2025 turned “normal” security operations into hard mode. Cloud sprawl continued, non-human identities multiplied, attacks grew faster, and third-party dependencies became inseparable from daily risk. For SOC teams, the job had to not only investigate more, but they also had to understand more.
Verizon’s 2025 DBIR noted that ransomware was present in 44% of breaches and increased 37% compared to the prior year; it also calls out that third-party involvement doubled from 15% to 30%.
Against that backdrop, 2025 was a foundational year for Exaforce. We announced $75M in Series A funding to accelerate the Agentic SOC Platform and its multi-model approach, blending LLMs with semantic and behavioral models. We also launched the full-lifecycle AI SOC platform and introduced Exaforce MDR, bringing agentic automation plus expert analysts across detection, triage, investigation, and response. We also over doubled the team from 50 to 110 employees (and we’re hiring).
2025 was a foundational year for us, and we wanted to reflect on aggregated customer statistics and key milestones before moving into the themes that mattered most for defenders.

By the numbers across Exaforce customer environments
Across customers (including our own champagne environment), Exaforce processed 79 billion events and over 1.29M alerts. Every event processed is an opportunity to learn and improve our platform for our customers.
Noise reduction was the dominant story, measured by the reduction in alerts that require human intervention.
- 97% of alerts required no analyst investigation: only 3% of alerts (41K out of 1.29M) required manual investigation; the remainder were auto-dispositioned.
- 98% of alerts were benign or false positives after human review, highlighting the noise in the industry.
- Exabots achieved a 98% accuracy rate, defined as the ratio of AI recommendations that matched outcomes confirmed through human review across all validated alerts.
In this time period, we saw a marked increase in the level of trust in the recommendations and investigations of Exabots as the above human level of accuracy was verified, drastically improving MTTI for those customers.
What the platform labeled as the most common threat types
The top three threat types in the dataset were:
- Initial Access
- Credential Access
- Execution
This aligns with what most SOCs feel operationally, that investigations typically start with identity misuse, initial access signals, and scattered activity that needs correlation.
Where false positives showed up by source
False positive rates vary heavily by source and environment. In the dataset (excluding low-count finding sources), the highest false positive rates were listed for:
- CWPPs
- SIEMs
- Native cloud detection tools
The lowest false positive rates (again excluding low-count sources) were:
- Email security
- EDR
- Identity tools
Overall, the rankings suggest that sources designed to cast a wide net, such as CWPPs, SIEMs, and native cloud detection tools, tend to produce more false positives, likely due to their broader telemetry and more generalized detection logic. By contrast, email, EDR, and identity tools skew lower in false positives (FP), reflecting more contextual or control-point-specific signals. Email in particular benefits from including reported alerts (e.g., user-reported phishing), which can meaningfully reduce false positive rates, though it still does not eliminate them.
Cloud telemetry dominance was not subtle
In tenants with AWS, AWS dominated telemetry, accounting for 67% of events on average and over 90% in many environments. That matters because most traditional SIEM and log aggregation architectures were built around the assumption that you can index and retain the majority of what you ingest. AWS breaks that model. Cloud logs are high volume, high cardinality, and tied to short-lived resources, so “ingest everything” quickly becomes “pay a lot to store noise.” Even when you can afford it, the analytic payoff often lags because the platform is busy moving and indexing data instead of producing investigation-ready context.
Identity sprawl is real, and non-human identities are the multiplier
Across the dataset, we observed 14.5 non-human identities for every human identity. That’s meaningfully lower than the 50:1 ratio reported in at least some industry discussions, but still large enough to materially affect correlation and triage workflows.
At 14.5:1, non-human identities change the shape of investigations. If your alert context ends at “user X,” you will miss the majority of identity-driven paths that actually execute in cloud environments.
The SOC workflow started to be re-architected in 2025
A useful way to describe 2025 is that teams stopped treating detection engineering, alert triage, investigation, threat hunting, and response as separate tiers. More teams started treating them as a single system that needs to work end to end, because the handoffs between stages have become the bottleneck.
Legacy, workflow-driven tools struggle to keep up with cloud-scale telemetry and identity sprawl, so “process” cannot compensate for missing context or slow correlation. Exaforce’s approach this year was to make that system-level shift explicit by applying agentic automation across the entire SOC lifecycle, not only Tier 1 triage.
If you want the conceptual framing behind this change, we published three posts that outline how the problem shows up in daily operations across detections, triage, and investigations. The throughline is consistent. If detections do not carry business and identity context forward into investigation, and if investigation does not hand off cleanly into response, speed improvements stall out even when tooling looks modern on paper.
What “full-lifecycle” looks like in practice
Customer outcomes are easiest to summarize in the language SOC teams use when something genuinely changes their day to day. One customer message captured the shift to working with an agentic SOC platform bluntly, in a positive way. Another customer told us, “I use Exaforce like ... 100x a day” and “You’re the number 1 tool in my arsenal.” Full-lifecycle only matters when it shows up in the work itself, meaning fewer investigations that go nowhere and faster, more confident answers when something is real.
You can see that in the customer stories. LottieFiles reported saving 6 days and 4 hours of person-hours every 30 days and an 80% reduction in investigation time while building a full-lifecycle SOC that spans code and cloud. Fuze reported 75% of AWS GuardDuty alerts automatically triaged as false positives and a 94% reduction in MTTI as they built a secure stablecoin platform with Exaforce MDR. Those are the measurable outcomes, but the part that stays with our team is what sits behind them, the moments where a real attack gets surfaced and blocked before it turns into a much worse week for our customers. That work is why we build, and why we keep pushing to make defenses more reliable for the teams that depend on them.
Extended research for better defense
This year, we published research and incident analysis across supply chain and cloud identity attack paths, including:
- tj-actions analysis
- s1ngularity supply chain attack
- npm wallet hijack patterns
- Google App Script abuse (“Ghost in the Script”)
- AWS CloudControl API as an attack tool
- historical enumeration (“log rings”)
These topics represent recurring patterns SOC teams now have to treat as normal work, including investigating third-party behavior, validating whether identity actions are expected, and quickly determining blast radius across cloud and code assets.
This also connects back to industry-level trends. Verizon’s DBIR explicitly calls out the increase in third-party involvement in breaches from 15% to 30%. It’s been clearer than ever that you cannot confine investigation to assets you own. The SOC has to reason about integrations, automation, and dependencies as first-class entities.
Third-party recognition and trust
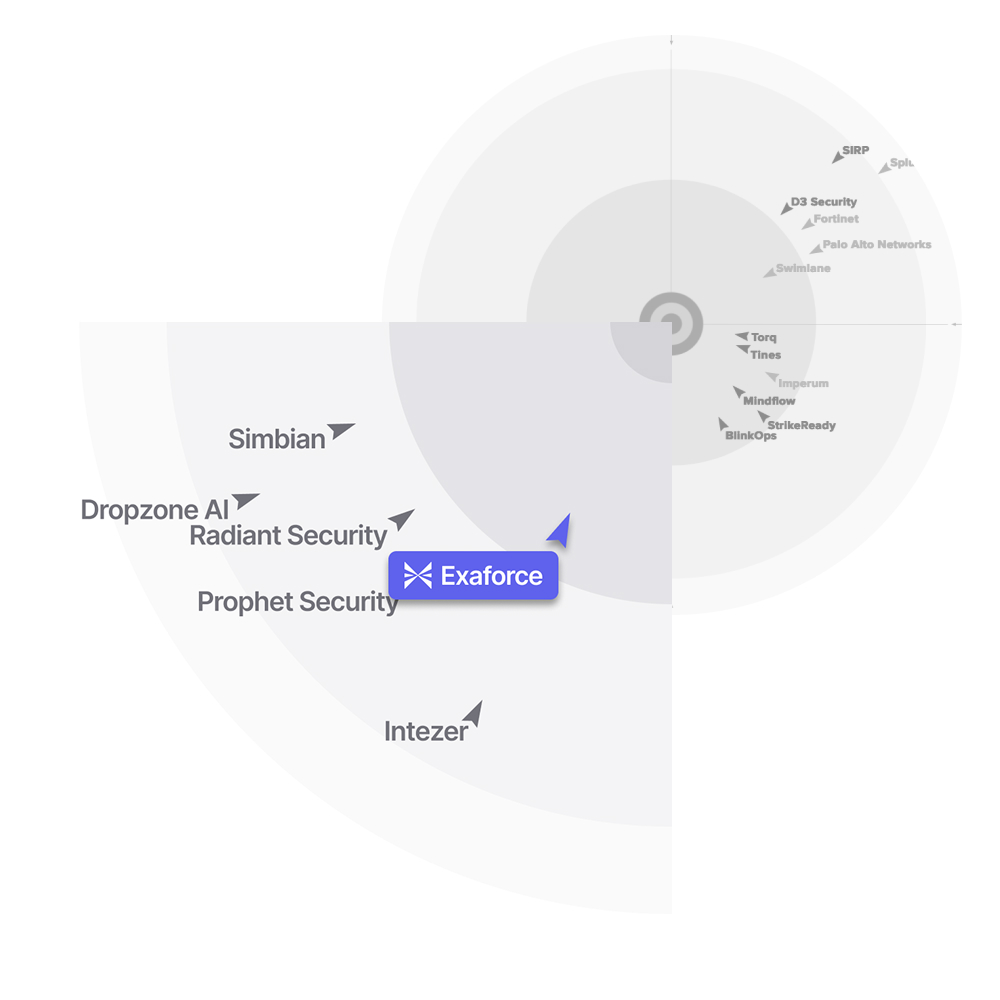
2025 also included external validation of Exaforce’s approach. In the 2025 GigaOm Radar for SecOps Automation, Exaforce was recognized as a Leader and Outperformer, with GigaOm comparing 19 vendors and highlighting strengths such as threat correlations, multi-model detection, and a “pre-LLM data layer” that normalizes and enriches data before analysis.
Beyond that report, we were also recognized across several industry lists and programs that reflect both product momentum and market relevance.
- AWS Generative AI Accelerator
- Leader in the Latio AI Security Market Report
- The Top 50 Software Companies of 2025
- 2025 Intellyx Digital Innovator Award
- 4 Startups to Watch in AI-Driven Cybersecurity
- 10 Software Companies to Watch in 2026
- 8 Gartner mentions
We also strengthened our compliance posture and publicly documented key milestones, including HITRUST certification. Alongside HITRUST, our compliance program includes SOC 2 Type 2, ISO 27001 certification, GDPR alignment, PCI DSS, and HIPAA support.
What we are building toward
2025 reinforced a hard truth for security operations. The constraints that define the job are not going away. Cloud telemetry continues to grow, identity continues to sprawl, and third-party dependencies keep expanding the scope of what a SOC has to understand. In that environment, the winning strategy is not to ask analysts to move faster through the same volume of noise. It is to change the default outcome of the work so that the majority of alerts are resolved with defensible automation, and the minority that remain come with investigation-ready context.
As we head into 2026, our focus stays the same. We will keep investing in full-lifecycle capabilities that reduce wasted investigation time, speed up high-confidence decisions, and connect detections to response with fewer brittle handoffs. We are grateful for the customers who push us with real-world feedback and real constraints, and we are committed to building technology and services that help SOC teams stay ahead without having to scale headcount at the same rate as telemetry.






