The cloud has given teams unprecedented agility, scale, and business velocity. It has also expanded the attack surface faster than most teams can keep up. Every day, new misconfigurations appear, identity boundaries shift, and workloads spin up and down in AWS, Azure, and GCP. Traditional monitoring falls short because it was never designed for an environment where infrastructure exists for hours rather than years.
This is where cloud detection and response (CDR) tools become essential. When done well, CDR delivers visibility, context, and action at the speed of cloud operations. When done poorly, teams drown in noise or miss the signal entirely. In this post, we explore how to build, refine, and operate a strong cloud detection and response strategy that supports enterprise scale without unnecessary complexity. While Exaforce works with customers globally to implement cloud security operations, this article focuses on best practices rather than promotion.
What cloud detection and response really means
CDR is the combination of telemetry collection, behavioral analytics, automated response, and threat-informed investigation. Effective CDR does three things consistently:
- Detect malicious activity or risky patterns early in the kill chain.
- Respond with automated or guided remediation that mitigates the impact.
- Learn and adapt detection logic based on attacker behavior.
CDR evolved because legacy SIEM and endpoint tools struggled to understand ephemeral resources and API-driven compromise paths. Modern attackers abuse roles instead of endpoints, elevate privileges through IAM policies, and pivot laterally between managed services. Without cloud native visibility and detection logic, teams lose situational awareness.
Why CDR matters more than ever
Security leaders know cloud adoption is no longer gradual. According to research from the Cloud Security Alliance, enterprises now operate across multiple providers and hundreds of integrated services. This has created unique challenges:
- Workloads scale faster than SOC teams.
- Every configuration is a potential vulnerability.
- Identity is the new perimeter.
- Data loss paths are cloud native, not endpoint bound.
CDR provides the real time perspective needed to monitor, prioritize, and contain risk before it escalates.
Core components of an effective cloud detection and response program
Telemetry and log ingestion from AWS, Azure, and GCP
Visibility begins with collecting the right data. As NIST guidance on cloud security best practices highlights, coverage across the control plane, data plane, and network layer is critical. Key log sources include:
- AWS CloudTrail, VPC flow logs, GuardDuty findings
- Azure Activity Logs, Azure AD sign-ins, NSG flow logs
- GCP Cloud Audit Logs, VPC logs, IAM access logs
The challenge is volume. Raw logs generate noise without correlation and context. CDR platforms must normalize and enrich data across providers so analysts can search and pivot quickly.
Identity and access monitoring
Compromise rarely starts with malware in cloud environments. It starts with keys, tokens, and permissions. Monitoring IAM changes, role assumptions, and high-risk privilege grants is a foundational CDR capability.
Automated response workflows
SOC teams achieve scale through automation, including isolate resources, revoke credentials, quarantine objects, or enforce new policies. Response speed reduces breach impact more effectively than preventative tools alone.
Behavior-based threat detection
Static rules detect known indicators but miss unknown attack patterns. CDR solutions must leverage anomaly detection, risk-scoring logic, and MITRE ATT&CK cloud mapping. This adds context. For example, not every S3 policy change is malicious, but one performed from a new geo location, by a new principal, followed by data transfer is suspicious.
Architecture of a cloud detection and response workflow
Below is a simplified representation of how telemetry flows through an enterprise CDR pipeline.
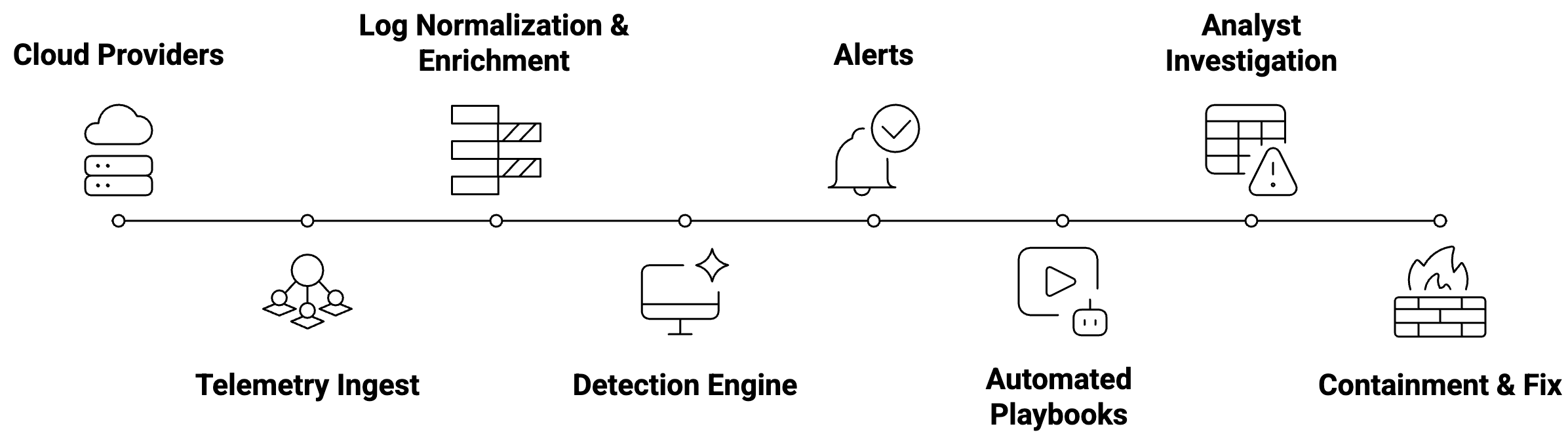
This chart is intentionally high level. In real environments, there are layers of threat intel, asset context, user behavior analytics, and cross-SaaS telemetry integration. The architecture scales when teams can modify rules without rewriting pipelines.
Managed cloud detection and response versus in-house build
Security leaders often ask whether they should build or outsource. The answer depends on maturity, scale, and operational appetite.
When in-house CDR makes sense
Organizations with deep engineering talent and a cloud-first culture may prefer to own detection logic. They can customize pipelines, integrate internal tooling, and adapt quickly to niche risks. However, this requires sustained investment in code, detection engineering, and SOC training.
When managed, CDR accelerates outcomes
A managed cloud detection and response service gives teams immediate coverage while reducing operational burden. This matters for fast scaling companies with limited detection engineering capacity.
Practical guidance for SOC managers
CDR programs evolve best through iterative improvement. The following numbered guidance provides a roadmap:
- Instrument core logs first, then expand. Coverage beats depth.
- Correlate identity events aggressively. IAM is your control plane.
- Add automation early to avoid manual bottlenecks.
- Align detections to MITRE ATT&CK cloud techniques.
- Test response playbooks quarterly in simulated real incidents.
Teams that adopt these practices often reduce mean time to detect and respond, even without new tooling. When evaluating an AI driven investigation workflow, many organizations benchmark decision speed, lateral movement detection, and enrichment coverage. Internal workflow maturity matters as much as tooling.
Putting cloud detection and response into practice
Cloud detection and response is now a requirement for any organization operating at scale in AWS, Azure, or GCP. SOC managers who develop disciplined visibility, behavior analytics, and automated response workflows can outpace adversaries rather than chase them. A strong CDR foundation lowers risk, accelerates investigations, and supports continuous cloud growth without adding unnecessary operational drag.
Enterprises evaluating cloud security modernization can explore how Exaforce supports CDR implementation and managed operations within diverse environments. A guided proof of value or architecture review may be the most direct next step for organizations seeking measurable improvement.