A few years ago, the idea that a small company could run its own SOC would have been highly unlikely. That kind of operation required a bench of analysts, detection engineers, 24/7 shift coverage, and the institutional knowledge to make sense of it all. The natural answer for most organizations was to hand the keys to a Managed Security Services Provider (MSSP) and hope for the best.
For many teams, "hope for the best" turned out to be the operative phrase. The SOC outsourcing model was built on the reasonable premise that security operations are complex, talent is scarce, and specialization should produce better outcomes. In practice, the experience has been uneven with analysts churn, lost context, and alerts that get punted back without enrichment. The organization that outsourced to reduce its burden often ends up doing much of the same work, just at a higher price point.
Something has shifted, though. AI-driven security operations have changed what a small team can accomplish, and the in-house vs. outsource question no longer tilts as heavily toward "outsource" as it once did. More organizations are pulling some or all of their security operations back in-house, because the math is fundamentally different now.
What's actually broken about outsourced SOCs
The issues with MSSP relationships tend to surface slowly, then all at once. They rarely come from bad intentions on the provider's side. More often, they're structural.
Start with knowledge loss. The average SOC analyst tenure is less than 18 months, and that figure may be generous. Every time an analyst leaves, whether at your MSSP or on your internal team, whatever they understood about your environment leaves with them. The next person ramps up, gets productive, and then also leaves. The result is a sawtooth pattern, where quality climbs after onboarding, degrades with churn, and climbs again with the replacement. With an MSSP, you have even less visibility into where you are on that curve at any given moment.
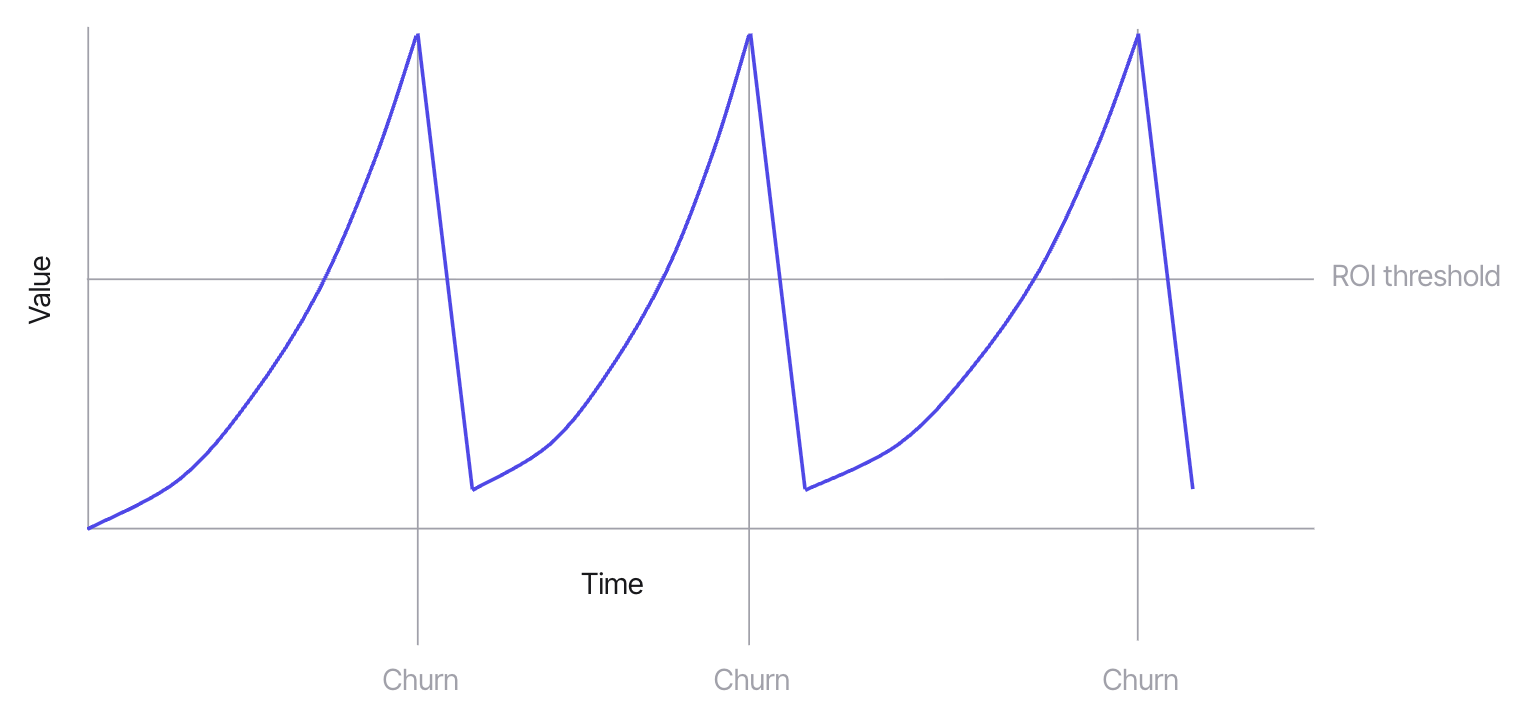
One Exaforce customer, a large institution, lived this cycle. They had originally built their SOC in-house. When burnout and turnover made that unsustainable, they outsourced to an MSSP. The peaks and valleys just shifted to the provider side. Good alerts one month, bad alerts the next. They never got the consistency they were paying for.
Then there's the context gap. A frustration we hear constantly from teams that have outsourced is what happens when the MSSP isn't sure about an alert. Rather than resolving it, the alert gets kicked back to the internal team, often with minimal enrichment. Your people are left investigating something they don't have context on, using tools they may not have direct access to, for a detection they didn't write. That defeats much of the point.
And finally, opacity. A lot of MSSP engagements still run as a black box. You send them your logs, and they send you alerts. The tuning decisions, the detection logic, the triage criteria, all of it happens behind a curtain. That makes it hard to evaluate quality, harder to improve coverage, and close to impossible to build internal competency alongside the outsourced relationship.
None of this means outsourcing is inherently wrong. But the value proposition was always more fragile than the pitch suggested, because it rested almost entirely on the people doing the work.
Why AI SOC changes the equation
What makes repatriation viable now, when it wasn't a few years ago, comes down to a few specific things AI-driven platforms have changed about the operational model.
The biggest one is that institutional knowledge finally stays put. In a traditional SOC, whether in-house or outsourced, knowledge lives in people's heads, in their Confluence pages, in the tribal understanding of "oh, that alert always fires on new hire day, ignore it." When those people leave, that understanding goes with them.
With an AI SOC platform, that knowledge gets embedded in the system. When an analyst marks an alert as a false positive and explains why, that reasoning persists. The next time a similar alert fires, the system already has the historical context. Business context works the same way. One of our customers told us that "the first Tuesday of every month is new hire day," and that on those days, you'll see a burst of MFA registrations from accounts created up to 45 days prior. In a traditional SOC, that knowledge lived in one person's head, or maybe in a wiki nobody reads. Now it's encoded in the system and applied automatically. Turnover still hurts, but it doesn't reset the clock.
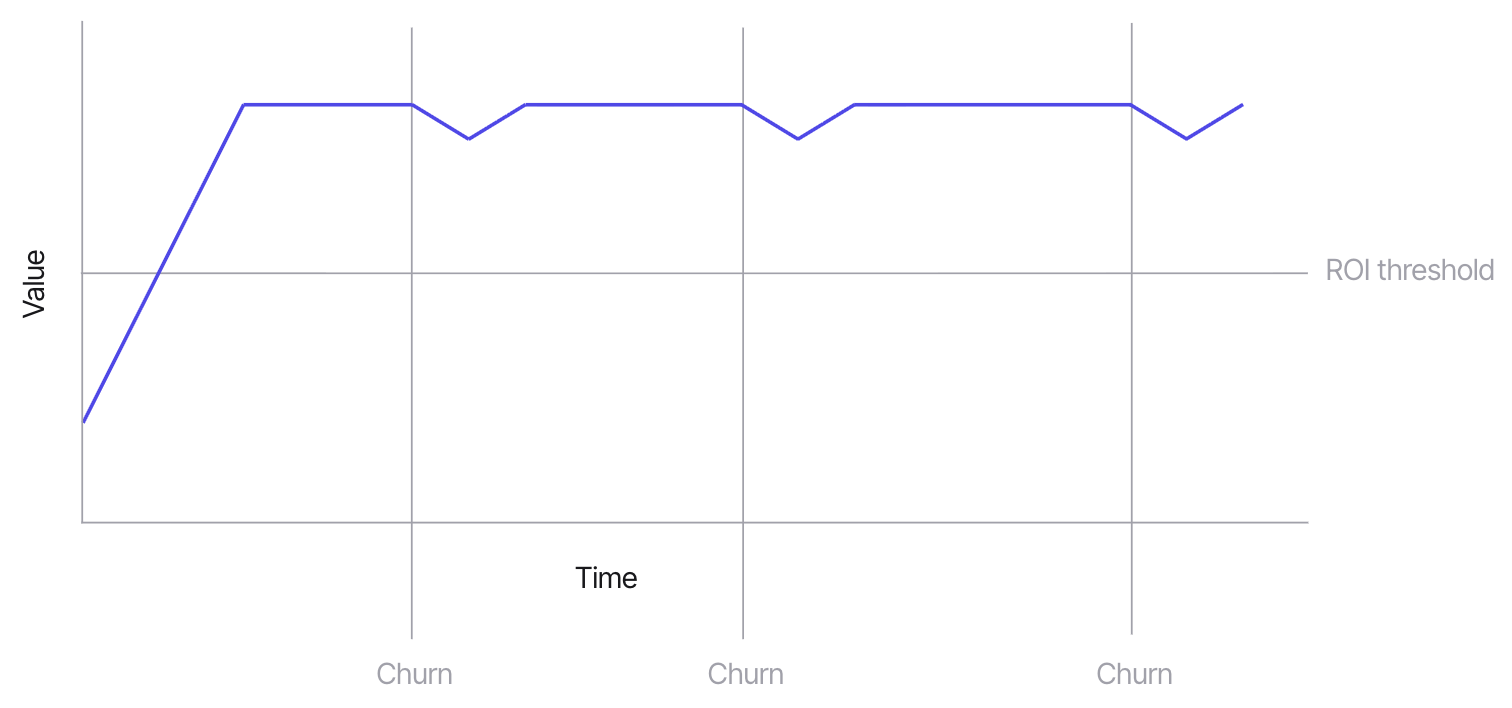
The second change is that triage and investigation happen before a human ever sees the alert. In a traditional SOC, the alert is the starting point of work. An analyst receives it, then pulls logs, checks user history, assesses permissions, and builds context. That process is the labor-intensive core of security operations, and it's the main thing MSSPs are paid to do.
AI SOC platforms do this work up front. Exaforce's Exabots, for instance, run a full triage pipeline on every alert, pulling in historical baselines, configuration data, business context, and prior resolutions. The vast majority of false positives get filtered out. What remains is a contextualized finding with a detailed explanation. A smaller team can handle a workload that previously required a much larger one, or an outsourced provider altogether.
This also changes who you hire first. Historically, you couldn’t start with just one hire. You needed a team of analysts and a manager to handle alert triage, investigation, and response workflows. Then you'd need more analysts. Maybe a detection engineer and SOAR expert for automation. The pyramid was wide at the base because the base was manual labor.
With AI handling triage, organizations are prioritizing detection engineers and threat hunters earlier in their security buildout, roles that leverage both institutional knowledge and the creative, investigative work that AI can't replicate yet. The tedious, repetitive work that caused burnout and drove people out of the field gets absorbed by the platform. People who get to do interesting work stick around longer.
We've seen this play out concretely. A smaller healthtech company is running a fully in-house SOC with a handful of security staff. Two years ago, that would have been impractical. They had the security expertise on staff, and with the AI SOC handling the operational load, they realized they simply didn't need an MSSP. The outputs were already triaged and contextualized. Their team could spend time on detection engineering and threat hunting instead of triaging noise.
Repatriation is a spectrum
The decision here is not "fire your MSSP" or "keep everything as-is." There are intermediate positions, and most organizations will land somewhere in the middle.
Some bring specific functions in-house while keeping others outsourced. Detection engineering is a common one to pull back as your internal team writes and tunes detections because they understand your environment best, while the service provider continues to handle operational triage and investigations. You get control over detection quality without needing to staff a full 24/7 operation.
Others flip the traditional MSSP model on its head. Instead of the MSSP running day-to-day operations, the in-house team handles the core workflow during business hours, and the MSSP picks up nights, weekends, and holidays. This works well when paired with an AI SOC platform that provides consistent, contextualized alerts regardless of who's on the receiving end.
The right model depends on your specifics. What expertise do you have on staff? What do those people actually want to spend their time on? How fast are you growing? Where does your workload spike unpredictably? There's an analogy one of our customers used that stuck with me. “You don't build enough parking spaces for the Super Bowl. You build for a normal day and figure out overflow for the peaks.”
How to repatriate the right way
If you're considering pulling operations back in-house, whether fully or partially, here's what we've seen work.
Define your mission before you pick your tools
Before changing anything, figure out what your SOC is for. What are your crown jewels? What are the threats that actually matter to your business? What are you choosing not to do right now? This sounds obvious, but a surprising number of teams skip it. They start hiring and buying tools before they've articulated what success looks like, and end up building a SOC that tries to cover everything and covers nothing well.
Audit what your MSSP is actually doing
Before you can decide what to bring in-house, you need an honest accounting of the value your provider is delivering. Are they resolving alerts, or forwarding them? Are detections tuned to your environment, or running out-of-the-box rules that fire indiscriminately? Are you getting fewer, higher-quality incidents, or the same volume of noise with a vendor logo on it? This audit often reveals that the functions providing the most value are different from what you expected.
Match your model to your people
One of our customers, a healthcare company with over 1,300 employees, had plenty of smart security people on staff. They chose to outsource their SOC staff to Exaforce's 24/7 coverage anyway. They chose to do this because their team was better oriented for other parts of security like product security, and felt it was best to outsource rather than staff round-the-clock SecOps monitoring. They kept their SOC in-house and used Exaforce to fill coverage gaps and handle the continuous triage work.
In contrast, the much smaller healthtech company with deep in-house SecOps expertise decided to run everything themselves. Same AI SOC platform, completely different operating model. Both were right for their situations.
Take 24/7 coverage seriously
This is consistently the top reason organizations keep an outsourced component, and for good reason. Staffing around-the-clock coverage requires either a large team or an international presence. AI handles much of the triage load continuously, but there are still situations where a human needs to make a call at 2 AM. If you don't have the team for that, keeping some level of MSSP engagement for off-hours is the pragmatic move.
Run things in parallel before you cut over
Repatriation is not a light switch. There's a period where you're building internal capability while still relying on external support. Use that overlap on purpose. Run your AI SOC platform alongside your MSSP for a defined window. Compare outputs. Identify gaps. Build your business context rules and let the system learn your environment. The institutional knowledge that makes an in-house SOC effective takes time to build up, even with AI accelerating the process. Rushing the transition is how you end up worse off than where you started.
Track the things that matter
The point of repatriation is better outcomes, not lower costs (though that may also happen). Track mean time to detect, mean time to respond, false positive rates, and how your analysts feel about the work they're doing. If your in-house operation isn't delivering better results than the MSSP was, either adjust your approach or reconsider the timing.
Where this is headed
Twelve months ago, if you had asked people who have spent their careers in SIEM and security operations whether a small startup could run its own SOC, the answer would have been an immediate no. The workloads were too heavy, the tooling required too much care and feeding, and the people problem was unsolvable at that scale.
That's no longer true, and the implications go beyond any individual organization's outsourcing decision. The talent shortage hasn't disappeared, but AI has reduced the number of people a SOC needs. Alert volumes are still massive, but intelligent triage means most alerts never reach a human. The operational burden has shifted from manual labor to system configuration and oversight.
For organizations that outsourced because they had no other option, it's worth asking whether that's still the case. The answer might still be yes. But it should be a deliberate choice, not a holdover from a time when the alternatives didn't exist.
And whatever you decide today, plan to revisit it. Your needs will change as you grow and as your team develops new capabilities. The SOC model that fits this year might not fit two years from now. That's fine. It was always supposed to be a spectrum.
If you're somewhere on that spectrum and want to figure out where you should be next, Exaforce can help. We run both an AI SOC platform and an MDR offering, and we've seen enough of both sides to give you a straight answer about what makes sense for your team. Or, if you want to hear the customer stories and decision frameworks behind this post in more detail, watch the full webinar recording.







