In the cat-and-mouse game of identity protection, attackers are playing the long game, probing, rotating infrastructure, and waiting for a weak link. At Exaforce, we protect many high-profile companies in sensitive industries that are constant targets of identity attacks. This blog post walks through a real compromise that unfolded recently with a current customer across several weeks, involving dozens of international IP addresses, eventual credential theft, and multiple successful authentications.
We’re sharing this timeline to show how persistent attackers really operate, and how visibility, context, and behavioral signal correlation are essential in detecting and stopping identity-based attacks.
Executive Summary
Attack Duration: May 15 - June 25, 2025
Initial Vector: Brute-force login attempts to SaaS authentication portals
Infrastructure: 200+ IPs across 40+ countries, many with ASN anomalies
Exaforce Detections: Impossible travel, ASN mismatch, repeated policy evaluations
Outcome: Attacker obtained valid credentials and successfully authenticated multiple times before remediation
Remediation: Forced logout of all active sessions, password reset, account enrolled in MFA
The anatomy of the attack
Phase 1: Reconnaissance and testing (May 15 - June 5)
The first signals were subtle: a handful of failed authentication attempts from Switzerland, France, the USA, and Morocco. Over the next three weeks, the volume increased steadily. All were unsuccessful, but the geography, ASN mismatches, and repeated attempts on a few accounts hinted at a coordinated brute-force effort, most notably repeated failures from IPs tied to Beltelecom (BY), Bahnhof AB (SE), and Novotelecom (RU).
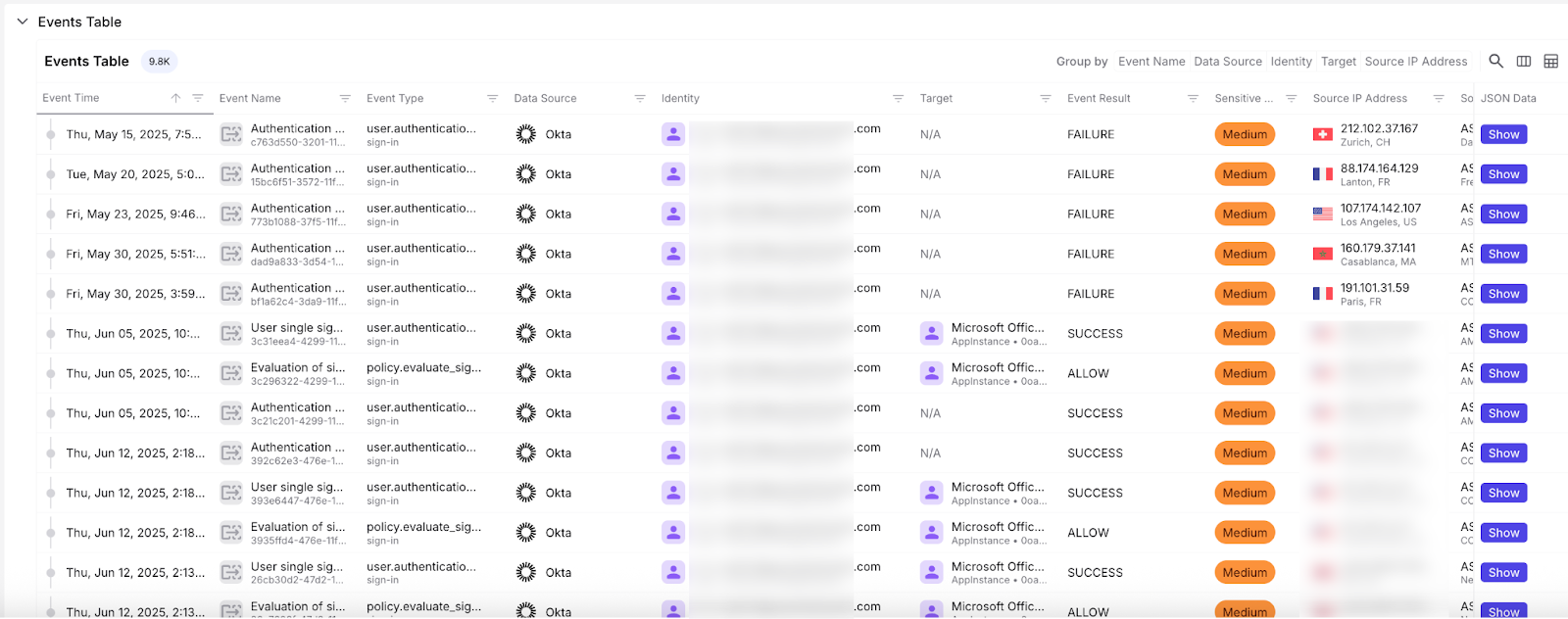
Despite the failures, the persistent attempts clearly showed this was a targeted attack that wouldn’t stop.
Phase 2: Coordinated spread (June 25)
The volume of activity spiked. Over 80 sign-on events were logged from a rotating set of international IPs. Key red flags:
- Multiple successful logins from IPs with no prior history in the environment
- Sign-ons from ASNs not aligned with user locations (e.g., AS29069 - Rostelecom)
- Location anomalies and ASN anomalies flagged across accounts, including admin identities
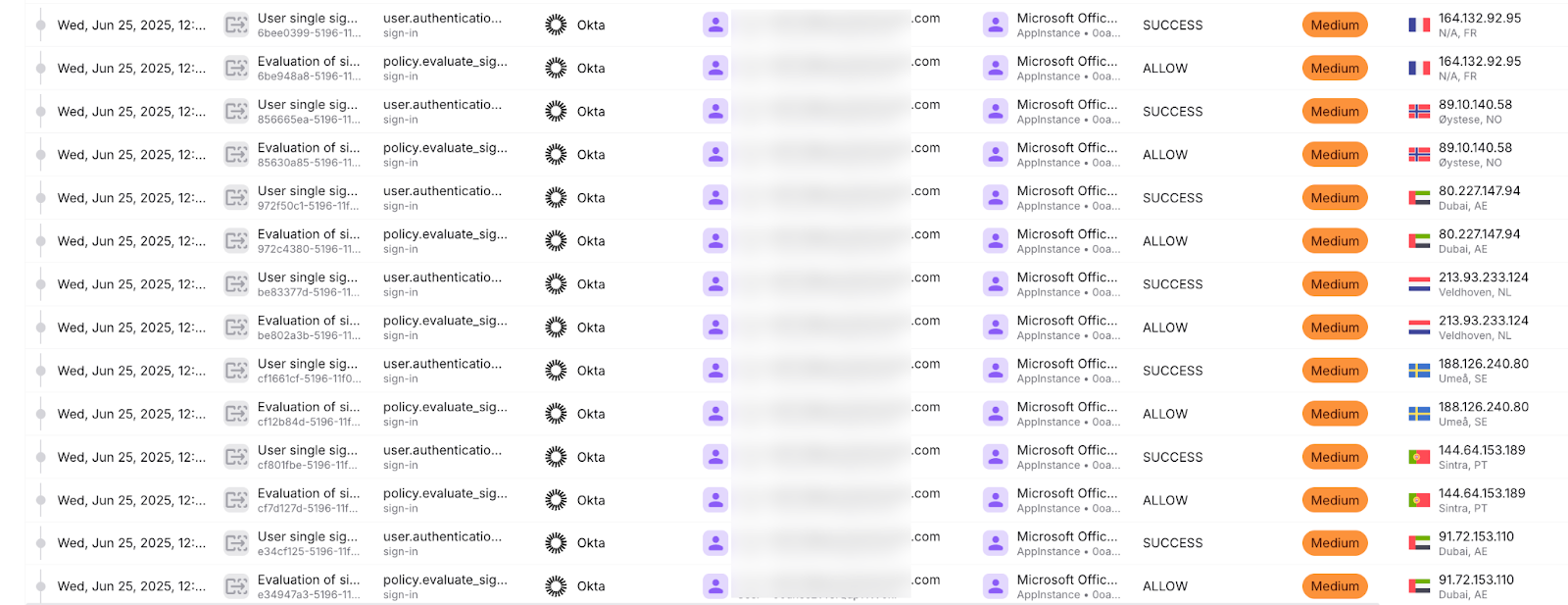
Attacker infrastructure profile
Over the course of the incident, Exaforce identified authentication attempts from more than 200 unique IP addresses across 40+ countries, involving both failed and successful logins. This diverse infrastructure is a hallmark of modern credential-based attacks and highlights the importance of geographic anomaly detection.
Some compelling stats from the investigation:
- Top Attacker Countries: Sweden, Romania, Norway, Ukraine, Tunisia, Russia, Spain, Netherlands, United Arab Emirates, Germany
- Most Active IPs (by authentication attempt volume):
- 41.224.62.206 (ORANGE – Tunisia): 166 attempts
- 89.160.38.13 (Bredband2 AB – Sweden): 165 attempts
- 176.104.241.131 (Bilink LLC – Ukraine): 155 attempts
- 109.100.41.198 (Orange Romania – Romania): 153 attempts
- 89.10.140.58 (NextGenTel AS – Norway): 151 attempts

- Widespread ASN Usage: Attackers utilized dozens of unique ASNs, including major ISPs, hosting providers, and anonymizing infrastructure like DigitalOcean and netcup GmbH, further complicating attribution and blocking.
- Repeated Patterns: Many IPs were used in short bursts, mimicking spray-and-pray behavior, while others established persistence with multiple successful logins over several days.
These findings reinforce the need for automated correlation of IP geolocation, ASN anomalies, and login behavior, capabilities that were instrumental in surfacing this attack as soon as the customer connected their Okta logs.
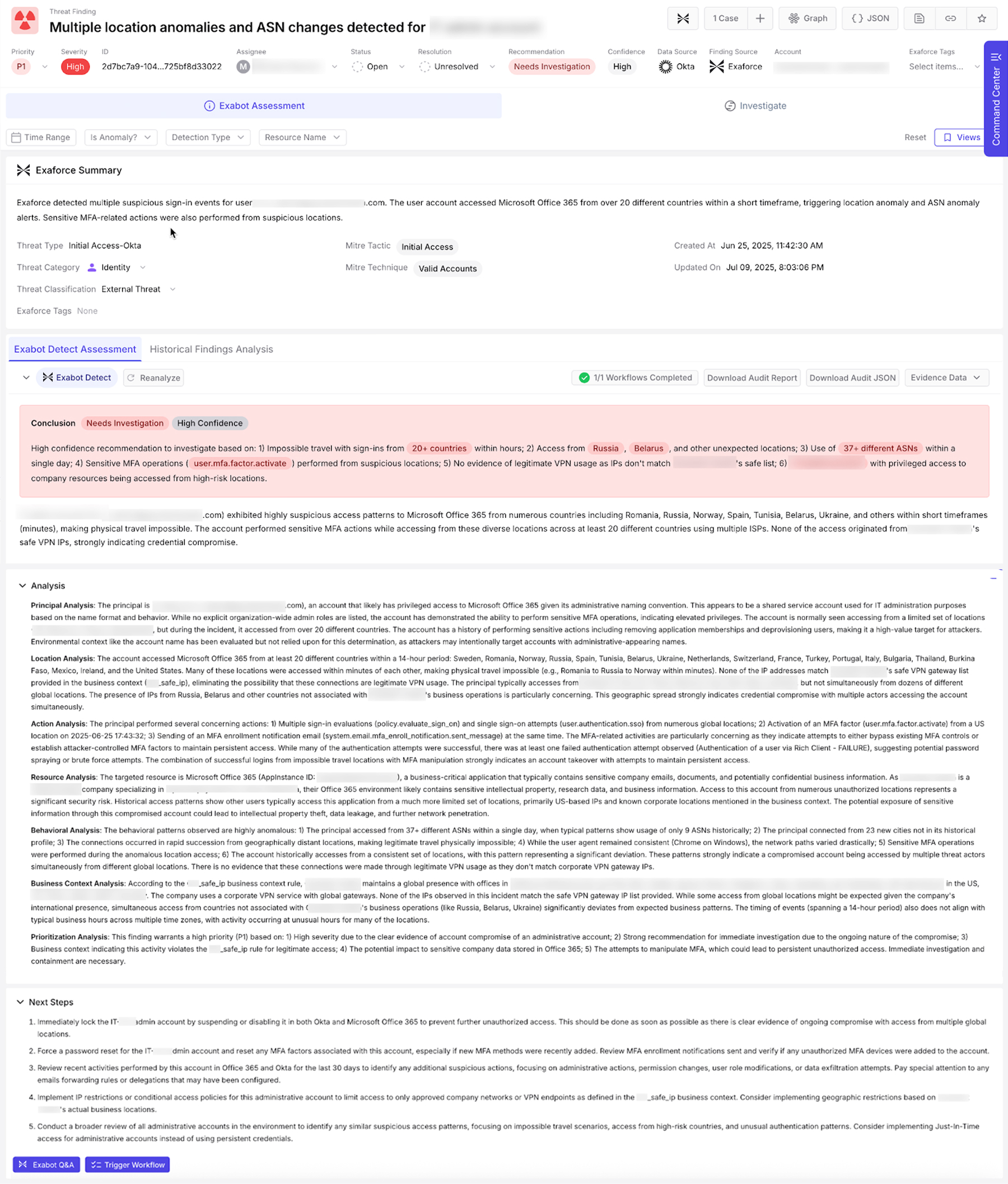
How Exaforce detected the incident
Exaforce was able to detect the intrusion the day it occurred (June 25). Detection wasn’t based on a single indicator. Exaforce's AI automatically stitched together multiple signals to arrive at a single threat finding. No rules written, no manual correlation performed.
- Impossible travel violations (e.g., logins from Sweden and Tunisia minutes apart)
- ASN anomaly detections from Okta policy evaluations
- Success/failure ratios on previously clean accounts
- Alert correlation across devices, IPs, and session behaviors
After detecting the intrusion, the customer was able to contain the threat by force logging out of all active sessions, resetting all passwords for the account, and enrolling the account in MFA to prevent another future breach.
Key lessons for defenders

How Exaforce helps
This incident was identified, investigated, and responded to inside our platform using:
- Account timeline stitching to correlate activity across time and surfaces for clearer attack progression.
- ASN-aware policy evaluations to detect access from risky or unusual networks more accurately.
- Visual behavioral analytics to help analysts quickly verify anomalies and patterns in user or system behavior.
- Alert summarization across IP clusters to highlight coordinated or related activity.
- Detailed remediation guidance to enable faster, more effective response without relying on external expertise.
Beyond just alert triage with full detection and context
When this customer connected their Okta tenant to Exaforce during onboarding, our platform immediately began behavioral analytics across identity, geo, ASN, and policy telemetry. Without custom rules, Exaforce detected a high-risk pattern: an admin-privileged service account signing in to Microsoft 365 from 40+ countries and 37+ distinct ASNs in compressed time windows - classic impossible travel plus infrastructure rotation.
Exaforce then auto-generated the finding, triaged it, and enriched it with analyst-ready context: why it matters (admin account, sensitive operations), what was observed (global spread, no matching safe VPN IPs), mapped MITRE tactic/technique (Initial Access → Valid Accounts), confidence level (High), and recommended investigation priority. All of the evidence, IP intelligence, event counts, and MFA-related actions were packaged in a single view, exportable as audit data or JSON.
The result: instead of starting from raw Okta logs and writing queries, the security team started from a high-confidence, fully scoped account-takeover investigation. This is the difference between alert noise and operational detection.
Want to see what Exaforce can do with your IdP data? We can show you what’s hiding in the data you already have. Schedule a demo to find out more.





