We’re proud to share that Exaforce has officially achieved HITRUST e1 certification, a significant milestone in our continuous commitment to protecting customer data and maintaining the highest standards of security, privacy, and operational excellence.
This certification reinforces our promise to deliver AI-driven SOC automation with integrity and transparency, while empowering enterprises to operate securely in the cloud.
Why HITRUST matters
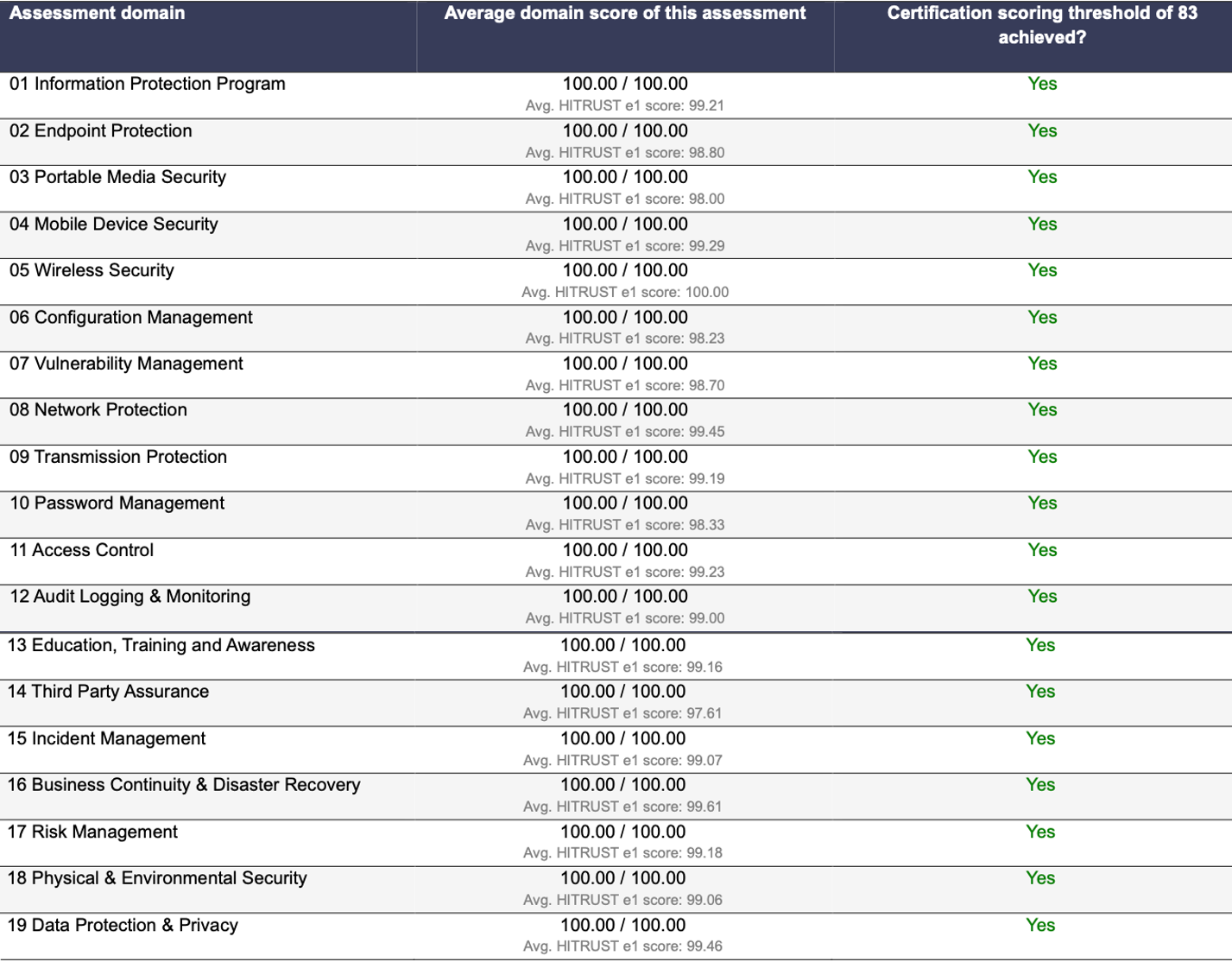
The HITRUST e1 assessment provides independent verification that we meet and maintain industry-recognized security and privacy requirements across 19 domains.
It demonstrates that the controls within our Agentic SOC Platform are designed and operated to protect sensitive information across diverse regulatory frameworks, including HIPAA, ISO 27001, SOC 2 Type II, PCI DSS, GDPR, and USDP.
Achieving HITRUST certification validates the maturity of our internal security program and our commitment to continuous assurance. We operate in some of the most security-conscious industries, and this certification reflects the depth of our governance, risk, and compliance culture.
How we embed compliance and security every day
Our cloud-native architecture ensures every customer runs on dedicated, isolated infrastructure, eliminating concerns about data-level multi-tenancy and strengthening tenant trust.
We continuously monitor, test, and improve our own security posture by feeding all the data sources we use to our Agentic SOC Platform and put our Exabots to work.
Powering the Agentic SOC platform
Our Agentic SOC Platform leverages AI-driven Exabots to automate detection, triage, investigation, and response.
We use the same platform internally to manage alerts, enrich events, and track SLAs, drinking our own champagne as we evolve our SOC automation capabilities.
Integrations that Reinforce Our HITRUST Controls
Achieving and maintaining HITRUST certification is a continuous process of verifying that every control is implemented, monitored, and evidenced effectively. Our deep integration ecosystem plays a critical role in that journey.
Each integration helps us and our customers automate evidence collection, strengthen control enforcement, and maintain continuous compliance across hybrid environments, directly supporting key HITRUST e1 control domains, including Access Control, Endpoint Protection, Incident Management, Logging & Monitoring, and Risk Management.
Our platform’s integrations ensure that every layer of the security stack contributes to ongoing HITRUST assurance.
Examples include:
- Cloud & IaaS: With AWS (GuardDuty, CloudTrail), Azure, and Google Cloud SCC, Exaforce provides auditable event logs, threat detections, and configuration baselines mapped to HITRUST requirements.
- Identity: With Okta and Microsoft Entra ID, we enforce MFA, SSO, and least-privilege access aligned with HITRUST Identity & Access Control objectives.
- EDR: CrowdStrike Falcon, Microsoft Defender, and SentinelOne strengthen endpoint protection, device compliance, and vulnerability control domains.
- SIEM / SOAR: Splunk, Microsoft Sentinel, and Sumo Logic enable centralized log aggregation and correlation for continuous HITRUST monitoring.
- Collaboration & Incident: Slack, Microsoft Teams, PagerDuty, and incident.io support timely incident response and escalation workflows, meeting HITRUST communication and response criteria.
- Ticketing & Workflows: Jira and ServiceNow automate remediation tracking and control documentation for audit readiness.
Explore all current and upcoming integrations: exaforce.com/integrations
By connecting every part of the operational and security stack, our integrations transform compliance from a static audit exercise into a living, automated assurance model, ensuring that our HITRUST-certified controls remain active, monitored, and verifiable in real time.
Continuous compliance, continuous trust
Security at Exaforce is our operating principle. We continuously align with frameworks such as:
- SOC 2 Type II
- ISO 27001
- HIPAA
- PCI DSS
- GDPR / USDP
- HITRUST e1
Each certification strengthens our customers’ ability to demonstrate compliance in their own audits and regulatory assessments. Read more about the roadmap that guided our path to validating and strengthening customer trust, and visit trust.exaforce.com to learn more about our certifications.
The road ahead
Achieving HITRUST e1 is another step forward in our commitment to providing the highest level of security for our customers and our platform. We’ll continue expanding our automation capabilities, deepening integrations, and evolving our compliance posture as we pursue higher-level certifications.
Our mission remains clear: make security operations faster, smarter, and more reliable through AI and automation.






