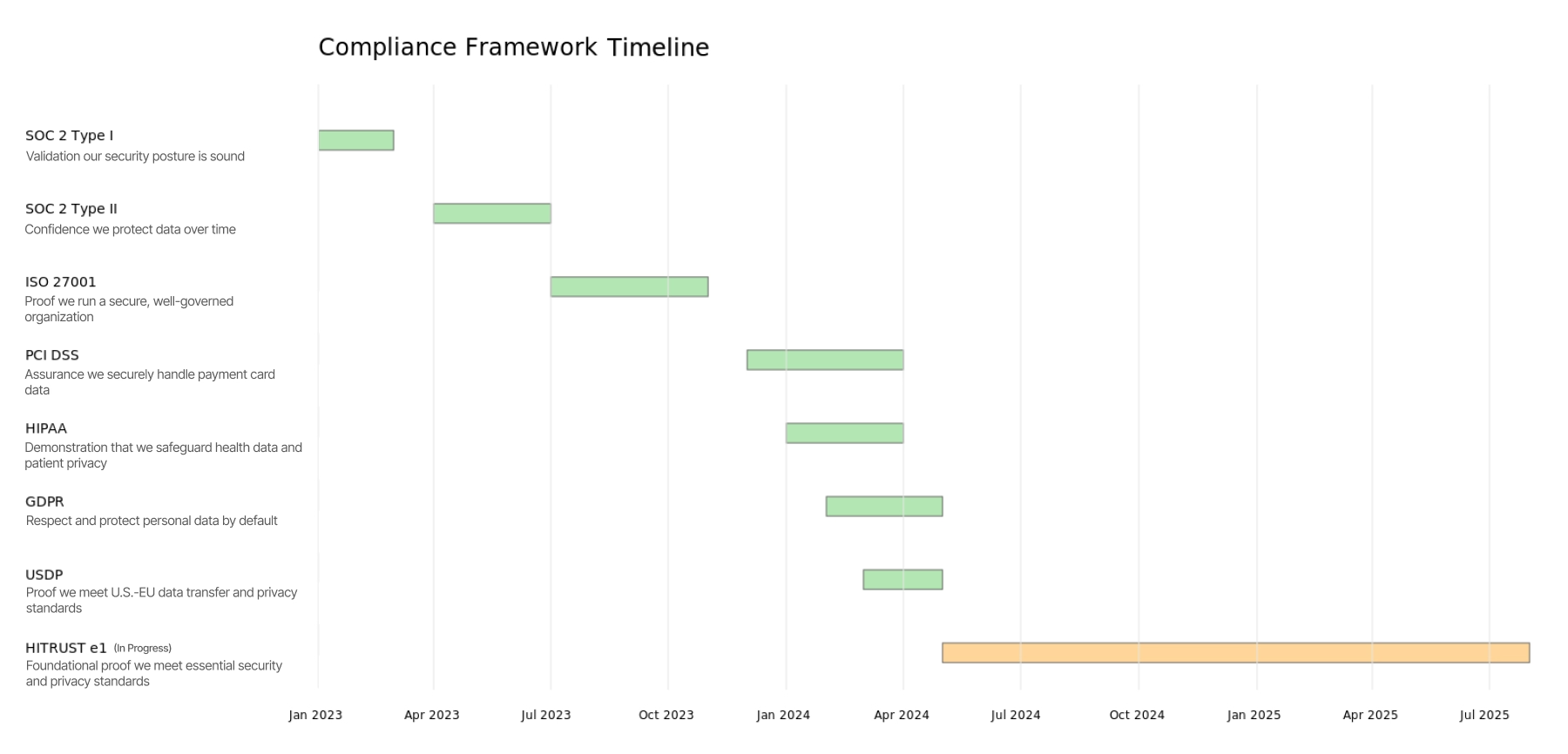
Fast forward: we’ve now locked in SOC 2 Type I & II, ISO 27001, PCI DSS, HIPAA, GDPR, and USDP. And we’re in mid-observation for HITRUST e1. And the best part? We hit many of these milestones ahead of schedule.
This is a startup survival guide told by the guy who wrote every policy, chased every screenshot, and occasionally bribed engineers with craft beer to hit compliance deadlines.
Our vision: Compliance by design
Before the first customer onboarded. Before the first alert fired. Before our platform even launched, we were already building with compliance in mind.
Why? Because we wanted to:
- Enable regulated industries to adopt Exaforce from day one.
- Create enterprise-grade trust in our platform and company.
- Bake security and governance into our architecture, not bolt it on later.
We aligned early with cloud-native frameworks like SOC 2 and ISO 27001, while preparing for partner-driven frameworks such as USDP, GDPR, HIPAA, and HITRUST.
The roadmap: From zero to certified
The leadership behind the mission
"Compliance isn't just a milestone. It's a mindset. It's how we operate."
— Team Exaforce
We don't treat compliance as a checkbox, nor is it the responsibility of a single person or department. It's a company-wide principle, woven into our culture of openness, agility, and transparency.
From day one, our leadership team committed to integrating security and compliance directly into our operational DNA. But the real strength of our program comes from our people: engineers, SREs, product leads, operations, and business teams who consistently go beyond expectations. Whether it is adjusting deployment pipelines, reworking onboarding flows, or documenting new processes, everyone leans in.
Collaboration as our foundation
Rather than compliance being enforced from the top down, it became a shared initiative. This unique culture meant that when compliance controls required change, the conversation wasn’t about resistance; it was about how to make it work faster, better, and cleaner. We strove to not only meet the bar but also to iterate on how it could be raised without adding unnecessary friction.
We partnered with well-known, trusted industry experts for audits, assessments, and risk validation. Their guidance helped us refine our approach, confirm we were meeting the highest standards, and challenge us to raise the bar even further. Combined with our internal expertise, this collaboration allowed us to build a program that’s both audit-ready and operationally seamless.
Platforms that powered the process
To scale and automate compliance in a fast-moving startup, we leaned into a robust and cloud-native toolset. We built our compliance foundation on proven, cloud-native platforms for policy management, automation, and access control, the same kinds of tools used by leading enterprises. These systems gave us a single source of truth for evidence, automated monitoring of controls, and streamlined onboarding and offboarding.
But the most important platform in the mix was our own. We used the Exaforce Agentic SOC Platform internally to detect, triage, and investigate anomalous activity, not just for security, but to meet and validate compliance controls in real time. We proved that the capabilities we deliver to customers can stand up to the same scrutiny we face ourselves.
“We drank our own champagne. Our platform wasn’t just built for others, we used it internally to prove it works.”
— Team Exaforce
Embedded into operations
By leveraging our stack and working as one team, compliance became an ongoing habit, rather than a quarterly panic. Tasks are tracked automatically. Alerts are triaged through Slack. Access reviews are visible and documented. When an audit request comes in, we already have the evidence.
This embedded model is what makes Exaforce different. We treat compliance as a competitive edge, a trust enabler, and an extension of our platform's mission to make cloud security more intelligent.
Lessons from the trenches
Real challenge: No access = No evidence
Because we operate under least privilege access, there were many times I didn’t have direct access to the systems I needed evidence from. Chasing SREs during crunch time? Let’s just say I had to get creative, offering bribes (beer) or joking about dire consequences!
Biggest win: No audit findings
When auditors returned clean reports (no findings, no changes, no redo), that was a moment of deep pride. Another highlight: beating internal certification deadlines despite product sprint pressure.
Cultural shift
Convincing a fast-moving startup team to complete onboarding, read policies, and watch training videos wasn’t easy. But today, compliance is just something our team does—and that mindset is a win.
Building a culture of compliance
At Exaforce, compliance is a mindset woven into every layer of how we operate. Our approach blends automation, culture, and accountability. Every new team member completes training videos and policy acknowledgments in their first week, automatically tracked in Vanta, and reinforced through onboarding flows in GitHub. Slack-integrated bots and emails deliver timely reminders for compliance tasks. gently guiding staff toward full alignment without interrupting productivity. Our engineering culture prioritizes secure coding practices, internal peer reviews, and approvals of policies and architecture. Finally, exits are managed with the same precision as entries, ensuring no loose ends across systems or access.
These are deep operational habits. And when auditors come knocking, the difference between our compliance culture and surface level changes is clear.
Drinking our own champagne: Agentic AI at work
We use our own Agentic SOC Platform internally for detection, triage, and alerts. This has the double benefit of learning from our own use and providing real operational value.
Example 1: Dormant account reactivation
Our system caught a dormant user in a design partner’s account suddenly becoming active. Turns out it was a contractor account that should’ve been disabled. We escalated and helped them shut it down before anything major happened. If we internally enforce processes in compliance, our platform flags similar situations for us.
Example 2: Brute-force login attempts
For another partner, we flagged suspicious activity across multiple accounts. The first time, they disabled the account. The second time, they revamped their MFA policies. Detections like these allow several compliance controls to be fulfilled.
That’s the power of an agentic AI SOC platform built to cover detections, triaging, investigations, and response.
Value delivered before launch
Compliance was always a launchpad for us. Before we even shipped our product, our security posture was already opening doors. Here's what it meant in practice:
Frictionless security reviews
We cleared complex vendor assessments early, turning red flags into green lights for our design partners and prospects.
Accelerated procurement cycles
Buyers saw a mature, secure partner, not a startup with "coming soon" promises.
Stronger first impressions
Our Security Trust Center impressed stakeholders and showed how seriously we take the protection of their data.
Built-in buyer confidence
Compliance gave us credibility, even in regulated industries, from day one.
By integrating security and compliance into our go-to-market motion, we didn’t just meet expectations — we exceeded them before launch.
Looking ahead
Our commitment to trust and transparency continues to evolve beyond our initial certifications.Next on our roadmap are advanced frameworks like ISO 27017, ISO 27018, and the ambitious FedRAMP program. We’re investing in smarter, more scalable ways to maintain compliance, reducing manual overhead while increasing reliability. A unified, public-facing hub where customers and partners can access our policies, certifications, and security posture at any time.
Final thoughts
If you’re a CISO, compliance lead, or security-conscious buyer, we built this for you. Exaforce is a compliant, intelligent, and trust-first cloud security partner.
We took the hard road first so our customers could go fast later.
Let’s secure the future together.






