Security Operations Centers (SOCs) have long been the front line of defense against cyberattacks. But with today’s scale of alerts, cloud complexity, and identity-driven risks, traditional SOCs struggle to keep up. That’s where the AI SOC comes in.
An AI SOC, or Artificial Intelligence-powered Security Operations Center, uses machine learning, automation, and autonomous agents to handle tasks that once overwhelmed human analysts. Instead of drowning in false positives, teams can now detect, triage, investigate, and respond at machine speed, while still applying human judgment where it matters most.
This article breaks down what an “AI SOC” is, how it differs from traditional SOCs, the evolving role of the AI SOC analyst, and why autonomous operations are quickly becoming the future of security. For the next step in this evolution, explore Agentic SOCs.
What is an AI SOC?
An AI SOC (Artificial Intelligence-powered Security Operations Center) utilizes machine learning, automation, and LLM agents to execute tasks that traditionally consumed analyst time.
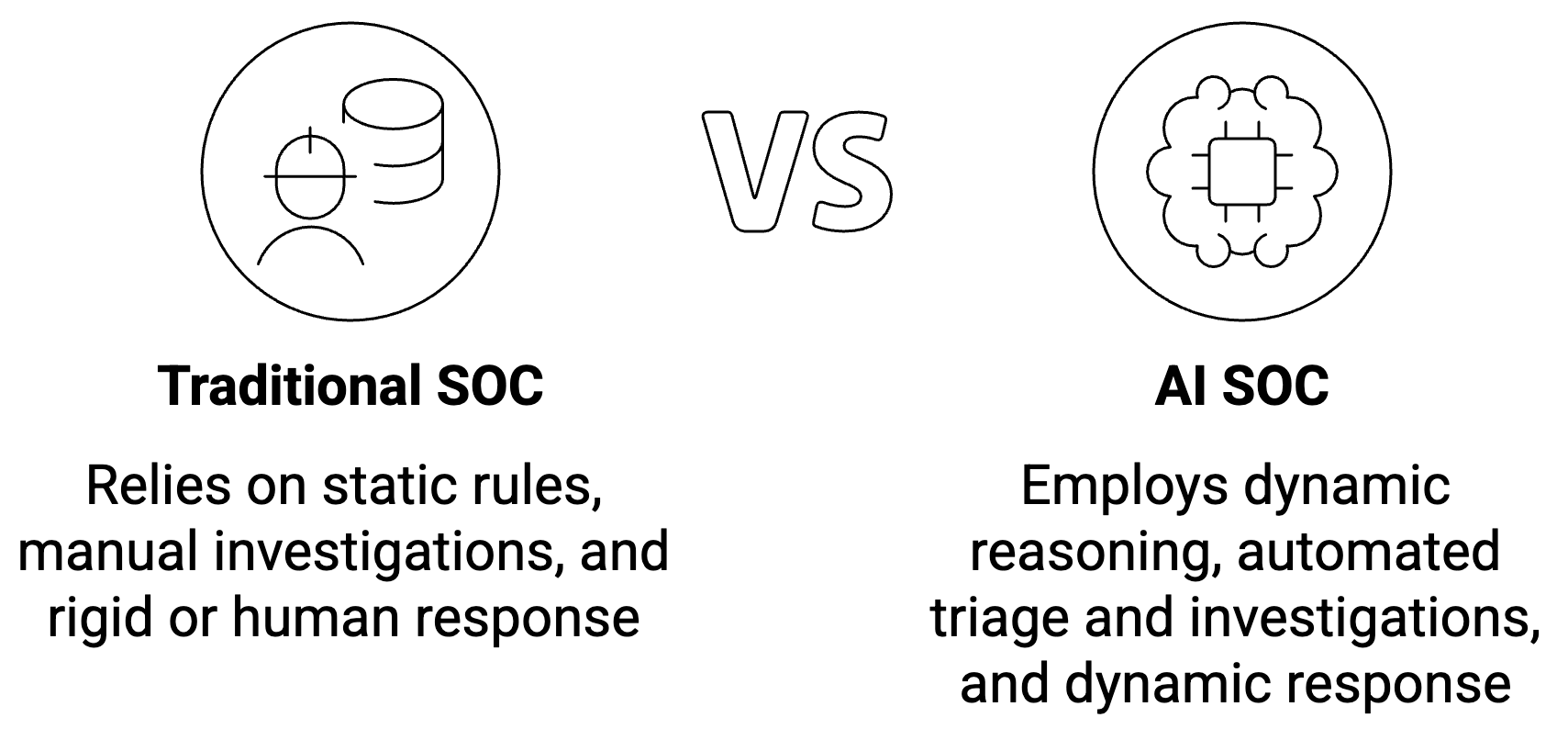
Unlike legacy setups that rely on static, brittle rules (such as "if X happens, alert Y"), an AI SOC employs dynamic reasoning. It ingests data across the entire stack, including logs, identities, cloud configurations, and code, to understand context. It determines if an anomaly is a genuine threat or benign behavior by analyzing the full timeline of activity rather than just a single data point.
Essentially, it handles the heavy lifting of detection, triage, and initial investigation so human teams can focus on strategic decision-making.
Why traditional SOCs fall short
Legacy SOCs rely on humans manually correlating alerts, switching between dashboards, and executing queries. This approach creates bottlenecks:
- Alert overload: a majority of alerts are false positives.
- Manual investigations: Analysts spend a large amount of their time gathering data rather than responding.
- Rule-based detections: Detection engineers are unable to keep up with new attack surfaces and fast evolving attack patterns.
- Talent gap: Over 3.5M unfilled security jobs worldwide.
- High costs: SIEM storage and licensing fees continue to rise as data grows.
An autonomous SOC powered by AI directly addresses these issues by reducing repetitive work and scaling analyst capacity.
Elevating the analyst role
There is a misconception that AI aims to replace human analysts. In reality, the AI SOC creates a new, more strategic role for analysts. By offloading repetitive tasks, such as running queries or correlating logs, the focus shifts from data aggregation to high-value security work.
This shift moves the analyst from triage to oversight. Instead of manually validating every alert, analysts supervise AI agents to ensure decisions align with business risk. Furthermore, the role evolves from reactive to proactive operations. Time previously spent on false positives is now dedicated to proactive threat hunting and vulnerability management. Finally, analysts provide strategic context by teaching the AI business-specific nuances (like knowing that specific behavior is normal for the Finance team during quarter-end) which refines the system over time.
Benefits of an AI SOC
Organizations moving to an AI SOC realize measurable improvements, starting with a significant reduction in false positives through automated triage. By eliminating disjointed "swivel-chair" workflows, these systems boost analyst productivity and lower total cost of ownership by reducing reliance on heavy SIEM data ingestion. Furthermore, AI-led investigations and automated responses drive faster MTTI and MTTR, ultimately empowering teams to shift their focus from reactive firefighting to proactive defense.
Real-world use cases
- Cloud Security: Detecting risky S3 bucket policies or IAM privilege escalation attempts.
- Identity Security: Mapping session hijacks, OAuth token theft, or impossible travel anomalies.
- Insider Threats: Correlating abnormal file downloads with SaaS logins and HR signals.
- Email: Detecting compromised accounts sending phishing campaigns.
- SaaS: Spotting abnormally high volumes of repository cloning.
- Endpoint: Identifying lateral movement across devices at scale.
An AI SOC ties these signals together into a unified investigation, something a traditional SIEM or UEBA tool cannot do alone.
Challenges in building an AI SOC
Building an AI SOC presents distinct challenges, primarily because AI is only as effective as the quality of the data it ingests. Beyond data integrity, organizations must navigate the cultural shift of adopting automated workflows and ensure strict alignment with compliance frameworks like SOC 2, HIPAA, and GDPR. Crucially, analysts need to trust the system through transparent decision-making while retaining the ability to pivot into deeper, manual threat hunting when necessary.
How to evaluate an AI SOC vendor
When choosing a platform, ask:
- Does it reduce false positives with measurable metrics?
- Can it investigate autonomously across cloud, identity, SaaS, and code?
- Does it offer business context rules to tailor detections?
- Are there AI agents for triage, investigation, detection, and response?
- Is compliance built in (SOC 2, ISO, HIPAA)?
These questions help separate real AI SOC platforms from legacy SIEMs with “AI” marketing.
The future is AI
AI SOC is the natural evolution of security operations. With autonomous SOC platforms, SOC analysts spend less time on false positives and more time protecting the business. Whether you’re starting without a SOC or looking to improve an existing SOC, the shift is here.
At Exaforce, we built our platform from the ground up to power the AI SOC with Exabot agents that triage, investigate, and respond like seasoned analysts. Ready to see how an AI SOC could transform your security operations? Request a demo today.