On November 3, 2025, Exaforce detected a coordinated attempt to compromise a customer’s Google Workspace account. The sequence began with a failed login from a Budapest commercial proxy at 12:06 UTC and escalated hours later when a successful login originated from a Linode server in Chicago, while the user was simultaneously active from their normal Ashburn location.
Within minutes of that Chicago login, the attacker established persistence through standard account takeover actions. In scenarios like this, legacy rule-based tooling would struggle to stitch these signals together. Building a static rule capable of correlating proxy-based infrastructure, anomalous ASNs, impossible travel, reauth events, and rapid-fire sensitive changes would require highly complex logic and constant manual tuning. Exaforce eliminated that burden, automatically correlating signals that would otherwise take analysts hours to piece together.
We will outline the attack and how Exaforce’s agentic SOC platform identified, correlated, and ultimately helped disrupt this targeted attack.
Executive Summary
Attack Window: November 3, 2025 (12:06 - 18:11 UTC)
Initial Vector: Failed login from a commercial proxy exit node
Infrastructure: Multiple commercial proxy services (IPRoyal, MarsProxies, NodeMaven, ProxySeller, Webshare) and a Linode cloud server
Exaforce Detections: Impossible travel, anomalous ASN, unfamiliar IP infrastructure, Sensitive Action Performed
Outcome: Attacker successfully authenticated twice, changed recovery email, and reset the account password
User Baseline: Normal activity originates from Ashburn and Amsterdam, none matching Chicago or Budapest, where the attacks originated
Remediation: Temporary account deactivation while the customer completes their investigation.
The anatomy of the attack
1. Initial reconnaissance & failed access attempt
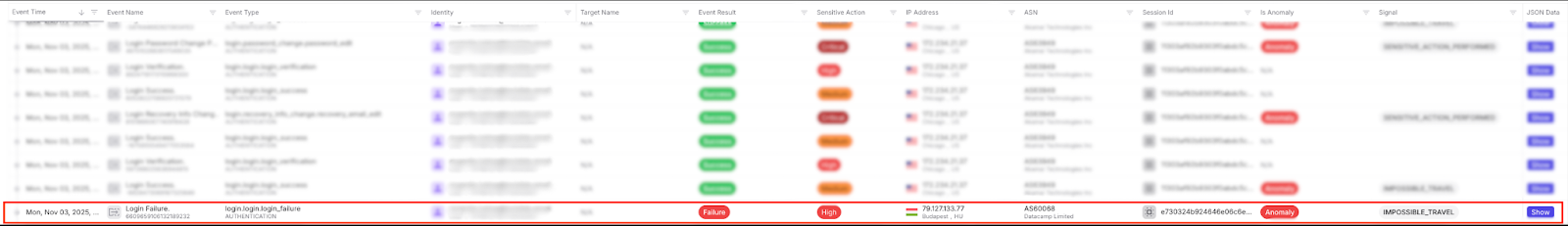
12:06 UTC - Budapest (Commercial proxy)
The first sign of malicious activity came from a failed login attempt originating from a commercial proxy exit node in Budapest. The infrastructure used is associated with multiple proxy services, indicating the attacker was masking their true location. No access was gained at this stage.
2. Attacker regroups and acquires valid credentials
12:06-17:39 UTC - 5.5 hours of silence
Following the failed login, the attacker paused activity. This window is consistent with credential-harvesting techniques, likely involving a phishing lure designed to capture the victim’s Google Workspace password.
3. Unauthorized access achieved
17:39 UTC - Chicago (Linode cloud server)
The attacker successfully authenticated using a Linode cloud server in Chicago while the legitimate user was active in Ashburn. This created a clear impossible-travel scenario and marked the moment initial access was achieved. Exaforce’s automated correlation elevated this immediately; in contrast, legacy tools would have required manual rule chaining or analyst investigation to connect the disparate geography, ASN, and infrastructure anomalies.
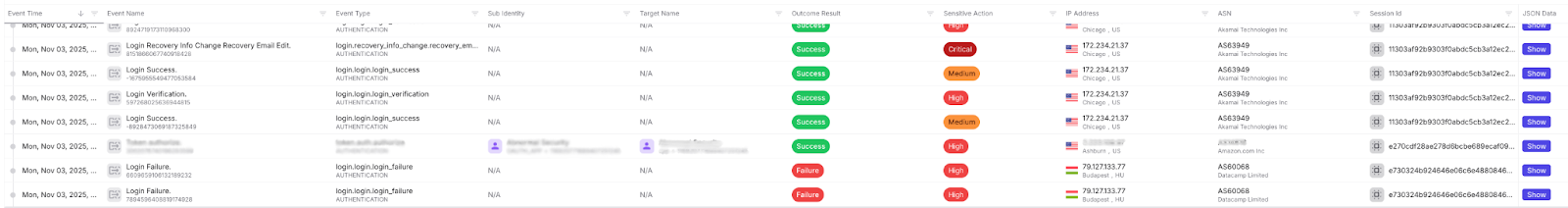
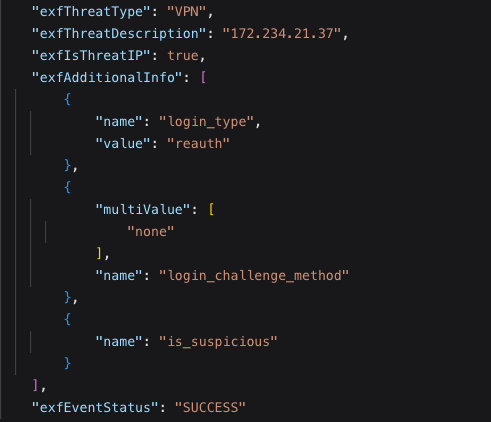
This successful authentication raised the highest severity signal, recorded as a “reauth” login from a VPN exit node, suggesting the attacker possessed valid session credentials and had fully taken over the account.
4. Establishing persistence
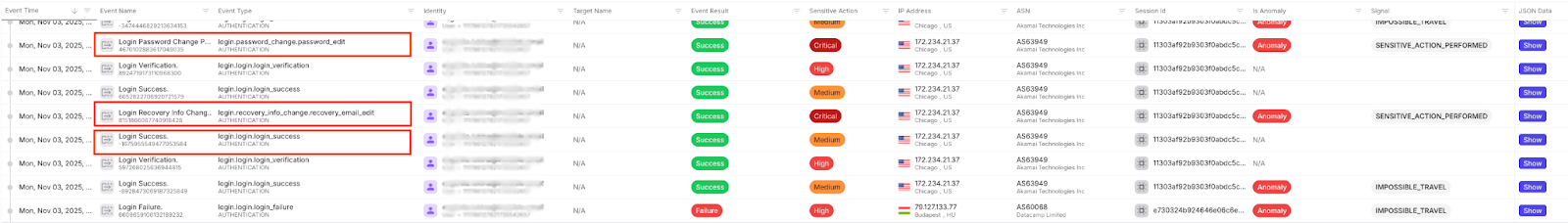
17:43 UTC - Recovery email changed
The attacker immediately modified the account’s recovery email, redirecting account-reset flows to an inbox they controlled.
17:45 UTC - Password changed
Two minutes later, the account password was reset. At this point, the attacker had fully locked the legitimate user out of their Google Workspace account.
Time to full takeover: 6 minutes
6. Continued access using rotating proxy infrastructure
18:11 UTC - Budapest (second proxy)
Roughly 30 minutes after the takeover, the attacker authenticated again, this time from a different Budapest proxy service. This confirmed that the newly set password was in use and demonstrated deliberate rotation of anonymized infrastructure, another scenario that typically evades single-event rules in legacy tools.
7. Duration of exposure & potential impact
From 17:39-18:11 UTC, the attacker operated with access across the user’s Gmail, Drive, contacts, calendar, SaaS integrations, and OAuth-connected services. The depth of data exposure or manipulation during this period is currently being investigated.
8. Current status & response
The account has been contained, and several response steps are now underway. The account was temporarily suspended to prevent any further activity. Out-of-band verification with the user is being conducted to confirm legitimate ownership. Administrators are reviewing email-forwarding rules, OAuth tokens, and Drive activity to identify any persistence mechanisms or data access. A supervised password and MFA reset is being performed to restore secure authentication. Finally, all actions performed during the unauthorized session are under investigation to determine the full scope of impact.
Response & remediation
Investigation and customer notification
Upon detection of the critical account modifications, Exaforce's MDR analyst immediately began investigating the correlated signals. The platform’s automated detection and enrichment capabilities produced a comprehensive evidence package within minutes, accelerating human analysis and allowing swift, targeted actions that limited the overall impact.
Lessons learned
This real-world account takeover demonstrates the critical importance of automated, context-aware security operations. The sophistication of modern attacks, combining proxy evasion, 2SV bypass, and rapid execution, demands equally sophisticated defense mechanisms.
Exaforce's automated detection identified the threat within minutes, correlated seemingly disparate signals into a coherent attack narrative, and executed containment before the attacker could establish persistent access or exfiltrate data, work that legacy tools would struggle to detect without extensive custom rule engineering. In an era where identity is the new perimeter, Exaforce provides the automated vigilance necessary to protect against even the most advanced account compromise attempts.





