セキュリティインシデントがきちんとラベル付けされて届くことはめったにありません。
現代のクラウドおよびSaaS環境では、最も困難な状況は明らかな攻撃ではありません。これらは善意で行われる正当な行為のように見えますが、信頼できるアイデンティティを通じて、また誰も予想していなかった場所から予期せぬ形で現れるなど、危険な形で実行されています。こうした状況は、経験豊かなセキュリティチームでさえ立ち止まってしまう瞬間です。なぜなら、シグナルは実在するものの、その意図は不明瞭だからです。
これは、Exaforceの社内で実際に経験したインシデントです。この情報は匿名化され、正確であり、セキュリティチームが日々直面している課題を表しています。
迅速な検出とトリアージ
私たちは自分でシャンパンを飲むため、環境にはライブデータソースが取り込まれ、重大度の高いP1アラートがプラットフォームにリアルタイムで表示されます。Exaforceは、基礎となるシグナルをただちに単一の集約されたインシデントに関連付けて、MDRプロセスを設計どおりに実行しました。アラートはSLA内で優先順位付けされました。
その瞬間、観測可能なテレメトリーでは、「そうでないことが証明されるまでは違反として扱う」という姿勢が必要でした。その行為が悪意のある行為なのか、予想外の (しかし正当な) 第三者による行為なのかを判断するための十分な背景情報はまだ得られていませんでしたが、その兆候は侵害の兆候と一致していました。
人間による調査の前にプラットフォームが観察したこと
このアクティビティには、サードパーティのSaaS統合に関連する人間以外のアイデンティティが含まれていました。具体的には、GitHub App トークンを使用して JWT を生成し、公開されているドキュメントリポジトリから未知のラップトップにコンテンツを複製するためのアクセスを認証しました。これまで、この ID の動作は一貫していて予測可能でした。そのベースラインは突然変わりました。これにはプロダクションコードは含まれていませんでしたが、パターンが気になるため、それに応じて対処しています。幸いなことに、本番システムや機密性の高いプロダクションコードへのアクセスを防ぐための強力な管理を行っています。これらの保護手段は、このような事態が非公開のリポジトリを超えてエスカレートしないように設計されています。
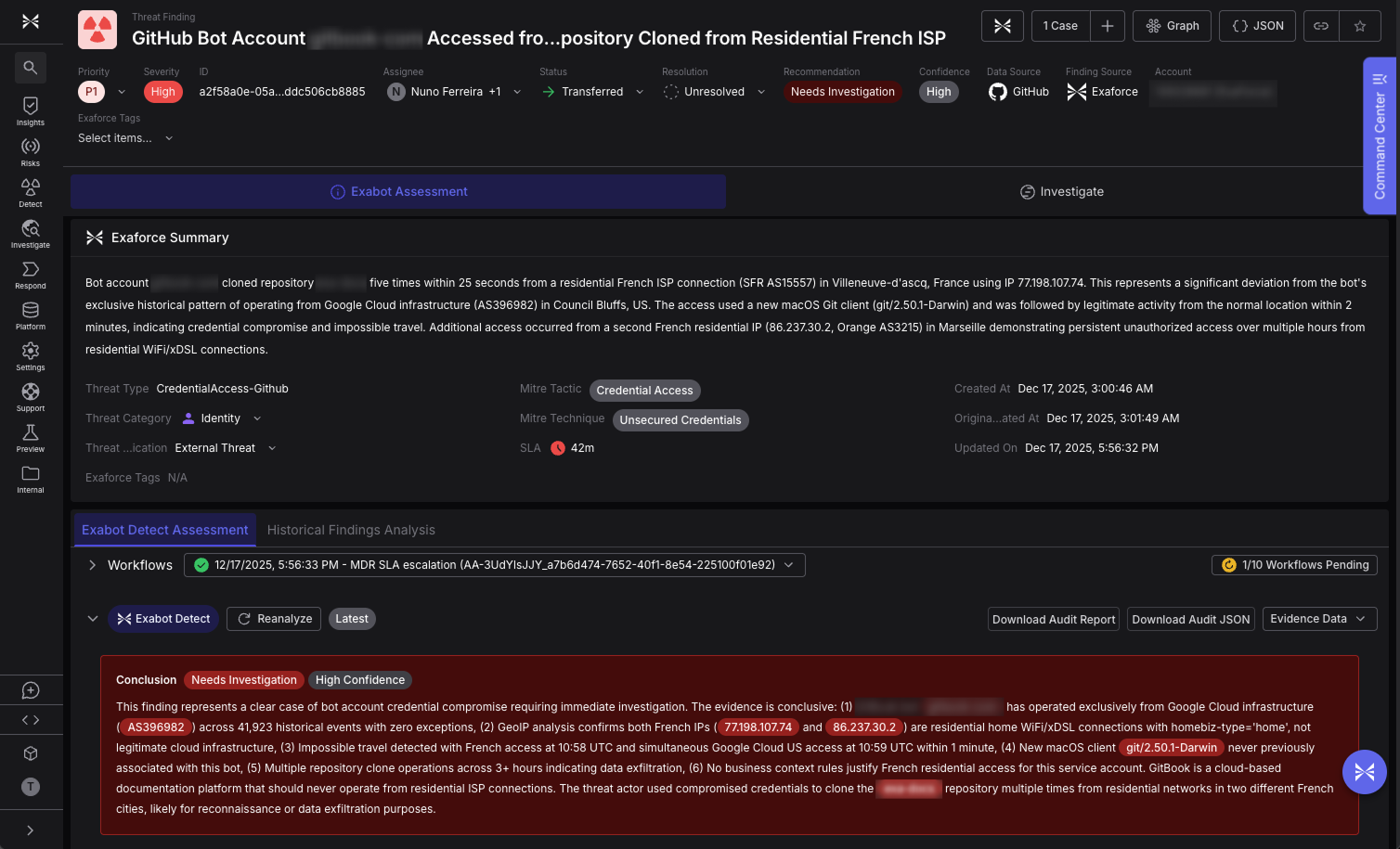
プラットフォームでは、短期間に複数の偏差が同時に発生していることが確認されました。
- アイデンティティは新しい国で運用を開始しました
- ソースネットワークを住宅用インターネットサービスプロバイダーに移行
- ユーザーエージェントがワークステーションベースの Git クライアントに変更されました
- 複数のフルリポジトリクローン操作が連続して発生しました
- 同時に、同じ ID が通常のクラウド環境から正常に動作し続けました。
個別に見ると、これらの信号はどれもまれではありません。地理的な異常にはノイズが多い。ネットワークは変化する。リポジトリへのアクセスは正当な場合があります。多くのセキュリティツールはこれらのイベントを個別に警告し、ほとんどのチームはそれらを調整する方法を学んでいます。ここで重要なのは同時実行性でした。
同じアイデンティティが 2 つの異なる環境で同時にアクティブでした。この重複により、ボット ID では移動が不可能なシナリオが生じ、リスク評価が変わりました。
このような状況で従来の検出アプローチが難しい理由
多くの環境では、このアクティビティによって複数の独立したアラートが生成されます。
- 地理的異常アラート
- ネットワークまたは自律システム番号 (ASN) の変更アラート
- リポジトリアクセスアラート
- サードパーティインテグレーションの警告の可能性があります
各アラートは個別に分離され、タイムスタンプが異なり、コンテキストも限られています。経験豊富なアナリストは、手動でシグナルを相互に関連づけ、タイムラインを再構築し、そのアクティビティが偶然、構成ミス、または妥協のどれを表しているのかを判断する必要があります。
そのプロセスには時間がかかります。時間はまさに攻撃者が頼りにするものであり、正当ではあるが予期しない活動が消費するものでもあります。
Exaforceがそれをどのように異なる方法で処理したか
このシグナルのグループから、Exaforceが生成しました 1 つの意味のある事件。
出発点としてのアイデンティティ行動
関係するIDは、人間ではなくボットとして分類されました。ボット ID が移動したり、住宅用ブロードバンドを使用したり、オペレーティングシステムを切り替えたり、インタラクティブに動作したりすることはありません。こうしたパターンが現れると、予想される行動から大きく逸脱していることになります。この行動の逸脱だけでも、インシデントをエスカレートさせるのに十分でした。
自動タイムライン再構築
エクサフォース・エージェンティックSOCプラットフォームは自動的に 一連のイベントを再構築しました、クラウドインフラストラクチャから発生する通常の自動アクティビティと、住宅ネットワークから発生する異常な手動アクティビティを区別し、同時使用であることが証明された一時的な重複を特定します。この再構築には、手動でのクエリ、ダッシュボード、ログステッチは不要でした。タイムラインはインシデントコンテキストの一部としてすぐに利用できました。
人間が理解できるようにAIを活用したトリアージ
このプラットフォームは、過去のベースライン、IDタイプ、アクセスパターン、環境状況をまとめて評価した結果、経験豊富なアナリストが状況をどのように推論するのかに合致したわかりやすい結論に達しました。それは、そうでないことが証明されるまで、侵害として扱うべきだということです。この枠組みにより、チームは完全な確実性を待たなくても断固として行動することができました。
Exaforce チームがどのように対応したか
インシデントの対象範囲が明確でコンテキスト化されていたため、対応は即時かつ測定的に行われました。短期間で P1 インシデントがレビューされ、 マネージド・ディテクション・アンド・レスポンス (MDR) チームが直接関与し、サードパーティとの統合は一時停止され、管理者認証は取り消され、ベンダーのセキュリティチームには法医学的証拠が記載された連絡がありました。この状況は数時間以内に解決しました。プラットフォームはすでにその作業を行っていたため、チームはシグナルが関連しているかどうかを議論する必要はありませんでした。
結果とそれがいまだに重要な理由
ベンダーとの共同調査の結果、この行為は違反ではなく、善意で危険なサポート行為であることが確認されました。あるSREは、ベンダー側のバグから回復するために、人間以外のIDを使用して手動でリポジトリを個人のラップトップに複製しました。その目的は迅速な対応とサービスの回復でしたが、ボット ID を使用し、事前に顧客に通知せずにベンダーの通常の本番インフラストラクチャの外で顧客コードにアクセスすることは不適切であり、有効な侵害指標が作成されました。
この特定のケースでは、リポジトリには公開プラットフォームドキュメントが含まれていたため、直接的な影響は最小限に抑えられました。しかし、内部アーキテクチャのドキュメント、ランブック、または機密データを含むリポジトリに同じパターンを適用すると、深刻な結果になる可能性がありました。より広範な教訓は、統制やコンテキストが欠けていると、正当で時間に追われている決定が妥協とどれほど簡単に区別がつかなくなるか、そして困難な状況であってもこれが起こってはならない理由についてです。
絶望的で曖昧な信号から決定的な検出まで
このインシデントは違反ではありませんが、シグナルは現実のものであり、リスクは現実のものでした。ツールが迅速かつ自信を持って区別できない場合、運と人間の英雄に頼っていることになります。Exaforce プラットフォームは、何が起きているのか、なぜ重要なのか、どれほど緊急なのかをリアルタイムで把握していました。それこそが、対応することと、準備を整えることの違いです。
Exaforceが複雑な信号を1つの一貫したインシデントに集約する方法を確認したい場合は、 エクサフォースでデモを予約する。





