Since March 14th, 2025, Exaforce has been very busy helping our design partners overcome a critical attack to the software supply chain through Github. In the last 6 months, this is a second major attack experienced by our design partners to their cloud deployments and we are grateful to have delivered value to them.
What Happened?
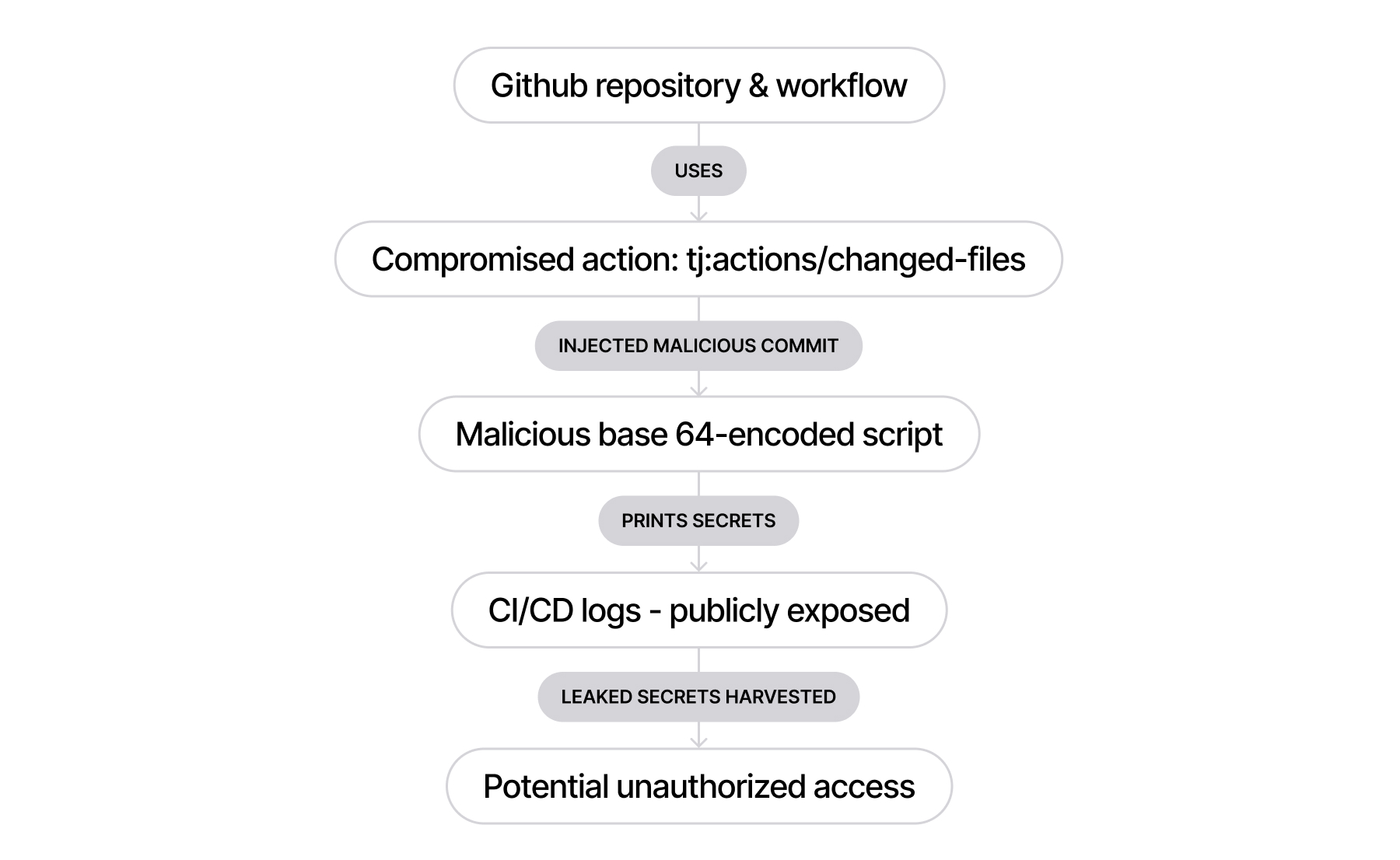
On March 14, 2025, security researchers detected unusual activity in the widely used GitHub Action tj-actions/changed-files. This action, primarily designed to list changed files in repositories, suffered a sophisticated supply chain compromise. Attackers injected malicious code into nearly all tagged versions through a malicious commit (0e58ed8671d6b60d0890c21b07f8835ace038e67).
The malicious payload was a base64-encoded script designed to print sensitive CI/CD secrets — including API keys, tokens, and credentials — directly into publicly accessible GitHub Actions build logs. Public repositories became especially vulnerable, potentially allowing anyone to harvest these exposed secrets.
Attackers retroactively updated version tags to point to the compromised commit, meaning even pinned tagged versions (if not pinned by specific commit SHAs) were vulnerable. While the script didn’t exfiltrate secrets to external servers, it exposed them publicly, leading to the critical vulnerability CVE-2025–30066.
How We Helped Our Design Partners
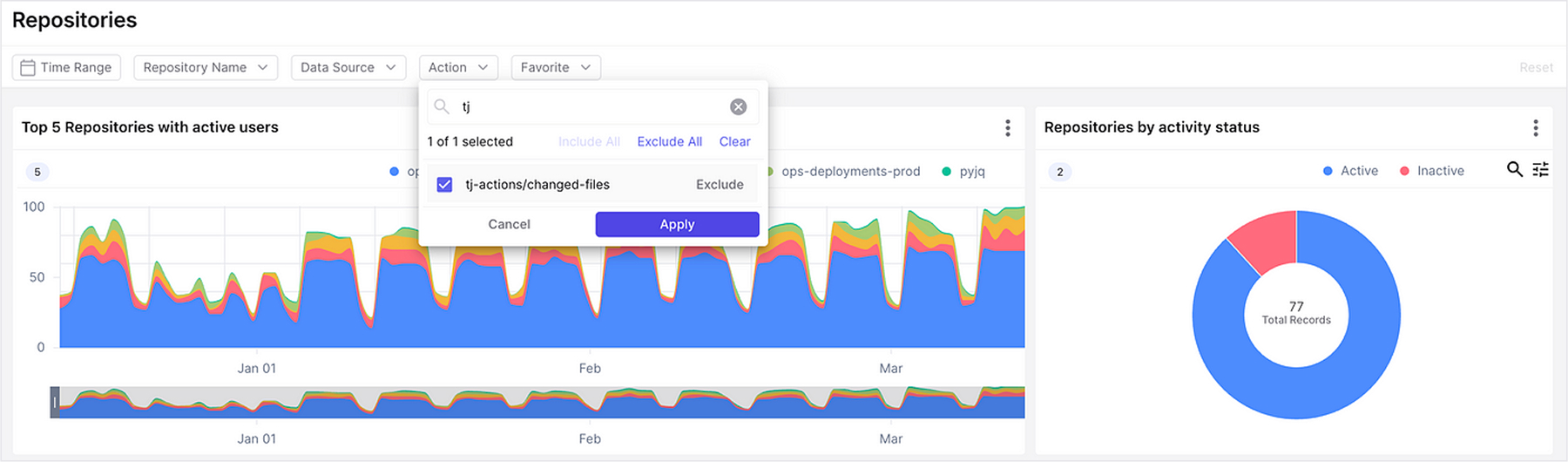
Leveraging the Exaforce Platform, we swiftly identified all customer repositories and workflows using the compromised action. Our analysis included:
Quickly querying repositories and workflows across customer accounts.
Identifying affected secrets used by compromised workflows.
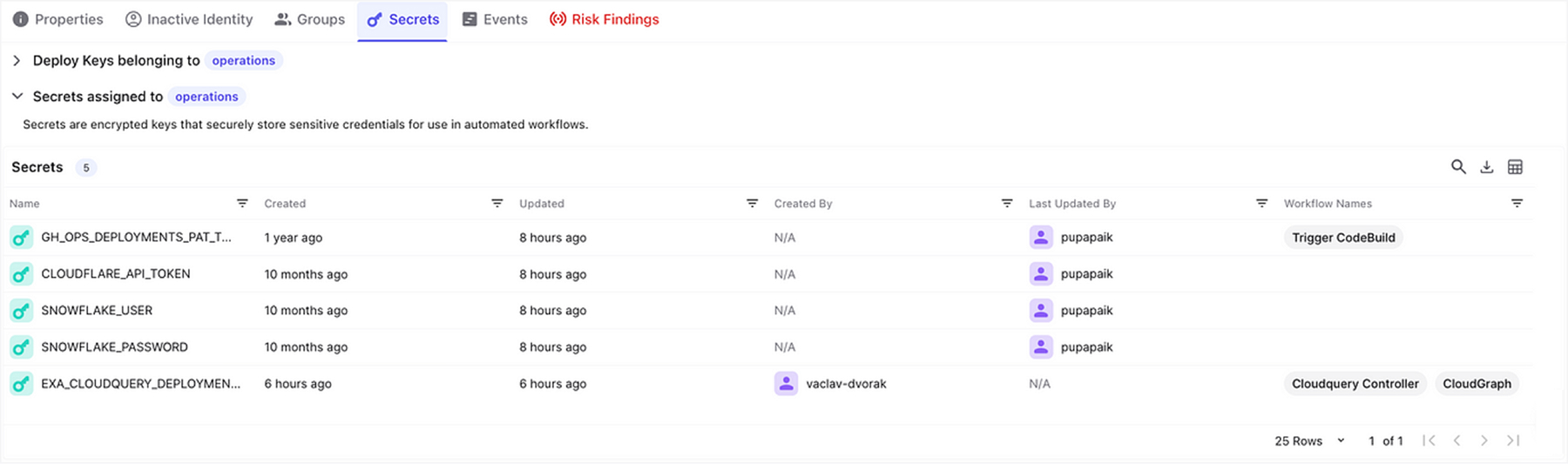
- Directly communicating these findings and recommended remediation actions to affected customers.
Our security team proactively informed customers detailing specific impacted workflows and guiding them to rotate compromised secrets immediately.
What Should You Do?
Use the below search url to look for impacted repositories. Replace the string <Your Org Name> with your github org name.
https://github.com/search?q=org%3A<Your Org Name>+tj-actions%2Fchanged-files+&type=issues
If your workflows include tj-actions/changed-files, take immediate action.
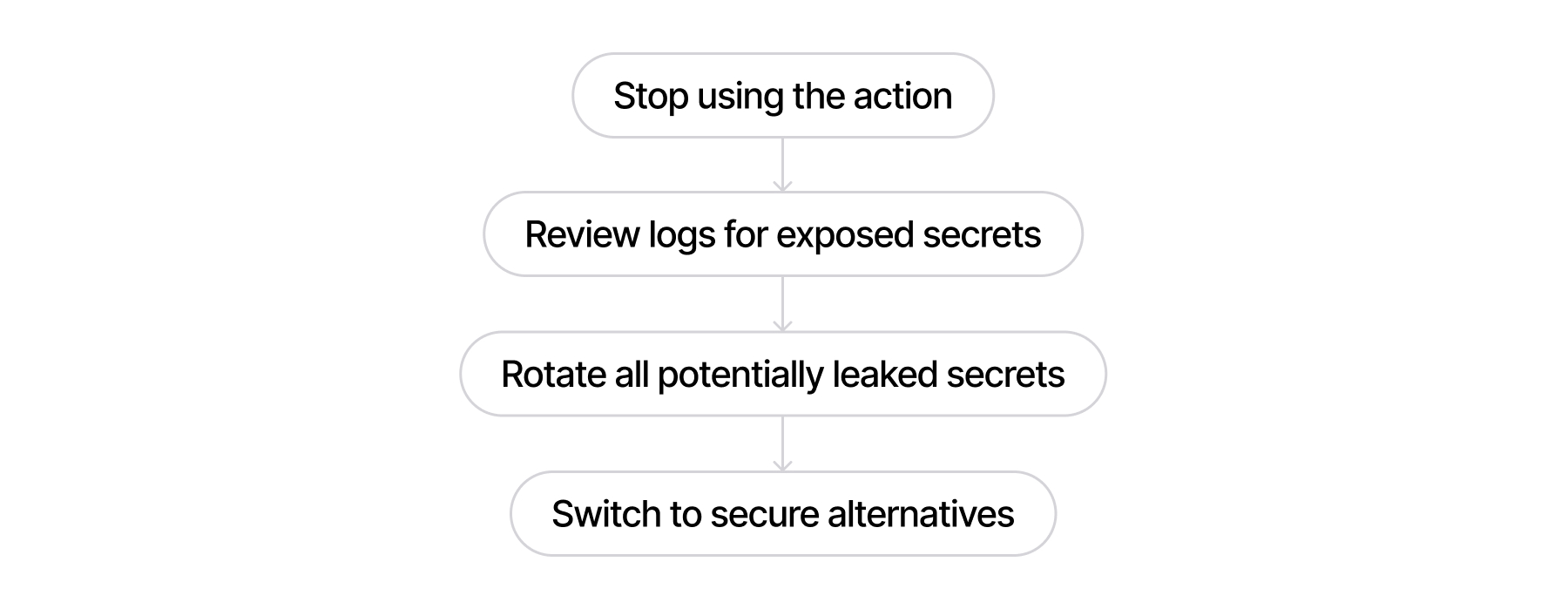
- Stop Using the Action Immediately: Remove all instances from your workflows across all branches.
- Review Logs: Inspect GitHub Actions logs from March 14–15, 2025, for exposed secrets. Assume all logged secrets are compromised, especially in public repositories.
- Rotate Secrets: Immediately rotate all potentially leaked credentials — API keys, tokens, passwords.
- Switch to Alternatives: Use secure alternatives or inline file-change detection logic until a verified safe version becomes available.
Lessons Learned
This breach highlights critical vulnerabilities inherent in software supply chains. Dependence on third-party actions requires stringent security practices:
- Pin your third party GitHub Actions to commit SHAs instead of versions
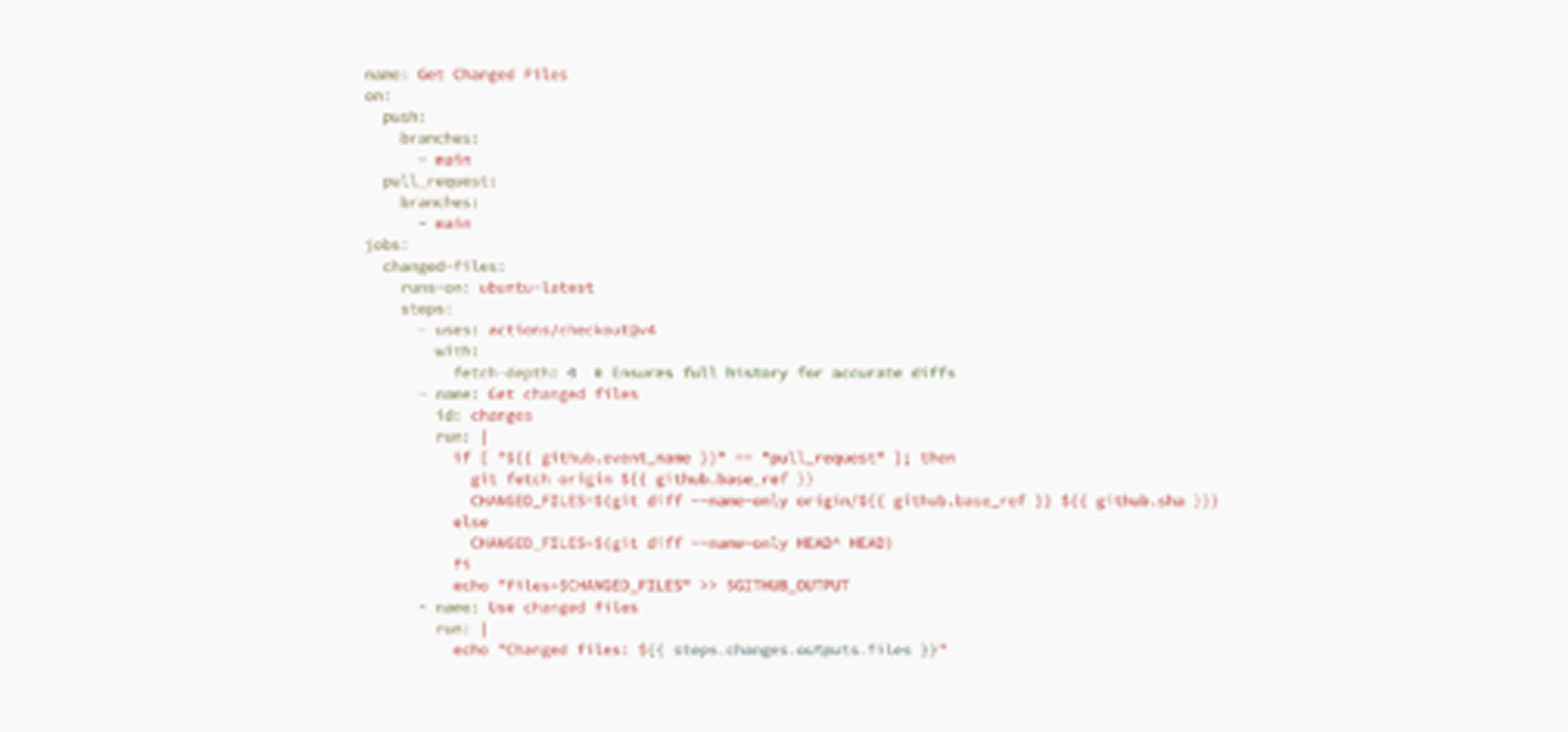
- Wherever possible, rather than relying on a third-party action you can use native Git commands within your workflow. This avoids external dependencies, reducing supply chain risks.
- Restrict permissions via minimally scoped tokens (like GITHUB_TOKEN).
- Implement continuous runtime monitoring including enabling audit logs, action logs, and capturing detailed resource information to promptly detect anomalous behavior and facilitate comprehensive investigations.
By adopting these best practices, organizations can significantly reduce the risk posed by compromised third-party software components.
Reach out to us contact@exaforce.com if you’d like to understand how we protect GitHub and other data sources from supply chain compromises and other threats.