Modern attackers move fast, and your security operations have to keep up. If your analysts are still bouncing between tools, manually stitching logs, and debating which alert to open first, you do not have a TDIR (threat detection, investigation, and response) strategy. A disciplined TDIR approach turns that chaos into a repeatable, measurable way to handle threat detection, investigation, and response at scale.
For security leaders, SOC managers, and IT owners of detection stacks, TDIR is emerging as a practical architecture for closing visibility gaps, lowering mean time to respond, and making better use of scarce analyst time. Done well, it becomes the connective tissue between your telemetry, your people, and your automation. Done poorly, it is just another acronym the board forgets by the next incident review.
This article breaks down what TDIR really is, how it fits alongside SIEM, SOAR, XDR, and MDR, and how to design a roadmap you can execute in the next 12 to 24 months.
What is TDIR in modern security operations?
At its core, TDIR is an operating model and technology stack that continuously performs threat detection, investigation, and response on the signals that matter most to your business. Instead of focusing only on log collection or only on automated playbooks, TDIR emphasizes the full lifecycle from initial signal through to verified containment and lessons learned.
Industry frameworks such as NIST’s incident response guidance stress that detection and response must function as a continuous loop rather than isolated stages. CISA’s best practices for event logging reach the same conclusion that you cannot respond effectively if your logging and telemetry strategy is fragmented across tools and teams.
In practical terms, TDIR is what connects your telemetry to business outcomes. It is less about buying a specific product and more about orchestrating the flow from raw signal to verified decision in a consistent way.
How TDIR differs from traditional SOC tooling
Many teams claim they already “do TDIR” because they have a SIEM, a SOAR platform, and an EDR tool. In reality, their workflows often look like a series of disconnected handoffs and swivel chair investigations.
A healthy TDIR program is built around end-to-end outcomes such as “detect and contain risky OAuth application abuse in 30 minutes or less,” not just around rules, dashboards, or playbooks in a single system. SIEM remains central to log aggregation, SOAR remains valuable for orchestrating actions, and EDR remains critical for host-level visibility. The difference is that TDIR defines how these tools participate in a single lifecycle for detection, investigation, and response, instead of leaving analysts to glue everything together ticket by ticket.
The core capabilities of a TDIR engine
Regardless of vendor choices, mature TDIR programs tend to converge on a similar set of capabilities that reinforce each other. Conceptually, you can think of a TDIR engine like this:
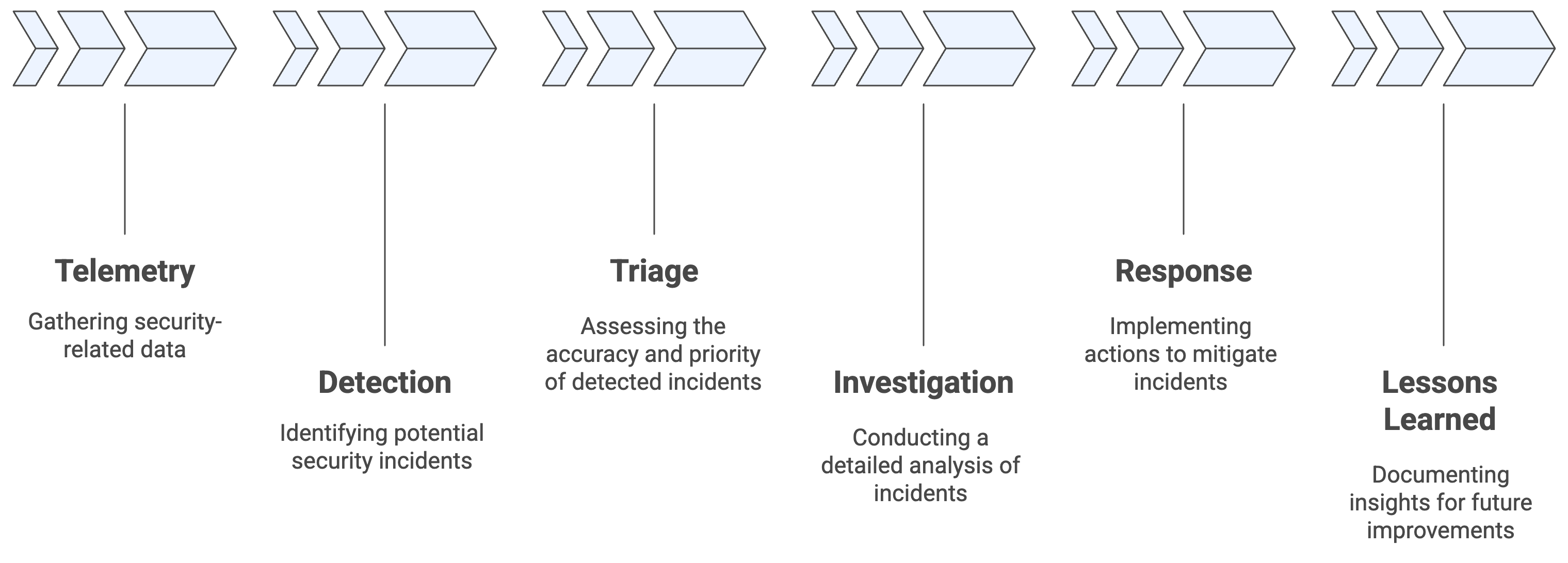
Each stage can be implemented with different products, but the value comes from the continuity of the flow, not from any single tool.
Centralized and normalized security data
Effective TDIR depends on high quality, normalized telemetry across endpoints, cloud infrastructure, SaaS, identity, and network. Without this foundation, threat detection, investigation, and response quickly fragment along technology silos, and every incident becomes a bespoke project.
CISA’s guidance on event logging repeatedly returns to the basics, saying it’s best to capture the right events, retain them for long enough, and ensure they are searchable at investigation time. Mature programs define explicit logging baselines for crown jewel systems and identity providers, and they periodically validate that those baselines are still in place.
High fidelity detection mapped to attacker behavior
The second pillar of TDIR is the ability to detect meaningful attacker behavior, not just policy violations or noisy signatures. Leading teams align their detection content with frameworks such as MITRE ATT&CK, which describe adversary tactics and techniques in a structured, testable way.
This mapping helps SOC leaders answer uncomfortable questions like which stages of an attack can we reliably see today and where are our blind spots. In a mature TDIR implementation, each detection has a defined downstream path, such as what enrichment is required, who owns the investigation, how “true positives” are defined, and what the default response options look like. Those decisions are encoded in the platform so they survive staff turnover and shift changes.
Repeatable investigations with human grade reasoning
TDIR is also about making every investigation more repeatable and more defensible. That means standardizing how context is pulled, how timelines are built, and how analysts decide whether something is benign, suspicious, or malicious.
Gartner’s work on modern SOC strategies highlights that high performing teams invest in investigation playbooks, collaborative case management, and narrative reporting that business stakeholders can understand. A robust TDIR platform bakes these habits into the workflow so junior analysts can benefit from the patterns discovered by your most senior responders.
Automation, AI, and agentic SOC platforms
The volume and complexity of signals make manual TDIR impossible at any meaningful scale. This is why many organizations are exploring AI-enhanced or agentic SOC platforms. These platforms can automatically triage alerts, enrich them with context, and perform large parts of the investigation workload while still keeping humans in control for high impact decisions.
Exaforce, for example, couples autonomous AI agents with rich security data so that threat detection, investigation, and response become continuous rather than ticket driven. Teams that are evaluating an AI-centric approach can look at how AI SOC platforms orchestrate TDIR flows across detection, triage, investigation, and containment, instead of forcing analysts to supervise every low level step.
Designing a practical TDIR roadmap
The key to a successful TDIR rollout is to build a roadmap that is realistic, sequenced, and measured.
Start by assessing where your SOC stands today across a few dimensions: telemetry coverage, detection quality, investigation workflows, response playbooks, and use of automation. Some teams use formal maturity models, others prefer simple scorecards, but the goal is to establish a baseline that highlights where TDIR can have the most immediate impact.
Common anti-patterns include over reliance on manual triage queues that treat all alerts as equal, a lack of ownership for specific threat scenarios, and an excessive focus on tuning tools rather than improving end-to-end outcomes. Addressing those issues early prevents your TDIR initiative from becoming just another configuration project.
From that baseline, leadership can define a staged roadmap that aligns with budget cycles and risk appetite. For example:
- Consolidate telemetry and normalize logs for high value identities, SaaS, and cloud environments.
- Map existing detection content to MITRE ATT&CK so you can identify and prioritize coverage gaps.
- Standardize investigation workflows around a central case management system that captures evidence, timelines, and decisions.
- Introduce automation for low risk, high volume response actions, such as session revocations and device isolation.
- Evaluate AI-assisted or agentic SOC capabilities that can take on full TDIR workflows for selected use cases, such as phishing or credential misuse.
Throughout this roadmap, treat TDIR as an evolving product inside your organization rather than a static set of tools. That mindset encourages continuous feedback from analysts, incident commanders, and business stakeholders.
Metrics that prove the TDIR value to the business
Security leaders often struggle to translate investments in TDIR into language that resonates with the board and with other executives. The solution is to focus on metrics that tie threat detection, investigation, and response directly to risk reduction and productivity, not just to technology activity.
Useful metrics include:
- Mean time to detect, investigate, and contain priority incidents, segmented by attack type or business unit.
- Percentage of high severity detections that lead to confirmed incidents, as a proxy for TDIR precision.
- Analyst hours saved through automation or AI-driven triage, compared with historical baselines.
- Reduction in exposure time for specific scenarios, such as compromised user sessions or misconfigured cloud resources.
Integrating TDIR with MDR and AI SOC services
Few organizations have the resources or appetite to run every aspect of TDIR alone. This is why many pair internal capabilities with managed detection and response (MDR) or AI-augmented SOC services. The goal is to extend coverage and scale using a shared operating model.
When you engage MDR or AI SOC partners, TDIR becomes the common language. Your providers contribute playbooks, detections, and 24x7 monitoring, while your internal team brings business context, escalation paths, and ownership of high impact decisions. Platforms that deliver MDR and an AI SOC on the same foundation can simplify this collaboration.
Bringing TDIR to life in your SOC
TDIR is a way to align people, process, and technology around a single outcome. It helps with consistently detecting, investigating, and responding to the threats that matter most before they become business crises.
By treating TDIR as a long term program and by leveraging modern AI-powered SOC platforms, you can move your organization from reactive firefighting to predictable, data driven security operations. Start with one or two high impact use cases, measure the improvements in detection and response, then expand.
If you want to see what a mature, AI assisted TDIR implementation looks like in practice, consider scheduling a demo or trial with an agentic SOC platform provider and using those sessions to benchmark your current approach.