The life of an analyst often starts with a flood of alerts. Buried in the noise may be the early signs of an attack, but finding those signs and connecting all of the necessary dots can be time-consuming and frustrating.
This isn’t a failure of detection. Most SIEMs and security tools do a good job surfacing suspicious activity, but they often present it in isolation. Without context, analysts are left wondering: is this a one-off event, or part of a bigger picture?
Exaforce takes a different approach. By intelligently aggregating findings, from collapsing duplicates to building attack chains, Exabots ensure analysts see fewer alerts, but with far more meaning. The result is less fatigue, more clarity, and faster response.
Exaforce findings represent one or more suspicious events or behavioral patterns that trigger an alert. These may be straightforward, such as compromising activity from a root account or deletion of a repository, or more statistical in nature, like an unusual sequence of actions tied to a credential, or login activity from an unexpected location. Identifying and connecting those related alerts can be deceptively difficult in complex attacks. Even more importantly, the type of relationship matters:
- Are there duplicate alerts?
- Are other analysts investigating something like this?
- Are the alerts similar but distinct, requiring correlation to build a bigger picture?
- Are they part of a broader attack chain, where seemingly unrelated events unfold as coordinated phases of an intrusion?
Exaforce addresses all of these scenarios by intelligently grouping alerts to reduce noise and maximize investigative context. Exabots achieve this by leveraging our proprietary Knowledge Model to perform this aggregation in an expedited, thorough, and consistent manner. This represents a significant departure from the traditional SOC tools, which may allow administrators and detection engineers to configure aggregation rules that aim to achieve a similar effect; however, these rules are cumbersome to build, maintain, and layer with existing detections.
Eliminating alert duplication
Many alerting tools use simple triggering mechanisms that can overwhelm analysts. A single event may be configured to raise an alert. This means that if a user performs an action that triggers an alert repeatedly, the system might generate dozens of alerts for what is, in reality, a routine activity.
Exaforce classifies these as Duplicates: alerts that are identical except for their ID and timestamp. Instead of cluttering the analyst’s queue with dozens of near-identical entries, Exaforce automatically groups these and presents them as one threat finding, without the need for configuration work by the detection engineer. The original alerts are preserved for audit or deeper review, but the analyst experiences a cleaner queue and a more concise view.
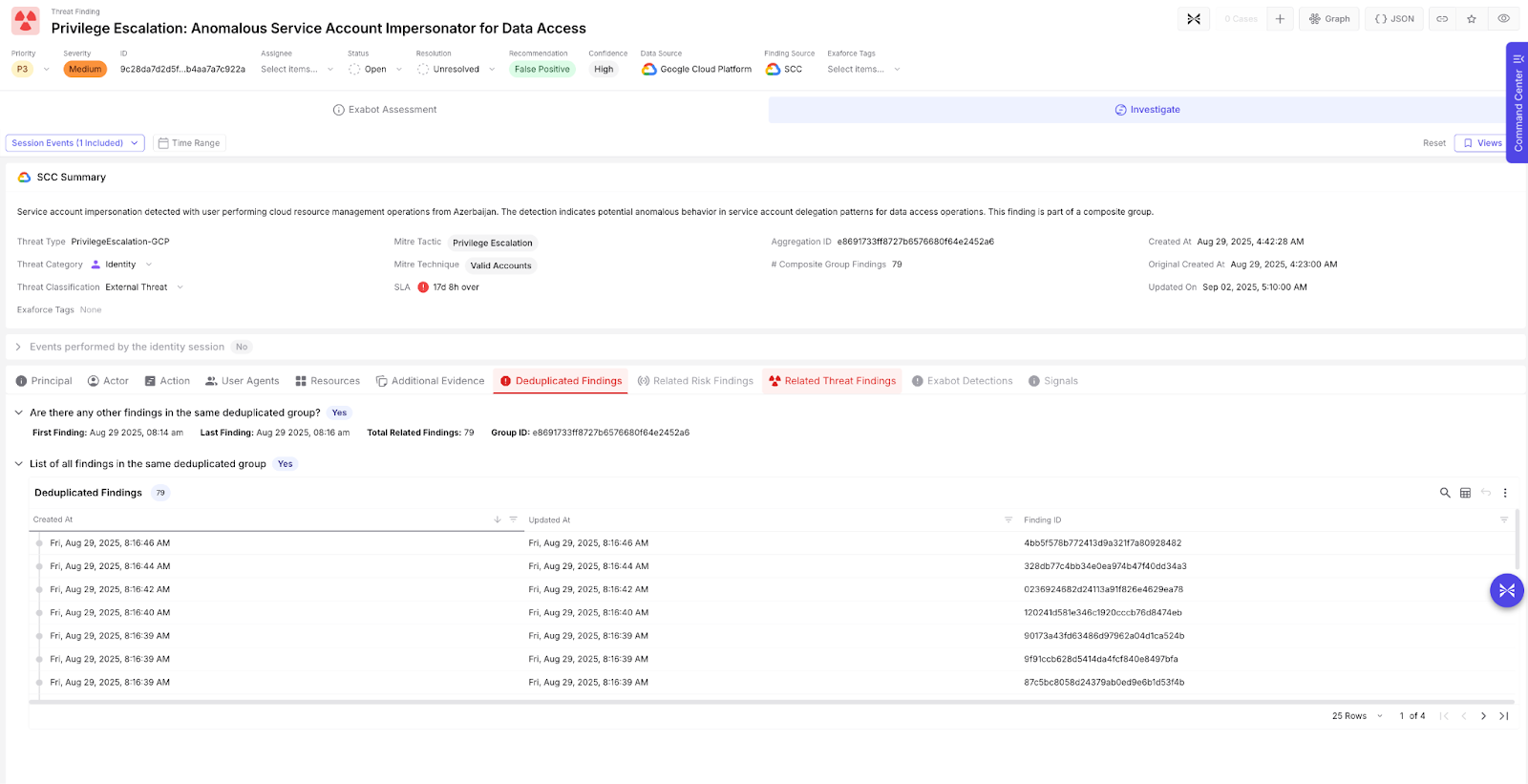
Take this Google Security Command Center (SCC) alert, for example. This google.cloud.resourcemanager.v3.Organizations.GetOrganization API call was made 79 times by a user who often performs this action. In SCC, this action is configured to automatically trigger an alert. As such, the tool simply generated 79 alerts. For the analyst, investigating these duplicated alerts is rather cumbersome. The Exaforce approach instead provides one alert and calls out the 79 duplicates. The deduplication is explained in the AI generated summary, and the individual duplicates are present in the details if needed.


Building Attack Chains
The more complex challenge is linking together alerts that may appear unrelated but are, in fact, steps in an attack sequence. Attack Chains in Exaforce are constructed using our proprietary Knowledge Model, which correlates findings across sources, entities, and timeframes.
Unlike traditional SIEM correlation rules, where analysts must predefine complex multi-level conditions, Exaforce dynamically analyzes relationships across events. This includes scenarios such as:
- Similar event patterns occurring across multiple users
- Chained role assumptions across accounts or services
- Activity by the same user spanning multiple tools or data sources
By automatically recognizing these varied relationships, Exaforce surfaces higher-order attack narratives rather than isolated alerts.
Let’s take a look at an example in which an admin user’s accounts were compromised and access to multiple applications (AWS, Google Workspace) was compromised. Exaforce identified individual attempts, which were assessed separately with their own severities and priorities, and then grouped them into this Attack Chain to tell a complete story and provide a holistic severity and priority.

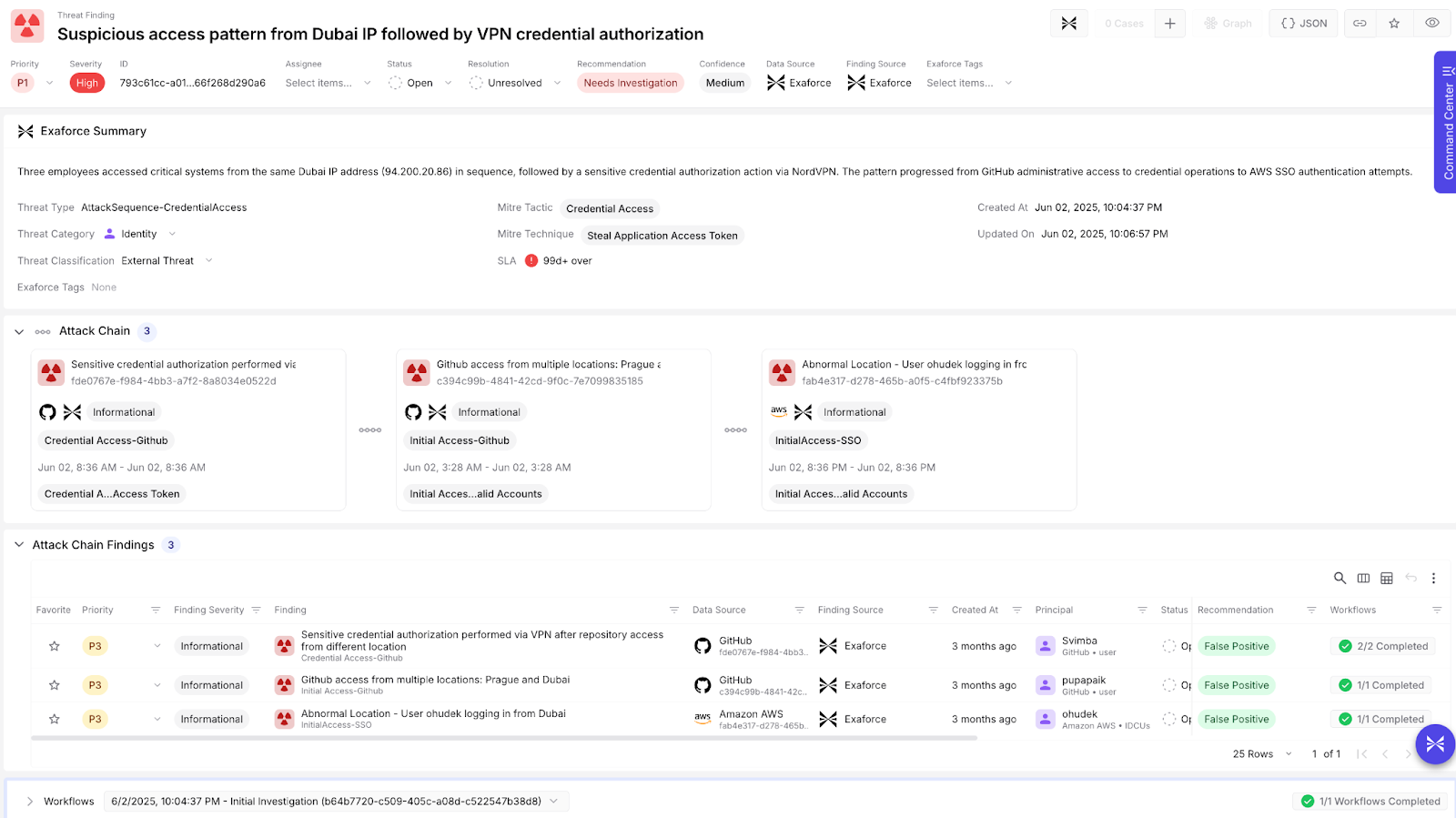
In some cases, the relationship is not as straightforward. In the example below, three distinct users were found exhibiting similar suspicious behavior across two different apps (GitHub and AWS). Assessed individually, each of these was deemed a low severity false positive, but when taken in context, the chain certainly merits investigation.
Related & historical findings
Not every alert can, or should, be collapsed into a duplicate or chained into a larger attack narrative; some findings are distinct but contextually relevant to another alert. Exaforce identifies and surfaces these as Related Findings, giving analysts the surrounding context they need. These relationships are also shared with Exabots to guide automated triage and enrichment.
A subset of related findings may have already been analyzed and evaluated. Exaforce incorporates prior assessments into the investigation process by analyzing historical findings and their resolutions. The closed findings’ closure notes, recommendations, verdicts, and even the investigative path taken are all captured in our Knowledge Model. When a similar alert arises, this history is automatically leveraged by Exabots to guide analysis and provide additional context. Analysts also benefit from this codification of institutional knowledge, avoiding repeated effort and improving the consistency of responses over time.
Below is an example of Exabot’s Historical Analysis in action. This alert, which looks real, was reclassified as a false positive because similar alerts were historically false positives. The pattern is observed and explained with similar findings listed for evidence. Exabots learn, adapt, and improve with each case.

Why aggregation matters
The Exabot system of aggregations addresses several core SOC challenges. By intelligently identifying, classifying, grouping, and assessing each set of alerts, Exabots provide high fidelity analysis themselves and pass along that context to human analysts.
- Reduced alert fatigue through deduplication
- Greater investigative clarity via context-rich grouping
- Faster response by surfacing full attack sequences rather than piecemeal signals
- Reduced detection complexity by offloading aggregation logic to Exaforce
With Exaforce, analysts spend less time triaging noise and more time responding to what truly matters. Sign up for a demo to see it in action.






